Month: February 2024
The fact that over 10,000 organizations appeared on leak sites in 2023, the most since 2019, is a microcosm of the growing ransomware menace. Leak sites are a name-and-shame tactic used by ransomware operators to extort ransom fees from organizations that refuse to pay. Leak sites do not reveal the full scope of impact from…
Read MoreBlackFog has been recording publicly disclosed ransomware attacks since 2020, and in 2023 we also began recording the number of undisclosed attacks, those that are listed on the data leak sites and dark web by the attackers. The 2023 ransomware attack report summarizes the key findings from 2023 compared to previous years. 2023 was a…
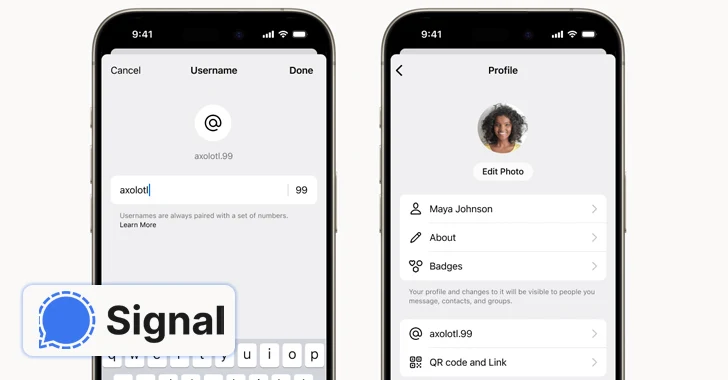
Read MoreFeb 21, 2024NewsroomSecure Communication / Anonymity End-to-end encrypted (E2EE) messaging app Signal said it’s piloting a new feature that allows users to create unique usernames (not to be confused with profile names) and keep the phone numbers away from prying eyes. “If you use Signal, your phone number will no longer be visible to everyone…
Read MoreWe explore the Badbox and Peachpit malware on Android, which granted illegitimate users backdoor access to Android devices and home networks. It details how the Triada mobile trojan formed the basis for Badbox, infecting over 74,000 devices by modifying Android OS and remaining hidden. Does malware come to mind when you think about streaming devices…
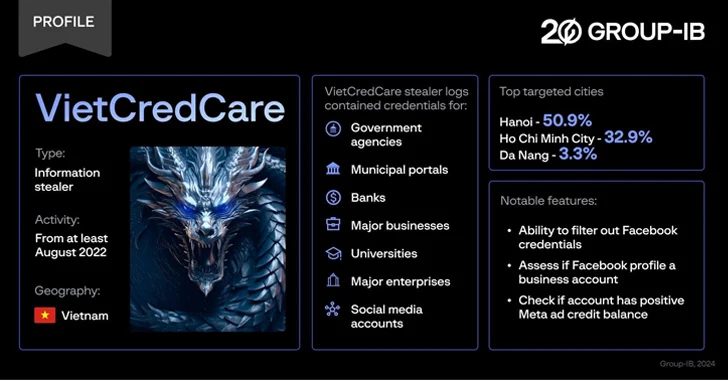
Read MoreFeb 21, 2024NewsroomMalware / Cyber Threat Facebook advertisers in Vietnam are the target of a previously unknown information stealer dubbed VietCredCare at least since August 2022. The malware is “notable for its ability to automatically filter out Facebook session cookies and credentials stolen from compromised devices, and assess whether these accounts manage business profiles and…
Read MoreA staggering 91% of ransomware attacks now involve data exfiltration, typically to servers in China or Russia, marking a major evolution beyond file encryption. This exponential rise in exfiltration creates endless extortion potential, sparks legal action, allows tailored demands, and fuels future breaches. According to our 2023 Annual Ransomware Report, 91% of all ransomware incidents…
Read MoreFeb 21, 2024NewsroomActive Directory / Vulnerability VMware is urging users to uninstall the deprecated Enhanced Authentication Plugin (EAP) following the discovery of a critical security flaw. Tracked as CVE-2024-22245 (CVSS score: 9.6), the vulnerability has been described as an arbitrary authentication relay bug. “A malicious actor could trick a target domain user with EAP installed…
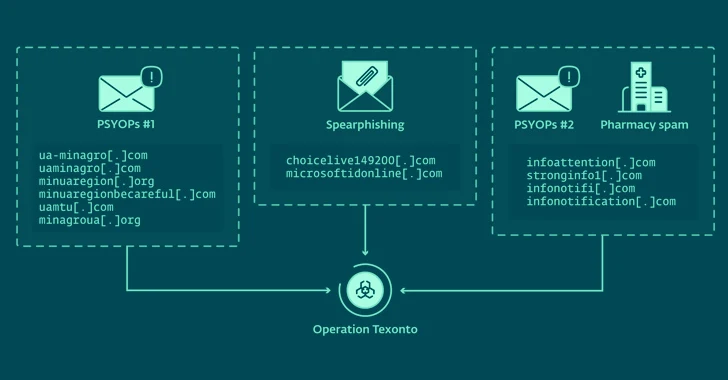
Read MoreFeb 21, 2024NewsroomPhishing Attack / Information Warfare Cybersecurity researchers have unearthed a new influence operation targeting Ukraine that leverages spam emails to propagate war-related disinformation. The activity has been linked to Russia-aligned threat actors by Slovak cybersecurity company ESET, which also identified a spear-phishing campaign aimed at a Ukrainian defense company in October 2023 and…
Read MoreFor some internal classified work, the NSA also pushes multiple layers of encryption. Their guidelines for using commercially available software in classified environments frequently encourage using multiple “layers” of independent packages. How much security does hybrid encryption provide? One of the biggest debates is how much security hybridization offers. Much depends on the details and…
Read MoreAdvisory ID: VMSA-2024-0004 CVSSv3 Range: 6.7 Issue Date: 2024-02-20 Updated On: 2024-02-20 (Initial Advisory) CVE(s): CVE-2024-22235 Synopsis: VMware Aria Operations updates address local privilege escalation vulnerability. (CVE-2024-22235) Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreRecent Posts
- The Most Scary, Interesting, and Important Stories of 2024
- Choosing the Right CNAPP: Six Considerations for Mid-Sized Enterprises
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Vulnerability Summary for the Week of December 23, 2024 | CISA
- Navigating the SEC’s Cybersecurity Disclosure Rules: One Year On