Month: February 2024
CISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2024-1709 ConnectWise ScreenConnect Authentication Bypass Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited…
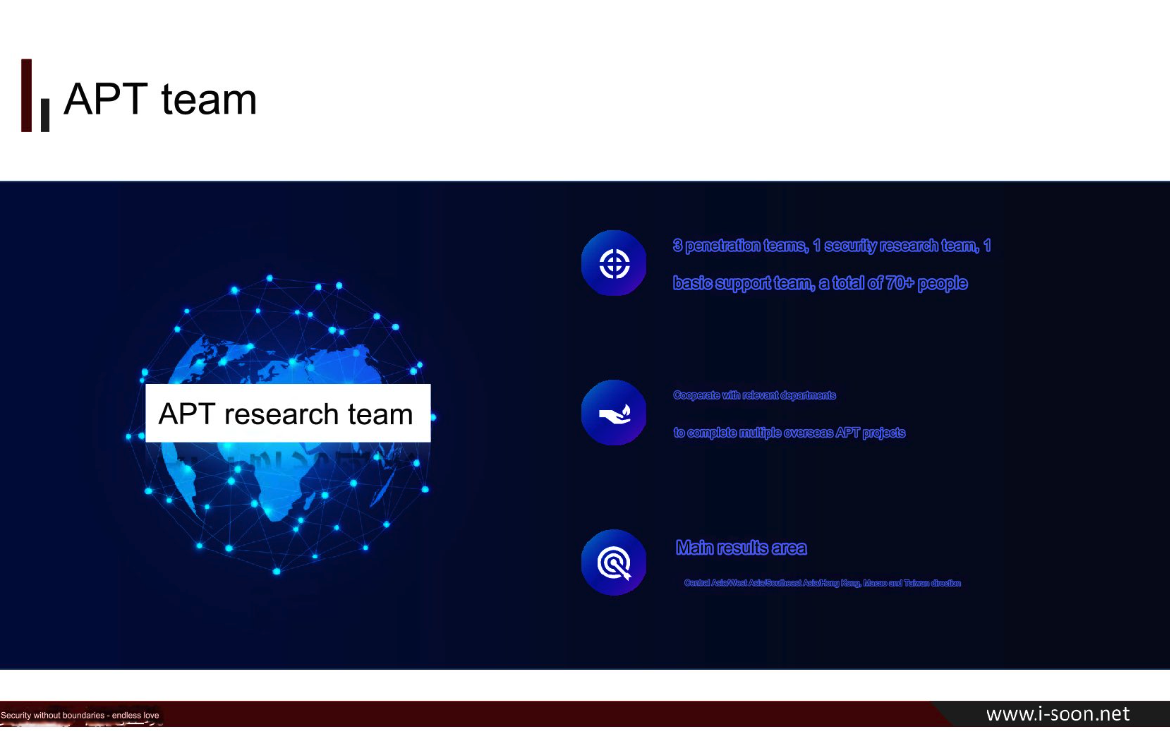
Read MoreA new data leak that appears to have come from one of China’s top private cybersecurity firms provides a rare glimpse into the commercial side of China’s many state-sponsored hacking groups. Experts say the leak illustrates how Chinese government agencies increasingly are contracting out foreign espionage campaigns to the nation’s burgeoning and highly competitive cybersecurity…
Read MoreFostering a domestic crane industry Given China’s dominance in the global supply of port cranes, the Biden administration seeks to revive a US-based crane industry. “The Administration continues to deliver for the American people by rebuilding the US’s industrial capacity to produce port cranes with trusted partners,” the White House said in its fact sheet.…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In our digitized world, online banking has become an integral part of managing your finances, offering unparalleled convenience. However, with this convenience comes…
Read MoreFeb 22, 2024NewsroomMalware / Cyber Espionage An installer for a tool likely used by the Russian Consular Department of the Ministry of Foreign Affairs (MID) has been backdoored to deliver a remote access trojan called Konni RAT (aka UpDog). The findings come from German cybersecurity company DCSO, which linked the activity as originating from the…
Read MoreThreat actors, frequently frustrated by improved enterprise security systems, increased their efforts to compromise credentials in 2023, according to CloudStrike’s 10th annual global threat report released Wednesday. “Threat actors are running into EDR products out there that are making it difficult for them. It’s difficult for them to bring their tools in and use them…
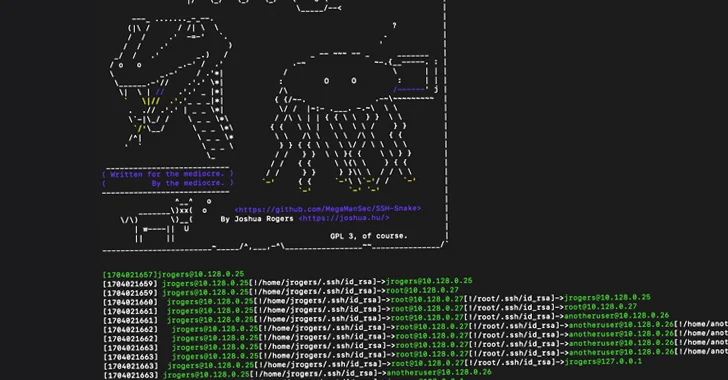
Read MoreFeb 22, 2024NewsroomNetwork Security / Penetration Testing A recently open-sourced network mapping tool called SSH-Snake has been repurposed by threat actors to conduct malicious activities. “SSH-Snake is a self-modifying worm that leverages SSH credentials discovered on a compromised system to start spreading itself throughout the network,” Sysdig researcher Miguel Hernández said. “The worm automatically searches…
Read MoreIn the past 2 years, we have observed a significant surge in hacktivism activity due to ongoing wars and geopolitical conflicts in various regions. Since the war against Ukraine began, we have witnessed a notable mobilization of non-state and state-backed actors alike, forming new groups or joining existing hacker collectives. We understand hacktivism as a…
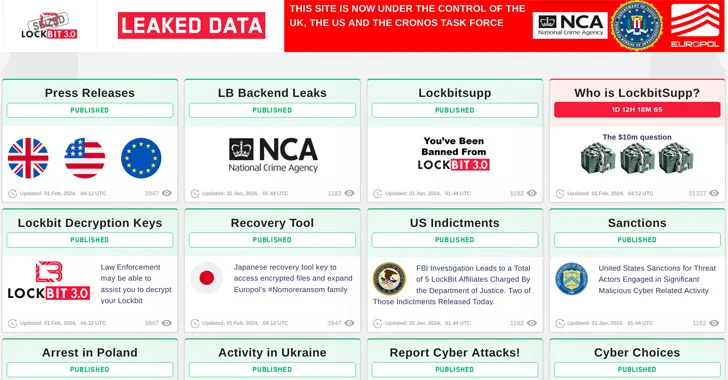
Read MoreThe U.S. State Department has announced monetary rewards of up to $15 million for information that could lead to the identification of key leaders within the LockBit ransomware group and the arrest of any individual participating in the operation. “Since January 2020, LockBit actors have executed over 2,000 attacks against victims in the United States,…
Read MoreThe willingness of competitors to use cyber operations to generate strategic effects is dictated by four institutional factors: Connectivity: Competitors are motivated by the degree of connectivity that exists to link them to adversaries. Given the ubiquity of cyber and cyber-physical systems today, this factor is consistently high. Vulnerability: Competitors are motivated by perceived…
Read MoreRecent Posts
- Tenable Chairman and CEO Amit Yoran Has Died
- Tenable Announces the Passing of Chairman and CEO Amit Yoran
- Opinion: Why Nvidia, MediaTek May Enter The PC CPU Market Soon
- Microsoft VP Of Silicon Engineering Jumps To Google Cloud To Head Chip Technology And Manufacturing
- 10 Cloud Startup Companies To Watch In 2025