Month: February 2024
The ransomware group LockBit told officials with Fulton County, Ga. they could expect to see their internal documents published online this morning unless the county paid a ransom demand. LockBit removed Fulton County’s listing from its victim shaming website this morning, claiming the county had paid. But county officials said they did not pay, nor…
Read MoreThe report points to the need for companies to patch open- source software and components, said Mike McGuire, senior software solutions manager at Synopsys Software Integrity Group. “It’s unpatched vulnerabilities that have led to some of the most significant data breaches,” he said. “Arguably, it’s the duty of these companies to address vulnerabilities, especially if…
Read MoreIn an era of unprecedented technological advancement, the adoption of AI continues to rise. However, with the proliferation of this powerful technology, a darker side is emerging. Increasingly, malicious actors are using AI to enhance every stage of an attack. Cybercriminals are using AI to support a multitude of malicious activities, ranging from bypassing algorithms that detect…
Read MoreCISA and Partners Release Advisory on Threat Actors Exploiting Ivanti Connect Secure and Policy Secure Gateways Vulnerabilities | CISA
by nlqip
Today, CISA and the following partners released joint Cybersecurity Advisory Threat Actors Exploit Multiple Vulnerabilities in Ivanti Connect Secure and Policy Secure Gateways: Federal Bureau of Investigation (FBI) Multi-State Information Sharing & Analysis Center (MS-ISAC) Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) United Kingdom National Cyber Security Centre (NCSC-UK) Canadian Centre for Cyber…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2023-29360 Microsoft Streaming Service Untrusted Pointer Dereference Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of…
Read MoreToday, CISA, the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) released a joint Cybersecurity Advisory (CSA), #StopRansomware: Phobos Ransomware, to disseminate known tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs), which are from incident response investigations tied to Phobos ransomware activity from as recently as February,…
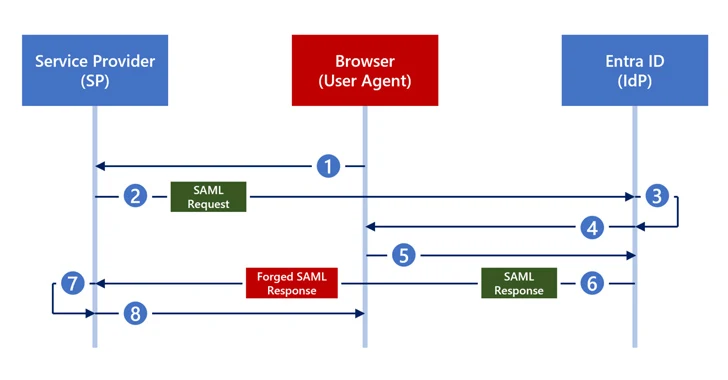
Read MoreFeb 29, 2024NewsroomThreat Intelligence / Cyber Threat Cybersecurity researchers have disclosed a new attack technique called Silver SAML that can be successful even in cases where mitigations have been applied against Golden SAML attacks. Silver SAML “enables the exploitation of SAML to launch attacks from an identity provider like Entra ID against applications configured to…
Read MoreCISA released two Industrial Control Systems (ICS) advisories on February 29, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review the newly released ICS advisories for technical details and mitigations. Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreSUMMARY Note: This joint Cybersecurity Advisory (CSA) is part of an ongoing #StopRansomware effort to publish advisories for network defenders that detail various ransomware variants and ransomware threat actors. These #StopRansomware advisories include recently and historically observed tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to help organizations protect against ransomware. Visit stopransomware.gov to see…
Read MoreWhat’s happened? The US government warned healthcare organizations about the risk of being targeted by the ALPHV BlackCat ransomware after a surge in attacks. I thought ALPHV BlackCat had been taken down by the cops? Well remembered. Shortly before Christmas, the US Department of Justice (DOJ) announced that it had disrupted the gang’s operations and…
Read MoreRecent Posts
- Secure Boot no more? Leaked key, faulty practices put 900 PC/server models in jeopardy
- Crooks Bypassed Google’s Email Verification to Create Workspace Accounts, Access 3rd-Party Services – Krebs on Security
- Friday Squid Blogging: Sunscreen from Squid Pigments
- Here Are The 8 Biggest IT Services M&A Deals In Q2 2024
- Crypto exchange Gemini discloses third-party data breach