Top 10 scams targeting seniors – and how to stay safe
by nlqip

Scams
The internet can be a wonderful place. But it’s also awash with fraudsters targeting people who are susceptible to fraud.
06 Mar 2024
•
,
5 min. read

We’re all getting older. That’s good news for digital fraudsters, who see rich pickings to be had in a rapidly ageing society. They’re increasingly targeting senior citizens because they suspect these targets to have more money to steal, but potentially less digital savvy to spot the early warning signs of a scam. In 2022, $3.1 billion in cybercrime losses were reported to the FBI by the over-60s, on the back of 88,262 incidents. Although that represented an 82% year-on-year increase, many more cases will not have been reported.
The impact of such scams can be devastating if you’ve already retired and have no source of income to replace savings lost to fraudsters. So if you’re a senior citizen, or a concerned relative, read on.
10 scams to watch out for
The internet can, of course, be a wonderful place. But it’s also awash with bad people trying to steal your personal information and money. Here are some of the most common schemes:
1. Phishing
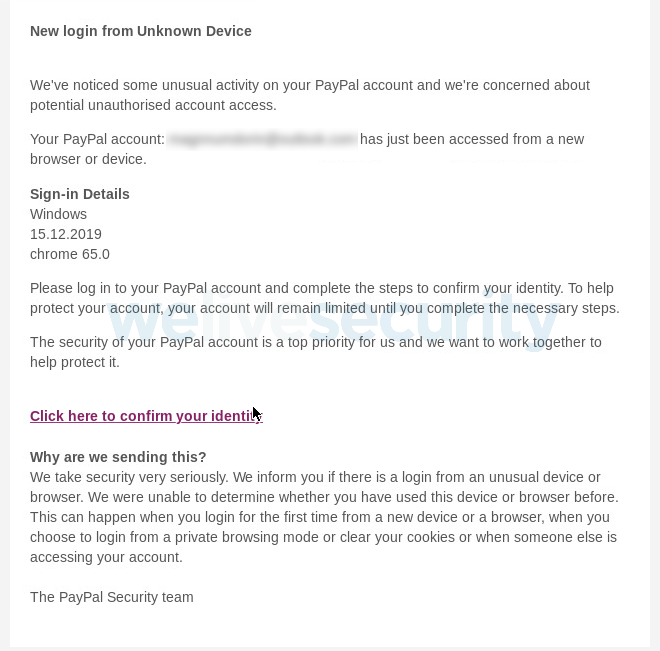
Let’s start with a threat that is a scourge of the modern internet: phishing. A phishing email or phone/social media message will arrive unsolicited. The scammer impersonates a legitimate entity requesting you supply information such as account log-ins, or click on a link/open an attachment. The former could enable them to hijack your accounts, while the latter may trigger a malware download designed to steal more data or lock down your computer.
2. Romance scams
Romance scams made $734 billion for fraudsters in 2022, the FBI says. Scammers will create fake profiles on dating sites, befriend lonely hearts and build a rapport, with the aim of extracting as much money as possible. Typical stories are that they need money for medical bills or to travel to see their sweetheart. Needless to say they will always find an excuse not to appear on a video call or meet in person.
3. Medicare/healthcare
The scammer impersonates a Medicare representative with the aim of eliciting personal and medical information that can be sold on to others to commit health insurance fraud. They may do this on email, by phone or even in person.
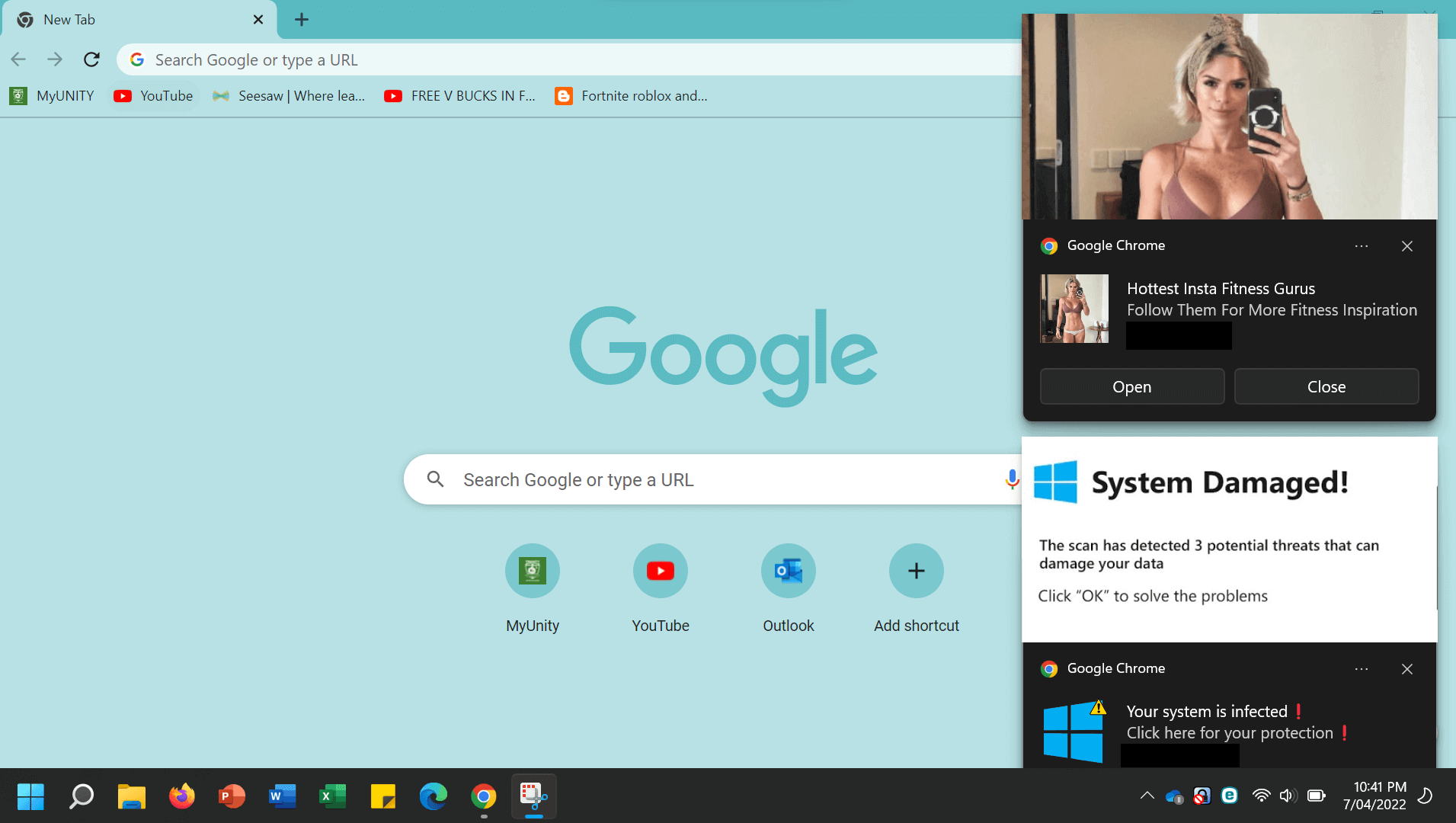
4. Tech support
In one of the oldest phone-based scams, the fraudster impersonates a legitimate entity like a tech company or telco provider, telling you there’s something wrong with your PC. This might happen out of the blue, or you might be prompted to call a ‘helpline’ after a harmless but worrying pop-up appears on your computer. The scammer may trick you into providing them access to the machine. They’ll try and find a way of making money out of you; for unnecessary ‘protection’ or ‘upgrades’ of the machine, or by stealing financial information from it.
5. Online shopping fraud
Scammers create legitimate-looking online stores and then attract users to visit them via phishing emails or unsolicited texts or social media messages. Items are often marked down with incredible offers. However, products are either counterfeit, stolen or non-existent and the real goal is to steal your card details.
6. Robocalls
Robocalls rely on automated technology to nuisance call large numbers of recipients at once. A pre-recorded message may be used to offer free or heavily discounted goods. Or it could be used to scare the recipient into responding, such as telling them they are the subject of an impending lawsuit. If you respond, the scammers will try to obtain your personal and financial information.
7. Government impersonation
Like tech support scams, these are usually performed by call centers based in south Asia. Combined losses topped $1 billion in 2022. In this version, the scammer will call pretending to be from the IRS, Medicare or other government body demanding unpaid taxes or other payments. They will aggressively warn that non-payment could lead to arrest or other penalties.
8. Lottery scams
A fraudster calls out of the blue claiming you’ve won a lottery and all you need to do to reclaim your winnings is send a small processing fee or tax up front. Of course, there is no prize and your money will disappear.

9. Grandparent scam
A scammer calls you up unannounced pretending to be a relative in jeopardy. They’ll typically start by saying something like “Hi Grandma, do you know who this is?” and then proceed with a tale of woe designed to persuade you into parting with cash to help them. Usually they’ll request a money transfer, gift cards or payment via a cash app. They may ask that you keep everything a secret. In some variations on this theme, the scammer pretends to be an arresting police officer, doctor or lawyer trying to help the grandchild. Advances in AI software known as deepfakes may even enable them to mimic the voice of your grandchild more accurately to perpetrate what has come to be called “virtual kidnapping scams”.
10. Investment scams
The highest earner for cybercriminals in 2022, making over $3.3 billion, this category refers to get-rich-quick schemes that promise low risk and guaranteed returns, often through cryptocurrency investments. In reality, the whole scheme is built on sand.
How to stay safe
We’ve written about this before and although the scammers’ tactics may change, best practice advice remains pretty consistent. Remember the following to stay safe:
- If an offer is too good to be true it usually is.
- Treat any unsolicited contact with suspicion. If you want to reply, never respond directly to a message. Instead, Google the sending institution and call or email separately to confirm.
- Stay calm, even when harangued on the phone. And don’t give out any personal information.
- Don’t trust Caller ID as it can be faked.
- Use multi-factor authentication on your accounts to mitigate the threat of someone stealing your logins.
- Never send money via wire transfer, payment apps, gift cards or cryptocurrency, as there’s no way of requesting it back in the advent of fraud.
- Don’t click on links or open attachments in emails/texts/social media messages.
What to do if you’ve been scammed
If you think you might have been scammed, get in touch with local police, your local bank (if financial details were involved) or even (in the US) Adult Protective Services. It is also a good idea to reset your passwords if you’ve handed them over to a potential scammer. In the US, consider reporting the case to the FTC.
If you read this and have elderly relatives you’re concerned about, take the time to have a chat about common scams. Technology can often be intimidating if we don’t fully understand it. But it’s that reluctance to find out more – and our reluctance to tell anyone about being scammed – that fraudsters take advantage of. Let’s not let them have the last laugh.
Source link
ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
