Month: March 2024
The Russian state-sponsored attackers who breached the corporate email accounts of several senior Microsoft employees and security team members in November have been using information stolen from those mailboxes to access internal systems. Some of the emails also included secrets that Microsoft exchanged with customers and which could potentially be used in further attacks, the…
Read MoreBotnets have been in existence for nearly two decades. Yet despite being a longstanding and widely known threat, they still have the power to wreak havoc on an organization’s networks, and often do so successfully while evading detection. The majority of contemporary malware families have set up botnets for command and control (C2) connections. It…
Read MoreEssays from the Second IWORD The Ash Center has posted a series of twelve essays stemming from the Second Interdisciplinary Workshop on Reimagining Democracy (IWORD 2023). Aviv Ovadya, Democracy as Approximation: A Primer for “AI for Democracy” Innovators Kathryn Peters, Permission and Participation Claudia Chwalisz, Moving Beyond the Paradigm of “Democracy”: 12 Questions Riley Wong,…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog…
Read MoreApple released security updates to address vulnerabilities in Safari, macOS, watchOS, tvOS, and visionOS. A cyber threat actor could exploit some of these vulnerabilities to take control of an affected system. CISA encourages users and administrators to review the following advisories and apply the necessary updates: Source link ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreESET researchers discovered a cyberespionage campaign that, since at least September 2023, has been victimizing Tibetans through a targeted watering hole (also known as a strategic web compromise), and a supply-chain compromise to deliver trojanized installers of Tibetan language translation software. The attackers aimed to deploy malicious downloaders for Windows and macOS to compromise website…
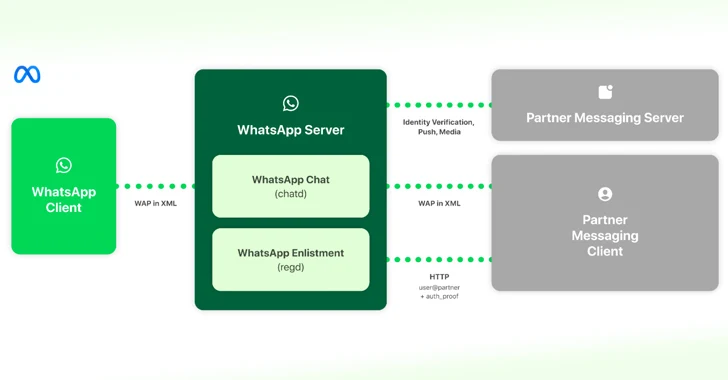
Read MoreMar 08, 2024NewsroomInteroperability / Encryption Meta has offered details on how it intends to implement interoperability in WhatsApp and Messenger with third-party messaging services as the Digital Markets Act (DMA) went into effect in the European Union. “This allows users of third-party providers who choose to enable interoperability (interop) to send and receive messages with…
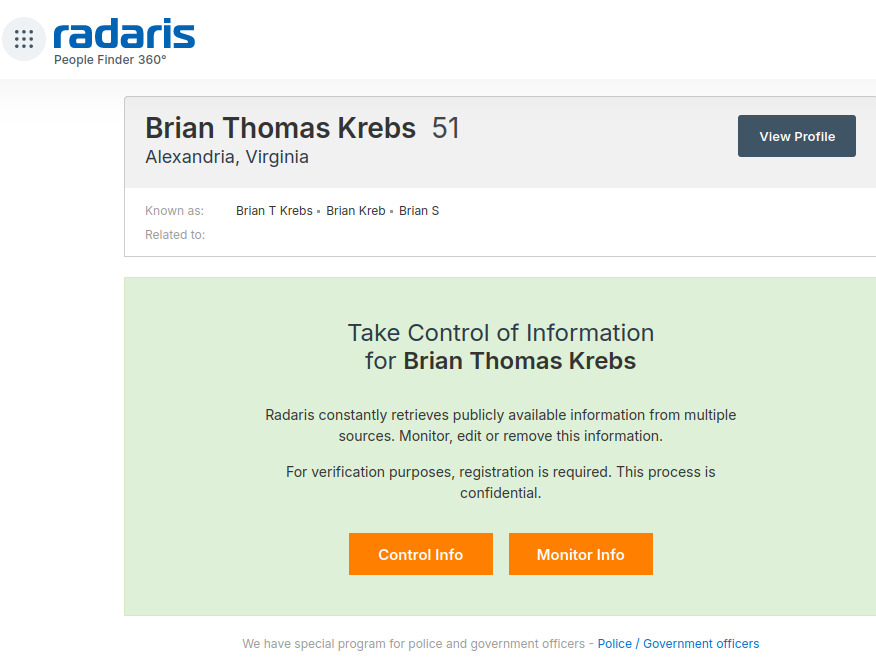
Read MoreIf you live in the United States, the data broker Radaris likely knows a great deal about you, and they are happy to sell what they know to anyone. But how much do we know about Radaris? Publicly available data indicates that in addition to running a dizzying array of people-search websites, the co-founders of…
Read MoreA Taxonomy of Prompt Injection Attacks Researchers ran a global prompt hacking competition, and have documented the results in a paper that both gives a lot of good examples and tries to organize a taxonomy of effective prompt injection strategies. It seems as if the most common successful strategy is the “compound instruction attack,” as…
Read More“You name it, we have seen it,” he said. “Salespeople are taking data from Salesforce and uploading it to Dropbox. Finance people are taking corporate financial information and emailing it to their Yahoo accounts. HR folks are using Airdrop to take sensitive salary data. But the fastest growing and scariest incidents we are seeing recently…
Read MoreRecent Posts
- Microsoft rolls out Recall to Windows Insiders with Copilot+ PCs
- Five Companies That Came To Win This Week
- The 10 Hottest Semiconductor Startups Of 2024
- Cybersecurity Snapshot: Prompt Injection and Data Disclosure Top OWASP’s List of Cyber Risks for GenAI LLM Apps
- Healthcare Ransomware Attacks: How to Prevent and Respond Effectively | BlackFog