Ransomware payments drop to record low of 28% in Q1 2024
by nlqip

Ransomware actors have had a rough start this year, as stats from cybersecurity firm Coveware show companies are increasingly refusing to pay extortion demands, leading to a record low of 28% of companies paying ransom in the first quarter of 2024.
This figure was 29% in Q4 2023, and Coveware’s stats show that diminishing payments have remained steady since early 2019.
This decrease is due to organizations implementing more advanced protective measures, mounting legal pressure not to meet the crooks’ financial demands, and cybercriminals repeatedly breaching promises not to publish or resale stolen data if a ransom is paid.
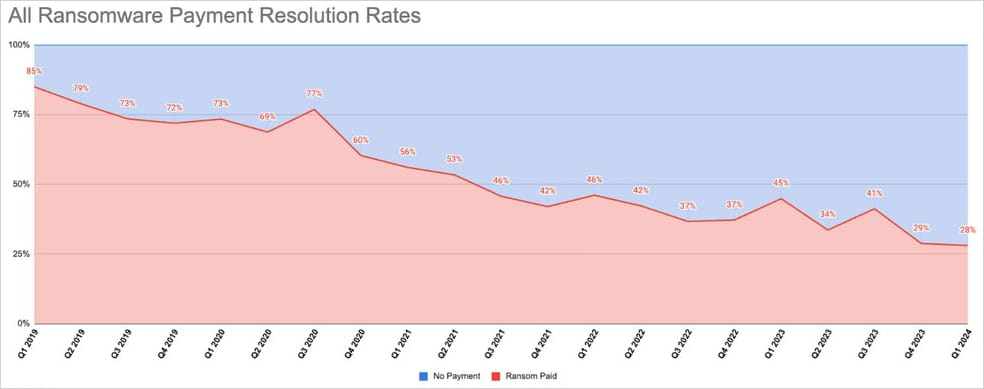
Source: Coveware
However, it is essential to note that despite the drop in the payment rate, the amount paid to ransomware actors is higher than ever before, reaching $1.1 billion last year, according to a Chainalysis report.
This is due to ransomware gangs hitting more organizations by escalating their attack frequency and demanding more substantial figures for not exposing stolen secrets and providing victims with a decryption key.
Concerning Q1 2024, Coveware reports a 32% quarter-over-quarter (QoQ) drop in the average ransom payment, now at $381,980, and a 25% QoQ increase in the median ransom payment, which stands at $250,000.
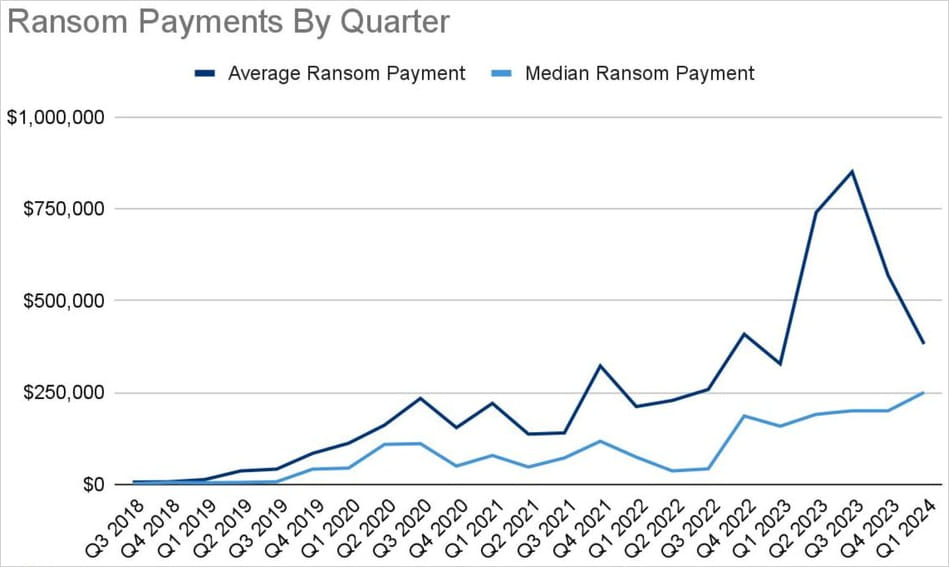
Source: Coveware
This simultaneous drop in average and rise in median ransom payments indicates a decrease in high-figure payments and an increase in moderate amounts. This could be caused by ransom demands becoming more modest and/or fewer high-value targets succumbing to extortion.
Regarding initial infiltration methods, there’s a rising number of cases where this is unknown, reaching nearly half of all reported cases in the first quarter of 2024.
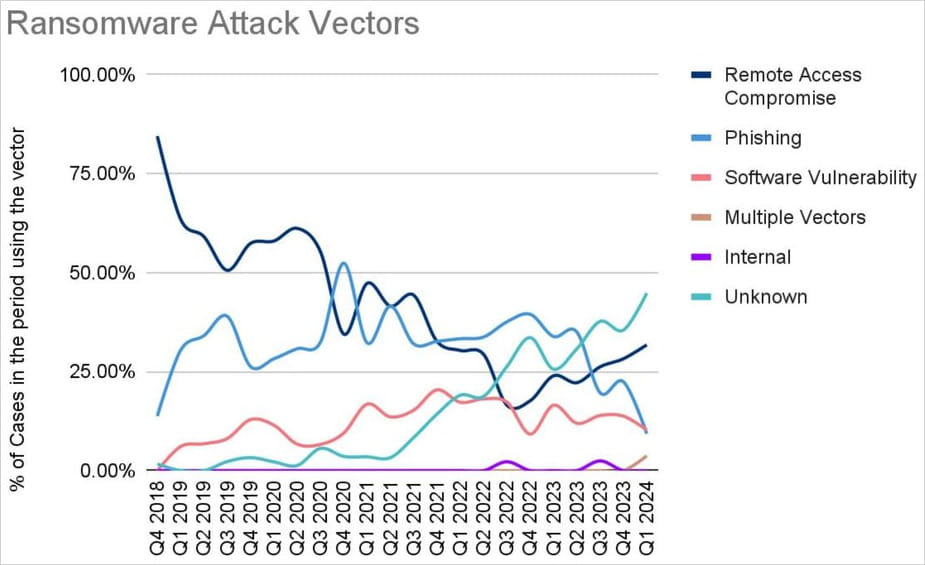
Coveware
From those that have been determined, remote access and vulnerability exploitation play the largest role, with the CVE-2023-20269, CVE-2023-4966, and CVE-2024-1708-9 flaws being the more widely exploited in Q1 by ransomware operators.
Law enforcement effect
Coveware reports that the FBI’s LockBit disruption has had a massive impact on the once-leading operation, as reflected in their attack statistics. The operation also brought turbulence to other major gangs, leading to payment disputes and exit scams, such as we saw with BlackCat/ALPHV.
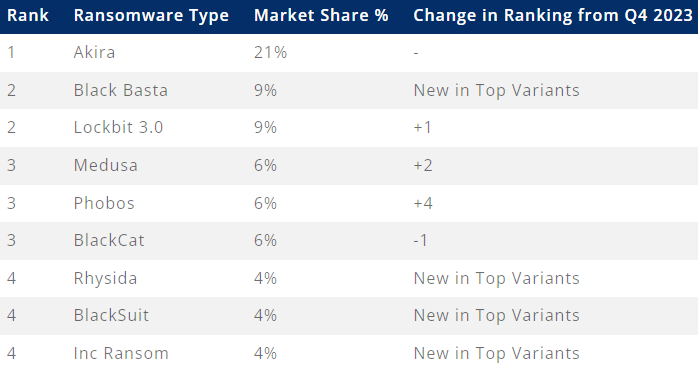
Source: Coveware
Moreover, these law enforcement operations have weakened the confidence of other ransomware affiliates toward RaaS operators, with many deciding to operate independently.
“We have already seen an increase in Babuk forks in recent attacks, and several former RaaS affiliates using the ubiquitous, and almost free, Dharma / Phobos services,” explains Coveware in the report.
According to the security firm, affiliates, in many cases, decided to quit cybercrime altogether.
“Most participants in the cyber extortion ecosystems are not hardened criminals, rather they are individuals with STEM skills that live in jurisdictions lacking both extradition treaties, and sufficient legitimate economic opportunities to put their skills to use,” continued Coveware.
“Some of these people will view the increased risk of getting in trouble along with the risk of getting cut out of their income as enough reason to quit.”
In this volatile space, Akira tops the list with the most active ransomware in terms of attacks launched in the first quarter of the year, remaining in place #1 for nine months now.
The FBI reported this week that Akira is responsible for breaches in at least 250 organizations, pocketing $42 million in ransom payments.
Source link
lol
Ransomware actors have had a rough start this year, as stats from cybersecurity firm Coveware show companies are increasingly refusing to pay extortion demands, leading to a record low of 28% of companies paying ransom in the first quarter of 2024. This figure was 29% in Q4 2023, and Coveware’s stats show that diminishing payments have…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
