Month: February 2024
At least two different suspected China-linked cyber espionage clusters, tracked as UNC5325 and UNC3886, have been attributed to the exploitation of security flaws in Ivanti Connect Secure VPN appliances. UNC5325 abused CVE-2024-21893 to deliver a wide range of new malware called LITTLELAMB.WOOLTEA, PITSTOP, PITDOG, PITJET, and PITHOOK, as well as maintain persistent access to compromised…
Read MoreU.S. President Joe Biden has issued an Executive Order that prohibits the mass transfer of citizens’ personal data to countries of concern. The Executive Order also “provides safeguards around other activities that can give those countries access to Americans’ sensitive data,” the White House said in a statement. This includes sensitive information such as genomic…
Read MoreSmashing Security podcast #361: Wireless charging woe, AI romance apps, and ransomware revisited
by nlqip
Your smartphone may be toast – if you use a hacked wireless charger, we take a closer look at the latest developments in the unfolding LockBit ransomware drama, and Carole dips her toe into online AI romance apps. All this and much much more is discussed in the latest edition of the “Smashing Security” podcast…
Read MoreVOLTZITE relies heavily on living-off-the-land techniques and hands-on post-compromise actions with the goal of expanding their access from the IT network perimeter to the OT network. The group is believed to be in operation since at least 2021 and has targeted critical infrastructure entities in Guam, the United States, and other countries with a focus…
Read MoreCovered persons: The program will be defined categorically to include certain classes of entities and individuals subject to the jurisdiction, direction, ownership, or control of countries of concern, if data to these persons will place that data within the reach of the countries of concern. The EO defines four categories of covered persons: “An entity…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-024 DATE(S) ISSUED: 02/28/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Chrome, which could allow for arbitrary code execution. Successful exploitation of these vulnerabilities could allow for arbitrary code execution in the context of the logged on user. Depending on the privileges associated with the user an attacker could then install…
Read MoreMatthew Perry’s official Twitter account was hijacked by scammers this week who attempted to solicit donations from well-meaning fans of the much-loved late actor. The post, which has since been removed from Perry’s Twitter account, asked for cryptocurrency donations “to support our mission in battling addiction.” The tweet claimed to be signed by “The Matthew…
Read MoreToday, CISA released a Resource Guide for Cybersecurity Clinics to outline ways CISA can partner with and support cybersecurity clinics and their clients. University cybersecurity clinics train students from diverse backgrounds and academic expertise to strengthen the digital defenses of non-profits, hospitals, municipalities, small businesses, and other under-resourced organizations. They can help address the national…
Read MoreGraham Cluley Security News is sponsored this week by the folks at Cynet. Thanks to the great team there for their support! George Tubin, Director of Product Strategy, Cynet Thorough, independent tests are a vital resource as cybersecurity leaders and their teams evaluate vendors’ abilities to guard against increasingly sophisticated threats to their organization. And…
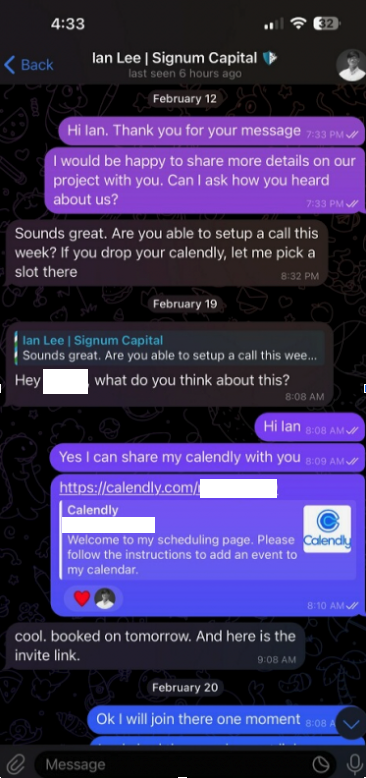
Read MoreMalicious hackers are targeting people in the cryptocurrency space in attacks that start with a link added to the target’s calendar at Calendly, a popular application for scheduling appointments and meetings. The attackers impersonate established cryptocurrency investors and ask to schedule a video conference call. But clicking the meeting link provided by the scammers prompts…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA