Month: March 2024
Mar 08, 2024The Hacker NewsSecrets Management / Access Control In the realm of cybersecurity, the stakes are sky-high, and at its core lies secrets management — the foundational pillar upon which your security infrastructure rests. We’re all familiar with the routine: safeguarding those API keys, connection strings, and certificates is non-negotiable. However, let’s dispense with…
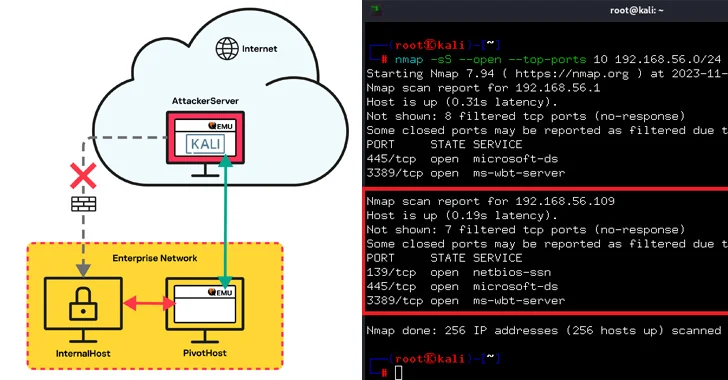
Read MoreMar 08, 2024NewsroomEndpoint Security / Network Security Threat actors have been observed leveraging the QEMU open-source hardware emulator as tunneling software during a cyber attack targeting an unnamed “large company” to connect to their infrastructure. While a number of legitimate tunneling tools like Chisel, FRP, ligolo, ngrok, and Plink have been used by adversaries to…
Read MoreMar 08, 2024NewsroomNetwork Security / Vulnerability Cisco has released patches to address a high-severity security flaw impacting its Secure Client software that could be exploited by a threat actor to open a VPN session with that of a targeted user. The networking equipment company described the vulnerability, tracked as CVE-2024-20337 (CVSS score: 8.2), as allowing…
Read MoreMar 08, 2024NewsroomVulnerability / Threat Intelligence The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Thursday added a critical security flaw impacting JetBrains TeamCity On-Premises software to its Known Exploited Vulnerabilities (KEV) catalog, based on evidence of active exploitation. The vulnerability, tracked as CVE-2024-27198 (CVSS score: 9.8), refers to an authentication bypass bug that allows…
Read MoreVMware has released fixes for several flaws that together could allow attackers to execute malicious code on the host system from inside a virtual machine, bypassing the critical isolation layer. Some of the flaws are in the virtualized USB controllers, so they impact most VMware hypervisors: VMware ESXi, VMware Workstation, VMware Fusion, and VMware Cloud…
Read MoreWelcome to this month’s edition of the “Bi-Weekly Cyber Roundup” by Canary Trap. In this ever-evolving landscape of cybersecurity, staying informed is not just a choice, but a necessity. Our mission is to keep you up-to-date with the most critical developments in the digital defense realm, and this bi-weekly publication is your gateway to the…
Read MoreLockBit Ransomware Affiliates Leverage Citrix Bleed Vulnerability (CVE-2023-4966) | BlackFog
by nlqip
Cybersecurity agencies have sounded alarm bells about active exploitation of a critical vulnerability in Citrix application delivery controllers (ADCs) and gateways. This flaw, tracked as CVE-2023-4966 and dubbed “Citrix Bleed” is being leveraged by affiliates of the LockBit ransomware gang to compromise organizations across sectors. The Vulnerability (CVE-2023-4966) CVE-2023-4966 stems from a session management issue…
Read MoreWelcome to this month’s edition of the “Bi-Weekly Cyber Roundup” by Canary Trap. In this ever-evolving landscape of cybersecurity, staying informed is not just a choice, but a necessity. Our mission is to keep you up-to-date with the most critical developments in the digital defense realm, and this bi-weekly publication is your gateway to the…
Read MoreIf you have been optimistically daydreaming that losses attributed to cybercrime might have reduced in the last year, it’s time to wake up. The FBI’s latest annual Internet Crime Complaint Center (IC3) report has just been published and makes for some grim reading. According to the IC3 report, online fraud hit record losses in 2023,…
Read MoreCISA and NSA Release Cybersecurity Information Sheets on Cloud Security Best Practices | CISA
by nlqip
Today, CISA and the National Security Agency (NSA) released five joint Cybersecurity Information Sheets (CSIs) to provide organizations with recommended best practices and/or mitigations to improve the security of their cloud environment(s). CISA and NSA encourage all organizations to review the practices and implement the mitigations provided in the joint CSIs to help strengthen their…
Read MoreRecent Posts
- Cybersecurity Snapshot: Prompt Injection and Data Disclosure Top OWASP’s List of Cyber Risks for GenAI LLM Apps
- Healthcare Ransomware Attacks: How to Prevent and Respond Effectively | BlackFog
- Black Friday Versus The Bots
- Over 2,000 Palo Alto firewalls hacked using recently patched bugs
- Chinese hackers target Linux with new WolfsBane malware