Month: March 2024
Mar 26, 2024NewsroomIndustrial Espionage / Threat Intelligence Threat hunters have identified a suspicious package in the NuGet package manager that’s likely designed to target developers working with tools made by a Chinese firm that specializes in industrial- and digital equipment manufacturing. The package in question is SqzrFramework480, which ReversingLabs said was first published on January…
Read MoreExplore the intricate web of Wizard Spider, a well-structured cybercrime syndicate notorious for its sophisticated malware attacks and ransomware extortions. Operating chiefly from Russia, with a strategic expansion into espionage software, this group exemplifies the threat landscape. Wizard Spider is a notorious cybercrime group believed to be operating out of Russia, particularly around Saint Petersburg,…
Read MoreAI has the power to transform security operations, enabling organizations to defeat cyberattacks at machine speed and drive innovation and efficiency in threat detection, hunting, and incident response. It also has major implications for the ongoing global cybersecurity shortage. Roughly 4 million cybersecurity professionals are needed worldwide. AI can help overcome this gap by automating…
Read MoreCISA has added three new vulnerabilities to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2023-48788 Fortinet FortiClient EMS SQL Injection Vulnerability CVE-2021-44529 Ivanti Endpoint Manager Cloud Service Appliance (EPM CSA) Code Injection Vulnerability CVE-2019-7256 Nice Linear eMerge E3-Series OS Command Injection Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber…
Read MoreIn today’s digital age, the internet plays a major role in young people’s lives, influencing how they further grow and develop into fully-fledged adults venturing out into the real world: From educational resources to social connections, discovering the latest viral dance trends, or watching how-to videos on how to cook pasta, the online world offers…
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2023-24955 Microsoft SharePoint Server Code Injection Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited…
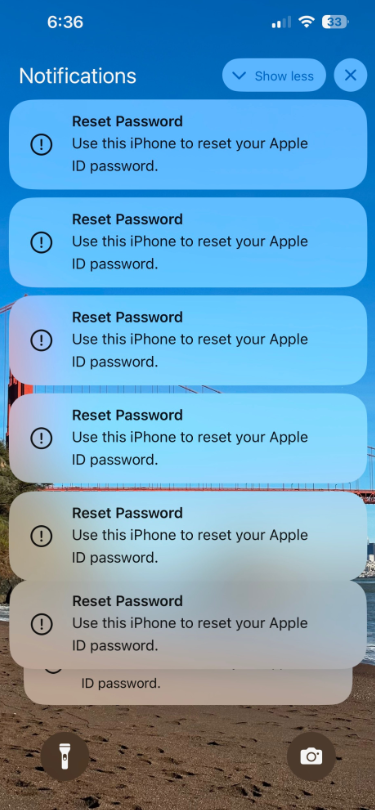
Read MoreSeveral Apple customers recently reported being targeted in elaborate phishing attacks that involve what appears to be a bug in Apple’s password reset feature. In this scenario, a target’s Apple devices are forced to display dozens of system-level prompts that prevent the devices from being used until the recipient responds “Allow” or “Don’t Allow” to…
Read MoreWho better to talk to about pan-African crime syndicates than someone tasked with shutting them down? From drug mules and sextortion to romance scams and spearphishing, this week’s talk with Secret Service Agent “Mark” pulls back the curtain on Black Axe and other crime rings operating worldwide. Because of its infrastructure (and apparently top notch…
Read MoreCISA released four Industrial Control Systems (ICS) advisories on March 26, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review the newly released ICS advisories for technical details and mitigations. Source link ddde
Read MoreAs organizations expand and increasingly invest in more cloud applications and services, their cloud footprint grows and often becomes more complex. That’s why it is critically important to regularly reevaluate the security of those cloud assets to ensure that everything is secure, and the required processes and procedures are being upheld. The growth in cloud…
Read MoreRecent Posts
- Hackers abuse Avast anti-rootkit driver to disable defenses
- Microsoft testing Windows 11 support for third-party passkeys
- Windows 11 24H2 update blocked on PCs with Assassin’s Creed, Star Wars Outlaws
- Windows 10 KB5046714 update fixes bug preventing app uninstalls
- Eight Key Takeaways From Kyndryl’s First Investor Day