What Is Digital Risk Protection (DRP)? | Binary Defense
by nlqip

Digital risk protection is the strategy and implementation of protecting an organization’s data, reputation, and digital assets from online threats.
DRP extends across visible, deep, and dark web environments to identify and mitigate risks that could compromise an organization’s security posture or damage its public image. The process involves continuous monitoring, threat intelligence, and the analysis of potential threats to address vulnerabilities.
What Is Digital Risk Protection Service (DRPS)?
Digital Risk Protection Service is a managed solution offered by third party vendors designed to safeguard an organization’s data, reputation, and digital assets from online threats.
DRPS encompasses intelligence gathering and monitoring across the Clearnet, darknet, and social media to detect and mitigate risks. A DRP solution bolsters cybersecurity efforts by providing advanced detection technology and expertise, reducing the need for extensive in-house security operations.
Components of the Internet
The Clearnet, darknet, and deep web are components of the internet’s broader structure. Each represents different layers of accessibility and visibility:
Clearnet
Also known as the surface web, the clearnet includes all publicly accessible websites that can be indexed by standard search engines like Google, Bing, or Yahoo.
Deep Web
The deep web is an area of the internet that is not indexed by standard search engines. It includes pages that require login credentials, like personal email, online banking, or confidential corporate databases.
Darknet
Part of the deep web, the darknet refers to encrypted online content that is not indexed by traditional search engines and is often accessed using special software like Tor, which anonymizes user activity. It is known for maintaining privacy and is sometimes associated with illicit activities.
Further reading: What Is the Darknet?
What Are Digital Risks?
Digital risks are the potential threats and vulnerabilities associated with the use of digital technologies and the implementation of digital processes within an organization.
They encompass a broad spectrum of concerns including cybersecurity threats, data breaches, operational disruptions, and reputational damage. These risks arise as organizations increasingly rely on digital tools, making it essential to proactively identify, assess, and mitigate them to protect the organization’s data, assets, and reputation.
Types of Digital Risks

Cybersecurity Risks
Cybersecurity risks involve potential threats from malicious cyber activities. Protection against these risks is critical as they can compromise an organization’s data and disrupt its digital infrastructure.
Examples:
- Cyber threats including data breaches, ransomware attacks, and other forms of cyber-attacks.
- Physical and cyber threats directed towards executives and their families, necessitating travel risk assessments and social media training.
Data Leakage Risks
Data leakage risks refer to the accidental exposure of sensitive information. They occur when data leaks through security measures during digital expansion. Risks include unauthorized access or mishandling of data that can lead to breaches of privacy and non-compliance with data protection laws.
Examples:
- Infiltration of corporate networks by monitoring criminal marketplaces and chat rooms for information that could put the company at risk.
- Typosquatting attacks where threat actors create domain names similar to the company’s to steal sensitive information.
Reputational Risks
Reputational risks emerge when a company’s image is compromised digitally. This can happen through fraudulent activities such as impersonation or website spoofing. The impact on a company’s brand can be significant.
Examples:
- Internal threats from employees both pre-hire and post-layoff that could potentially harm the business.
- Threats to the brand image or reputation through negative content on review sites or social media platforms.
- Claims of workplace misconduct including sexual assault or other general misconduct within the HR scope.
- Exposure of marketing campaigns to negative feedback or slander on social media and various outlets, along with inaccurate trending analysis.
Operational Risks
Operational risks refer to the potential for the disruption of existing business processes. Introducing new software or incompatible updates can cause unexpected downtime, affecting client-facing operations like website accessibility.
Process automation risks also fall within this category, emerging when changes to automation processes cause compatibility or functionality issues. These risks can impact customer service and introduce new challenges in business operations.
Resilience risks are also considered operational, concerning an organization’s ability to maintain service availability and recover from disruptions. New technologies and cyberattacks can cause damage that affects operational continuity and requires robust recovery strategies.
Example:
- Physical threats such as bomb or shooting threats that could endanger employees or company assets.
Third-Party Risks
Third-party risks are those introduced by external partners, including vendors and service providers. These risks can sometimes be found in a supply chain and can range from data breaches to intellectual property theft, requiring careful management of vendor relationships.
Example:
- Compromises through verified third-party breaches and data dumps containing client email addresses, login credentials, and passwords.
Why Is Digital Risk Protection Important?
Digital risk protection is important because it serves as a proactive shield for an organization’s data, brand, and personnel. Businesses increasingly operate online, exposing them to a variety of risks. In a digital ecosystem where threats are always present and evolving, having a robust protection strategy is not just about defense, but maintaining operational integrity, safeguarding reputation, and ensuring compliance with regulatory standards. Through continuous monitoring and expert analysis, it provides actionable insights to navigate the complexities of the digital age securely.
Digital Risk Protection Solution Components
Digital risk protection services and solutions may differ depending on the provider. Generally speaking, a reliable DRP solution should include the following components:
Threat Information Engine
The Threat Information Engine serves as the initial line of defense in digital risk protection. It is an automated system designed to scour the internet—including the Clearnet, darknet, and social media—using specific keywords to detect potential threats. Once identified, these threats generate alerts for further analysis.
Counterintelligence
Counterintelligence refers to the analytical process where threats identified by the Threat Information Engine are scrutinized. Specialists assess these threats for their potential impact on physical security, cyber security, and public image. The team also conducts manual scraping to uncover threats that automated systems may not detect due to limitations like authentication barriers.
Intelligence Operations
Intelligence Operations involves predictive measures and proactive infiltration to forestall attacks before they occur. This team utilizes methods like sock puppet accounts to penetrate threat actor groups and monitor their activities. The goal is to identify and preempt ongoing and future attacks, campaigns, or the use of new malware.
How Does Digital Risk Protection Work?
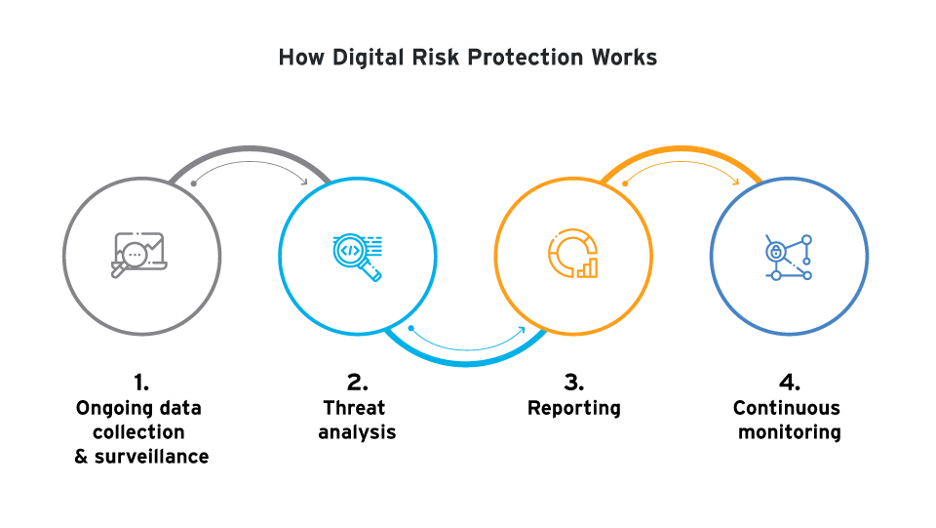
Digital risk protection works as a multi-layered approach to protecting an organization from online threats.
The process typically begins with ongoing data collection and surveillance across various digital platforms. This includes monitoring social media chatter, activities on the dark web, data breach information, and instances of typosquatted domains. The objective is identifying any potential threats that could affect an organization’s operations or reputation.
Once a potential threat is detected, analysts become actively involved in the investigation. They scrutinize findings to pinpoint actual threat indicators. This could involve identifying explicit threats like bomb threats or active shooter situations, or more stealthy ones such as leaked emails and passwords. Findings are then compiled into detailed reports specific to the needs of the client, which are established during the onboarding process. Clients can usually receive reports through various channels, including ticketing systems, emails, or direct phone calls, depending on the urgency and their preference.
Reporting is not the end of the service—it’s part of an ongoing commitment to vigilance. Post-report, the situation undergoes continuous monitoring over hours, days, or even weeks to track further developments or additional threats. In critical scenarios where immediate action is required, such as with imminent threats to physical safety, clients are notified immediately and directly via phone. Timely communication is key to making sure clients can initiate swift countermeasures to mitigate the threat effectively.
For instance, in a real-world scenario, if a threat group announces an imminent cyberattack on banking institutions, digital risk protection services would scrutinize available data to identify any clients on the target list. Upon verification, a report would be generated detailing the threat along with preventive measures, such as proactive alerts to internet service providers. This preemptive action can be instrumental in preventing operational downtime during the planned attack.
DRP Real World Examples
These scenarios provide concrete examples of Binary Defense clients, demonstrating the critical role digital risk protection plays.
Physical Threat to Employee
In a stark illustration of digital risk protection at work, a situation unfolded where an employee was targeted through social media. The threat information engine picked up a tweet warning people to steer clear of a business location due to potential harm. Swift analysis led to the identification of the retail location at risk. Immediate escalation to the client allowed for prompt involvement of local law enforcement, who were able to apprehend the individual in question, averting potential harm.
Compromised Employee Online Presence
Another real-world scenario involved an employee whose online activities posed a significant risk to their employer’s brand image. Detected through digital monitoring, the employee was found posting compromising photos from within a client’s residence. The detailed report compiled and delivered to the client included the employee’s identity and the risks posed to the company, demonstrating the importance of vigilant digital risk protection in preserving a brand’s reputation.
Insurance Payout Information Leaked on Darknet
A particularly sensitive case emerged when insurance payout details for a U.S. city were found posted on the darknet. Digital risk protection services engaged in manual scraping to uncover the poster’s identity and assess the breach’s origin. After the investigative process, the city was informed.
Employee’s Social Media Post Leads to Data Breach
A data breach was identified when an employee unknowingly posted a photograph on Instagram containing a customer’s personal information. This operational security lapse was detected through meticulous profile investigation. The client was promptly informed of the breach with recommendations for operational security improvements and employee training to prevent future incidents.
How to Manage Digital Risk
To manage digital risks effectively, an organization must first understand its digital footprint and identify all critical assets at risk. This includes everything from social media channels and sensitive resources to shadow IT and cloud platforms.
Once these assets are recognized, assessing the various ways each could be exploited is crucial. Using frameworks like MITRE ATT&CK can guide the process by providing a backward approach to understanding threat possibilities based on risk mitigation strategies.
Digital risk management also involves continuously monitoring for unauthorized access attempts and reducing the attack surface. Tools and strategies like the strategic placement of honeytokens can reveal unauthorized access attempts, while regular audits of internal and third-party assets can minimize the number of vulnerabilities. Implementing stringent access control policies, like Zero Trust Architecture, ensures resources, especially sensitive data, remain secure from unauthorized access.
Investing in a Digital Risk Protection Service (DRPS) is often more efficient than allocating dedicated internal resources to the task. These services provide the constant vigilance needed to identify and address threats swiftly, and in many cases more cost effectively.
Digital Risk Protection vs. Threat Intelligence
Digital risk protection and threat intelligence are complementary but distinct aspects of a comprehensive cybersecurity strategy.
Digital risk protection is an overarching approach that focuses on protecting an organization’s data, reputation, and digital assets by proactively identifying and mitigating risks across the internet.
Threat intelligence, on the other hand, is a component of digital risk protection. It is the knowledge obtained about potential or current threats to an organization’s digital assets. This intelligence includes understanding the context, mechanisms, and potential impact of cyber threats.
While digital risk protection is the application of controls and measures to protect against digital threats, threat intelligence is the information that guides the protective measures.
Digital Risk Protection FAQs
How does digital risk protection work?
Digital risk protection involves monitoring the internet, including the Clearnet, deep, and dark web, to identify and mitigate threats against an organization’s data and reputation.
What is the meaning of digital risk?
Digital risk refers to threats and vulnerabilities that arise with the use of digital technologies and processes within an organization.
What is the meaning of digital protection?
Digital protection encompasses measures and strategies implemented to safeguard an organization’s digital assets and reputation from online threats.
What is an example of a digital security risk?
An example of a digital security risk includes typosquatting attacks, where threat actors create misleading domain names to steal information.
Why is digital risk protection important?
Digital risk protection is vital for preventing operational disruptions, reputational damage, and financial penalties due to cyberattacks.
What are four common digital security risks?
Four common digital security risks are cybersecurity threats, data breaches, reputational risks, and compliance risks.
Source link
lol
Digital risk protection is the strategy and implementation of protecting an organization’s data, reputation, and digital assets from online threats. DRP extends across visible, deep, and dark web environments to identify and mitigate risks that could compromise an organization’s security posture or damage its public image. The process involves continuous monitoring, threat intelligence, and the…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
