Communication is Key – Leveraging Business Frameworks to Develop a Detection and Response Strategy | Binary Defense
by nlqip
Operating a business within the modern threat landscape can often appear like an impossible task. With a constant stream of new vulnerabilities, malware, and adversaries flowing, security leadership can often become overwhelmed and stuck in “analysis paralysis” struggling to identify what threats to invest resources towards.
It’s no secret that cybercrime has become big business with increasingly mature operations that mimic legitimate businesses with profits, losses, and margins. While the continuing “businessification” of cybercrime has increased the size of the criminal ecosystem, it does provide an opportunity for non-technical leaders to understand and make informed decisions regarding investments towards a detection and response strategy through conveying threat landscape information using common business principals.
One of the most valuable pieces of threat intelligence that defenders can leverage is understanding that “businessification” of cybercrime means the
criminal ecosystem is driven to maximize profits. Just like in the legitimate business world, profits can be increased through streamlining and efficiencies. It is far too expensive for cybercriminals to create novel attack chains for every target, meaning there are repeatable processes that defenders can key in on to drive their detection and response strategy.
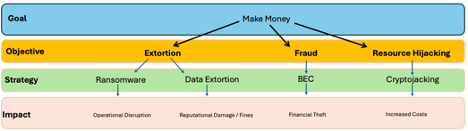
Consider the following example of applying the GOST (goals, objectives, strategies, and tactics) framework to the cybercrime ecosystem:
The goal of cybercriminals is to make money and the criminal ecosystem has coalesced around three main objectives: extortion, fraud, and resource hijacking. There are obviously additional cybercrime operations which are used to support these objectives such as credential harvesting, initial access brokers, and phishing platforms however, they should be considered supplemental and have less direct impact to organizations.
The strategies in which criminals employ to complete their objectives are largely ransomware (extortion), data theft (extortion), business email compromise (fraud), and cryptojacking (resource hijacking).
The technical components of how cybercriminals execute these attacks can be considered the tactics and are key to building out a prescriptive detection and response strategy. The tactic level of a GOST modeled threat is a great opportunity to leverage the MITRE ATT&CK framework to provide further context.
Leveraging a structured framework against the threat landscape to build a detection and response strategy also has the ancillary benefit of enabling organizations to develop valuable metrics to evaluate how effective their detection and response strategy is. Without defined threats, it becomes extremely difficult to generate meaningful security metrics to measure how more or less secure an organization is.
Applying cybercriminal GOST to a detection and response strategy
While it would be fantastic if organizations were able to stop all attacks, the reality of the situation is that organizations will have incidents but that does not mean they need to have a crisis. A critical first step to developing an effective detection and response strategy is to first understand an organization’s largest missions and the people, processes, and technology that support them. This concept was originally derived from within the military as identifying the “cyber key terrain” to help focus defenses to prevent or stop an attack.
Two-way communication between security staff and business leadership is foundational to develop an effective and robust detection and response strategy and being able to communicate complex technical or business details in a manner all members can understand will make development of the strategy exponentially easier.
Presenting the threat landscape in a business-oriented manner will enable business leaders to easily understand the threat landscape as it relates to risk to the business. In turn, business leaders will be able to provide security staff with guidance in terms of prioritization and resources to implement security measures. While all threats are important, depending on the business, they may be more sensitive to a particular impact than others. For example, healthcare and manufacturing are hypersensitive to operational disruption due to potential health and safety consequences while a financial management company could suffer a catastrophic failure if a series of fraudulent wire transfers are processed.
One of the benefits of working with a security company like Binary Defense is that we intimate knowledge of how cybercriminals operate and can distill the complex technical components of an attack down to easy-to-understand concepts and assets or service which are most at risk so that security and leadership can make informed decisions regarding their strategy.
Consider the previous example which has now been enriched with threat intelligence with the technical TTPs of an attack represented as tactics within the GOST framework and likely targets.

At this point security teams can now convey technical threat information in a business context and leaders can easily see the overlaps in tactics across different strategies. For example, consider the overlaps in tactics leveraged for ransomware and data extortion. While not every ransomware attack includes data exfiltration (“double-extortion”) and, as evidenced during the MFT mass exploitation events, data extortion attacks can happen independently without ransomware, leadership can immediately identify how closely these strategies are related within the threat landscape.
Using this simple diagram, leadership and security teams can have a productive conversation bridging the business and security worlds. For example, perhaps the business leaders are highly concerned with ransomware given the non-stop media attention, but the company runs totally on non-Windows and doesn’t leverage ESXi for virtualization infrastructure. The security team can inform leadership that while ransomware variants exist that impact other platforms, the ransomware threat remains very Windows and ESXi centric and so the overall risk may fall within acceptable limits. This type of two-way communication can help drive the conversation to focus on what’s most important to the business and what threats the business is most at risk of.
For example, perhaps the leadership and security teams agree that a business email compromise is both highly impactful to the business and the current detection and response strategy is not effective against this type of attack.

With this direction, the security team can begin developing a plan to build out an effective detection and response solution for various methods to successfully leverage the associated tactics.
Measuring Success
As mentioned previously, without defined threats, it become incredibly hard for security teams to communicate how much more secure the organization is based on their work.

Once a threat has been identified as a priority for the organization, the security teams can begin expanding upon the tactics listed in the GOST framework into more detailed technical details through open-source intelligence sources such as MITRE ATT&CK or threat intelligence services such as offered by Binary Defense.
A word of caution for organizations leveraging MITRE ATT&CK to drive their detection and response efforts: While ATT&CK is an amazing project and massively helpful for security teams, it’s important to understand that it does not contain a comprehensive list of techniques and there are multiple different ways a technique can be employed that enable a criminal to complete their objectives and having a single detection for a particular technique does not mean an organization is “covered”.
As an example, through these efforts the security teams may identify a list of associated techniques associated with BEC attacks and corresponding defensive countermeasures. As the security team adds more capabilities to detect and respond to the various techniques, valuable metrics can be communicated to the leadership to evaluate the organization’s current risk.
| Name | ATT&CK ID | Description | Detection |
| Suspicious Mailbox Rule | T1564.008 | Mailbox rule created to automatically forward emails to a non-company email | Operation contains (“new-inboxrule” OR “set-inboxrule”) AND (Parameters.Name contains (“RedirectTo” OR “ForwardTo” OR “ForwardAsAttachmentTo”) ) AND (Parameters.Value NotContains “companyemail.com”) |
If the requisite data or tooling is unavailable to effectively detect and respond to a BEC attack, the security team is in a much better place to go to leadership for further investment since the risk to the business has already been evaluated.
While it’s extremely easy to immediately dive into the technical details of cybersecurity, it’s critically important to understand how an organization fits within the threat landscape and just how important communication is to the development of a detection and response strategy. Without collaboration and communication between the business and security teams, organizations will continue to feel like they are always playing catch up with the criminals.
In navigating the intersection of cybersecurity and business operations, it’s crucial to recognize the intricate dynamics at play. While technical proficiency is indispensable, a nuanced understanding of an organization’s position within the broader threat landscape, coupled with effective communication, is paramount in developing robust detection and response strategies. Without cohesive collaboration between business and security teams, organizations risk falling behind in the perpetual race against cybercriminals.
Here are four strategic approaches to foster synergy between these two realms:
- Be Bilingual – Learn to communicate without technical terms
- In executive settings, where decisions are made, the language of cybersecurity must be translated into terms readily understandable by all stakeholders. Chief Technology Officers (CTOs) should adeptly articulate risks devoid of technical jargon, elucidating their potential impact on the organization’s reputation and financial health. By bridging this linguistic gap, CTOs can ensure that security considerations are comprehensively grasped and prioritized.
- Facts over Feelings
- Persuasive arguments in favor of cybersecurity initiatives hinge on the solidity of evidence. By leveraging empirical data, organizations can quantify the potential financial ramifications of security breaches and underscore the real-world repercussions. This evidence-based approach instills confidence in decision-makers and steers discussions away from subjective perceptions towards objective realities.
- How to properly convey the need for security investment
- Communicating the necessity of cybersecurity investment entails elucidating the tangible benefits it offers. From shielding against financial losses to safeguarding reputations and bolstering customer trust, the dividends of such investments are multifaceted. By articulating these advantages, organizations can position cybersecurity expenditures as strategic investments geared towards long-term resilience and sustainability.
- Collaborative Decision Making Reduces Risk
- Effective risk mitigation necessitates a collaborative ethos wherein leadership is actively engaged in cybersecurity deliberations. By inviting stakeholders into these discussions and presenting them with a spectrum of options along with their associated costs, organizations foster an environment conducive to dialogue and collective decision-making. Through this collaborative process, security measures can be aligned with overarching business objectives, thus minimizing risk exposure.
By adhering to these strategic imperatives, organizations can forge a symbiotic relationship between their security and business functions. Such cohesion not only enhances the efficacy of cybersecurity measures but also cultivates a culture of proactive risk management, thereby fortifying the organization’s resilience in an increasingly perilous digital landscape.
Source link
lol
Operating a business within the modern threat landscape can often appear like an impossible task. With a constant stream of new vulnerabilities, malware, and adversaries flowing, security leadership can often become overwhelmed and stuck in “analysis paralysis” struggling to identify what threats to invest resources towards. It’s no secret that cybercrime has become big business…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
