Month: March 2024
The need for reliable intelligence is pressing in threat hunting and emerging AI technologies can fulfill that to a good extent, according to a Censys study. The study included US and Europe-based organizations across industries and noted that current threat-hunting practices are “as much an art as science” and can use a discipline of common,…
Read MoreAutomakers Are Sharing Driver Data with Insurers without Consent Kasmir Hill has the story: Modern cars are internet-enabled, allowing access to services like navigation, roadside assistance and car apps that drivers can connect to their vehicles to locate them or unlock them remotely. In recent years, automakers, including G.M., Honda, Kia and Hyundai, have started…
Read MoreMar 14, 2024NewsroomCyber Espionage / Malware The Russian-speaking cybercrime group called RedCurl is leveraging a legitimate Microsoft Windows component called the Program Compatibility Assistant (PCA) to execute malicious commands. “The Program Compatibility Assistant Service (pcalua.exe) is a Windows service designed to identify and address compatibility issues with older programs,” Trend Micro said in an analysis…
Read MoreBeing a CISO is a balancing act: ensuring organizations are secure without compromising users’ productivity. This requires taking multiple elements into consideration, like cost, complexity, performance and user experience. CISOs around the globe use Cato SSE 360, as part of the Cato SASE Cloud platform to balance these factors without compromise. This article details how…
Read MoreAn Instant Guide on How to Install SSL Certificate on Apache Server Securing your website is like having a lock on your network that protects it from cyberattacks. SSL/TLS encryption is a communication lock between a web server and a browser. These encryptions ensure that sensitive information, such as passwords, and financial and personal data,…
Read MoreCheyenne, WY – March 14th, 2024 – BlackFog, the leader in ransomware protection and anti data exfiltration, today announces its wins in three categories at the 20th Annual 2024 Globee Awards. The Globee® Cybersecurity Awards, a leading authority in recognizing business excellence globally, has honored BlackFog for outstanding innovation and effectiveness in cybersecurity. The Globee Cybersecurity…
Read MoreMar 14, 2024NewsroomCyber Threat / Malware The threat actor known as Blind Eagle has been observed using a loader malware called Ande Loader to deliver remote access trojans (RATs) like Remcos RAT and NjRAT. The attacks, which take the form of phishing emails, targeted Spanish-speaking users in the manufacturing industry based in North America, eSentire…
Read MoreIn addition to having an inventory of existing tools in use, there also should be a process to onboard and offboard future tools and services from the organizational inventory securely. AI security and privacy training It’s often quipped that “humans are the weakest link,” however that doesn’t need to be the case if an organization…
Read MoreMar 14, 2024The Hacker NewsVulnerability / Network Security Fortinet has warned of a critical security flaw impacting its FortiClientEMS software that could allow attackers to achieve code execution on affected systems. “An improper neutralization of special elements used in an SQL Command (‘SQL Injection’) vulnerability [CWE-89] in FortiClientEMS may allow an unauthenticated attacker to execute…
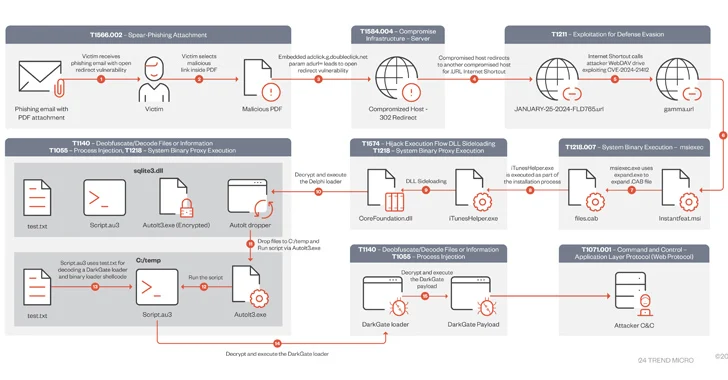
Read MoreMar 14, 2024NewsroomMalware / Cyber Attack A DarkGate malware campaign observed in mid-January 2024 leveraged a recently patched security flaw in Microsoft Windows as a zero-day using bogus software installers. “During this campaign, users were lured using PDFs that contained Google DoubleClick Digital Marketing (DDM) open redirects that led unsuspecting victims to compromised sites hosting…
Read MoreRecent Posts
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day
- QNAP pulls buggy QTS firmware causing widespread NAS issues
- N-able Exec: ‘Cybersecurity And Compliance Are A Team Sport’
- Hackers breach US firm over Wi-Fi from Russia in ‘Nearest Neighbor Attack’