Month: March 2024
Mar 27, 2024The Hacker NewsData Protection / Browser Security As SaaS applications dominate the business landscape, organizations need optimized network speed and robust security measures. Many of them have been turning to SASE, a product category that offers cloud-based network protection while enhancing network infrastructure performance. However, a new report: “Better Together: SASE and Enterprise…
Read MoreSecurity Vulnerability in Saflok’s RFID-Based Keycard Locks It’s pretty devastating: Today, Ian Carroll, Lennert Wouters, and a team of other security researchers are revealing a hotel keycard hacking technique they call Unsaflok. The technique is a collection of security vulnerabilities that would allow a hacker to almost instantly open several models of Saflok-brand RFID-based keycard…
Read MoreCompany: Lake Dallas Independent School District Industry: Education Country: Denton County, Texas Employees: 650 Students: 4000 Locations: 5 campuses, 4 faculty buildings Web: www.ldisd.net Download PDF Lake Dallas ISD serves about 4,000 students in Denton County with a focus on providing big-school opportunities while maintaining a small-town atmosphere. Located adjacent to Lewisville Lake in North Texas, approximately 30 miles…
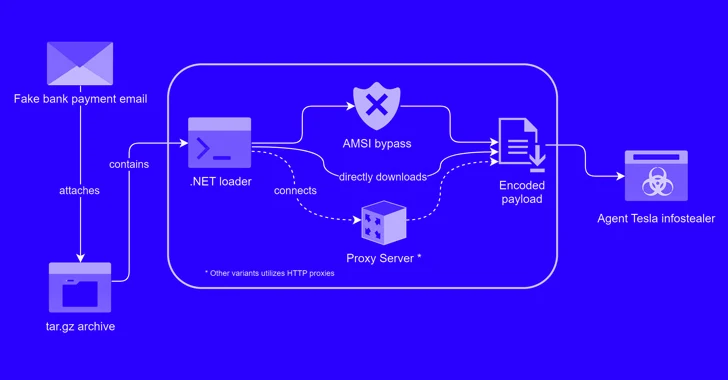
Read MoreMar 27, 2024NewsroomVulnerability / Cybercrime A new phishing campaign has been observed leveraging a novel loader malware to deliver an information stealer and keylogger called Agent Tesla. Trustwave SpiderLabs said it identified a phishing email bearing this attack chain on March 8, 2024. The message masquerades as a bank payment notification, urging the user to…
Read MoreSecurity teams can assess vendors’ policies on data handling, incident response, data regionalization, and privacy. They can evaluate a service-level agreement for things like availability and security metrics. They can also scrutinize the vendor’s security culture and practices, including third-party audits, and confirm features like multifactor authentication and data recovery. Ideally, companies should do real-time security…
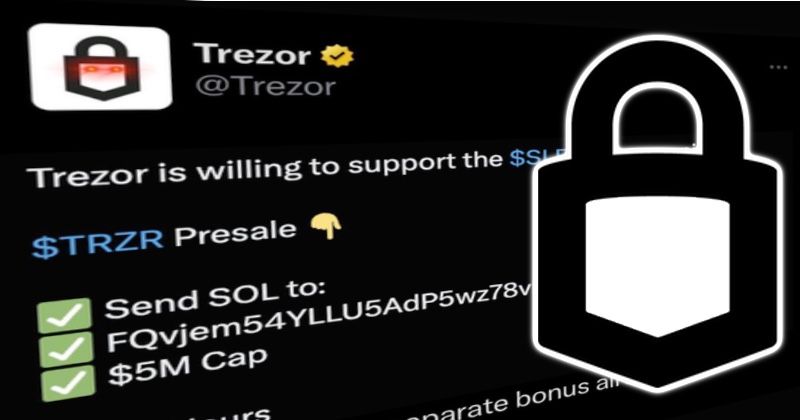
Read MoreThis isn’t the kind of thing you expect to see posted on the official Twitter account of Trezor, the well-known cryptocurrency wallet manufacturer. It’s a fairly blatant attempt to dupe unwary cryptocurrency fans into transfering digital currency into the wallet of a scammer. And whoever hacked Trezor’s Twitter account didn’t limit themselves to just posting…
Read MoreStep 3: Threat profiling This phase helps to identify and prioritize threats and understand how they can manifest. Threat profiling starts with the identification of potentially relevant threats through discussion with key stakeholders and analyzing available sources of threat intelligence (e.g., an internal threat intelligence team or external commercial feeds). Once the threat landscape is…
Read MoreTwo China-linked advanced persistent threat (APT) groups have been observed targeting entities and member countries affiliated with the Association of Southeast Asian Nations (ASEAN) as part of a cyber espionage campaign over the past three months. This includes the threat actor known as Mustang Panda, which has been recently linked to cyber attacks against Myanmar…
Read MoreSimilarities with older APT29 backdoors While Zscaler did not link the January attack to any APT group, the researchers believed at the time it was the work of a nation-state threat actor looking to exploit diplomatic relations, which is typical of APT29 targeting. Going further, Mandiant has not established clear similarities in design and code…
Read MoreAs cloud adoption rates continue to rise, security leaders are beginning to rethink the way they approach cybersecurity. What once worked for on-premises networks is no longer sufficient for complex, interconnected hybrid and multicloud environments. In addition to deploying security best practices throughout the full application lifecycle, CISOs also need to be able to obtain…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA