Month: March 2024
Last year ESET published a blogpost about AceCryptor – one of the most popular and prevalent cryptors-as-a-service (CaaS) operating since 2016. For H1 2023 we published statistics from our telemetry, according to which trends from previous periods continued without drastic changes. However, in H2 2023 we registered a significant change in how AceCryptor is used.…
Read More2023 was a year that saw ransomware continuously break records, and while the usual suspects LockBit and BlackCat represented 38% of all reported attacks, we also saw around 29 new ransomware gangs began operations last year. Notable newcomers in 2023 included Akira, who were responsible for over 50 attacks and Rhysida who made headlines with…
Read MoreHundreds of US employees have been targeted in a new email attack that uses accounting lures to distribute malicious documents that deploy a malicious remote access tool known as NetSupport RAT. The attackers use a combination of detection evasion techniques including Office Object Linking and Embedding (OLE) template manipulation and injection as well as Windows…
Read MoreMar 21, 2024NewsroomThreat Intelligence / Malware The Russia-linked threat actor known as Turla infected several systems belonging to an unnamed European non-governmental organization (NGO) in order to deploy a backdoor called TinyTurla-NG. “The attackers compromised the first system, established persistence and added exclusions to antivirus products running on these endpoints as part of their preliminary…
Read MoreMar 21, 2024NewsroomSoftware Security / Open Source New research has discovered over 800 packages in the npm registry which have discrepancies from their registry entries, out of which 18 have been found to exploit a technique called manifest confusion. The findings come from cybersecurity firm JFrog, which said the issue could be exploited by threat…
Read MoreMar 21, 2024NewsroomThreat Intelligence / Vulnerability Cybersecurity researchers have shed light on a tool referred to as AndroxGh0st that’s used to target Laravel applications and steal sensitive data. “It works by scanning and taking out important information from .env files, revealing login details linked to AWS and Twilio,” Juniper Threat Labs researcher Kashinath T Pattan…
Read MoreCISA, FBI, and MS-ISAC Release Update to Joint Guidance on Distributed Denial-of-Service Techniques | CISA
by nlqip
Today, CISA, the Federal Bureau of Investigation (FBI), and the Multi-State Information Sharing and Analysis Center (MS-ISAC) released an updated joint guide, Understanding and Responding to Distributed Denial-Of-Service Attacks, to address the specific needs and challenges faced by organizations in defending against DDoS attacks. The guidance now includes detailed insight into three different types of…
Read More“Implementations of UDP application protocol are vulnerable to network loops,” according to the vulnerability’s NVD entry. “An unauthenticated attacker can use maliciously crafted packets against a vulnerable implementation that can lead to Denial of Service (DOS) and/or abuse of resources.” CISPA researchers explained the attack loop can be initiated by sending one single IP-spoofed error…
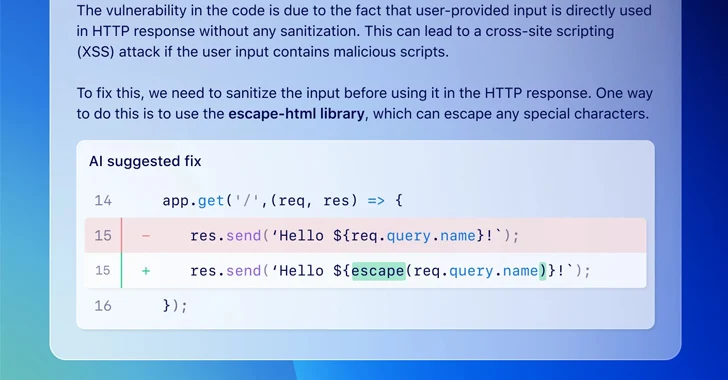
Read MoreMar 21, 2024NewsroomMachine Learning / Software Security GitHub on Wednesday announced that it’s making available a feature called code scanning autofix in public beta for all Advanced Security customers to provide targeted recommendations in an effort to avoid introducing new security issues. “Powered by GitHub Copilot and CodeQL, code scanning autofix covers more than 90%…
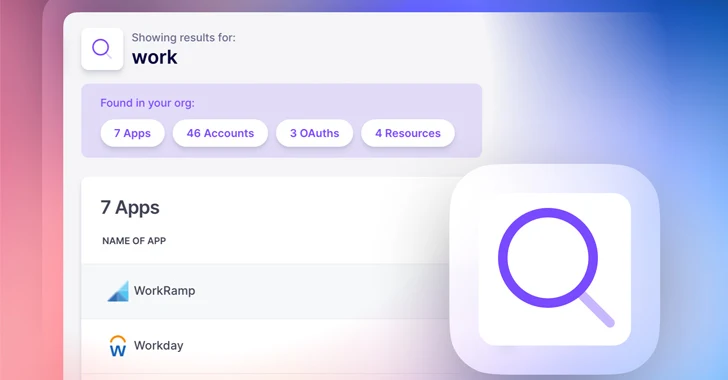
Read MoreIn today’s digital-first business environment dominated by SaaS applications, organizations increasingly depend on third-party vendors for essential cloud services and software solutions. As more vendors and services are added to the mix, the complexity and potential vulnerabilities within the SaaS supply chain snowball quickly. That’s why effective vendor risk management (VRM) is a critical strategy…
Read MoreRecent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’