These aren’t the Android phones you should be looking for
by nlqip

When shopping for a new smartphone, you’re likely to look for the best bang for your buck. If you’re on the hunt for a top-of-the-range device but aren’t keen on paying top dollar for it, offerings from lesser-known manufacturers will probably make your shortlist. Indeed, in the fiercely competitive smartphone market you may be even spoiled for choice as some little-known but high-end contenders can, in many respects, rival the flagship products of established tech titans like Apple, Samsung and Google.
On the other hand, while handsets targeting the price-conscious of us may not break the bank, they lose out when assessed against criteria such as brand recognition, competing telecommunications technologies and, in some cases, global security and data privacy considerations. Prestige (or lack thereof) and pricing policies associated with some manufacturers also have impacts on public perception – after all, the smartphone has evolved into one of the main status symbols of our time.
In some respects, even some cutting-edge devices can then be relegated to the mid-range or possibly even budget-friendly category. Particularly in the latter, smartphones often come loaded with older Android versions and have lesser, if any, after-purchase support. They often receive neither feature nor security updates, receive them late or only for a short period of time, and their manufacturers may even be barred from the Google Play Store app ecosystem entirely. As shown by several cases where phones were shipped with malware straight out of the box, supply chain security is another reason for worry.
Android multiverse?
With a market share of more than 70 percent, or around 3.3 billion active users, Android maintains its position as the leading global mobile operating system (OS). However, all is not equal in the world of Androids. Among Android-powered smartphones with full features, Samsung leads the way with a market share of almost 35 percent while its share of the total smartphone market amounts to 20 percent, right behind Apple.
Samsung is leading the pack not only thanks to its innovativeness and the high quality of its products that feature various options for every budget. Samsung’s lead also has to do with the fact that its phones benefit from security safeguards baked into Google Play and many of its phones come with software updates for longer periods of time than most of its competitors in the fragmented Android ecosystem. This all ultimately ensures optimized hardware and software integration and, by extension, enhances user experience and security.
Meanwhile, new handsets from, for example, Chinese tech giant Huawei, have been barred from the Google Play Store since 2019. In order to maintain its presence on the global market, the company, which boasts its own range of high-end smartphone models, has built its own operating system called HarmonyOS. This OS is largely based on the freely available Android Open-Source Project (AOSP). However, such exclusions from Google Play could have security implications for end users.
Collective security
In addition to security features baked into Android, users also benefit from security extended via the Google Play Store itself and its enabled-by-default Play Protect safeguards. This officially sanctioned Android app environment is built into the phones of smartphone manufacturers who are compliant with US and EU regulations. The store’s security is backed by Google’s App Defense Alliance, which was launched in November 2019 and counts ESET as a member.
The Google Play Store is home to more than 2.6 million apps, and almost all of them could, in theory, have malicious “sleeping functionalities” invisible at the time of upload or, as was the case with Ahmyth malware discovered by ESET recently, receive a malicious update later on in an incident also highlighted in Google’s August 2023 Threat Horizons report. Where threats are spotted on security-conscious stores like the Samsung Galaxy Store and even the Google Play Store, their operators act quickly to remove the apps.
As such, Android devices are at risk from several main types of malware. They are banking trojans, which steal login credentials and can even bypass two-factor (2FA) authentication. Another threat is posed by Remote Access Trojans (RATs), which can spy on victims and receive direct commands from attackers to steal money, credentials or data, hijack social media accounts and record phone calls. Then there is also Android ransomware that often spreads via malicious links on insecure websites or in emails and messages. Keeping people safe from these kinds of risks is central to the Alliance’s mission.
Security concerns us all
Most Android devices come fitted with manufacturer skins on top of the Android barebones version and offer access to Google Play. There are also vendors that have established a foothold in the market with other AOSP-based operating systems, but their app stores and apps available in them aren’t vetted by the App Defense Alliance.
Using third-party app stores or other unvetted places may be tempting, as they feature apps that you might not find on mainstream stores or offer fully open-source (FOSS) alternatives that bypass regional restrictions – or they were just not made by a tech giant you don’t want to share your data with. And while some of these stores may be properly regulated and run by legitimate companies, there are also hundreds of app stores with less strict, if any, vetting processes.
A bottom line emerges, where risks from alternative apps and app stores are more likely to impact some phone brands than others, and is a worry especially for those without access to Google’s authentic OS and app environments. [Note: Even people who decide to dispense with the safeguards built into Google Play-supported Android handsets and install apps from outside the official app store can, or will soon be able to, use the store’s real-time scanner to check apps from other sources.]
Cautionary tales abound
There’s been no shortage of examples of risks involving third-party app stores and phone makers, including those you probably never heard of. Let’s review at least a few that have emerged over the years:
- The British NE Regional Economic and Cyber Crime Units issued a warning back in 2020 about scammers claiming that specific paid-for apps – in this case a fake ‘TikTokPro’ app – could be downloaded “free” from certain third-party app stores. Victims got spyware or adware instead.
- And, just as there are fake apps, app updates and app stores created to lure victims into downloading malware, similar dangers can stem from cheap devices made by B-grade or no-name mobile brands. In 2020, anti-fraud firm Upstream found malware submitting fraudulent requests for subscription services on 53,000 Tecno W2 smartphones sold in some African countries.
- Similar threats, embedded in firmware, could be found in devices bought cheaply on big e-commerce platforms like Alibaba and Amazon and it’s likely that many budget and ultra-cheap offerings come with “additional costs”, such as adware and other nastiness.
- Cheapo phones aren’t necessarily only distributed in the developing world. In 2020, the U.S. government issued UMX U686CL Android smartphones for low-income users. It turned out later that they had come preinstalled with unremovable malware displaying unwanted advertisements and downloading unauthorized apps.
Here there be monsters
ESET Research continues to hunt down mobile threats, including those that target users of software from third-party stores or malware distributed in messages or on websites. Recent threats like Kamran spyware, hidden in a news app in Pakistan and downloaded directly from a legitimate news site, show just one of many problems with unvetted apps. After downloading the app and accepting its terms, the app started to gather data like contacts, calendar events, call logs, location information, device files, SMS messages, images and more.
Chances are high that you’re not from the Gilgit-Baltistan region of Pakistan. Regardless of where you live, however, you probably use a diversity of apps that aid you with banking, supply critical news updates, or just serve as entertainment. Whatever the price, brand or operating system powering your chosen handset, you need to explore the online world with caution.
Going for the multi-layered security option
Among other things, the Kamran campaign laid bare the importance of where users source their apps as well as the need for multiple layers of security on mobile devices. Simply, the arsenal of threats and the diverse attack methods available to criminals – regardless of location – demands protection. For this reason, solutions like ESET Mobile Security (EMS) not only block malware as presented in the Kamran case, but also offer comprehensive protection that scans for and blocks potentially harmful websites and comes fitted with payment protection, anti-phishing, and proactive anti-theft capabilities.
From spyware such as Kamran and others threats mentioned in this blog, EMS goes a long way towards protecting you from these threats. In fact, EMS would have caught Kamran twice – first, via the Anti-Phishing feature that would have prevented accessing the page and second, thanks to its Anti-Virus module that would have scanned the malicious app both before and during the installation process, blocking it as shown in the picture below.
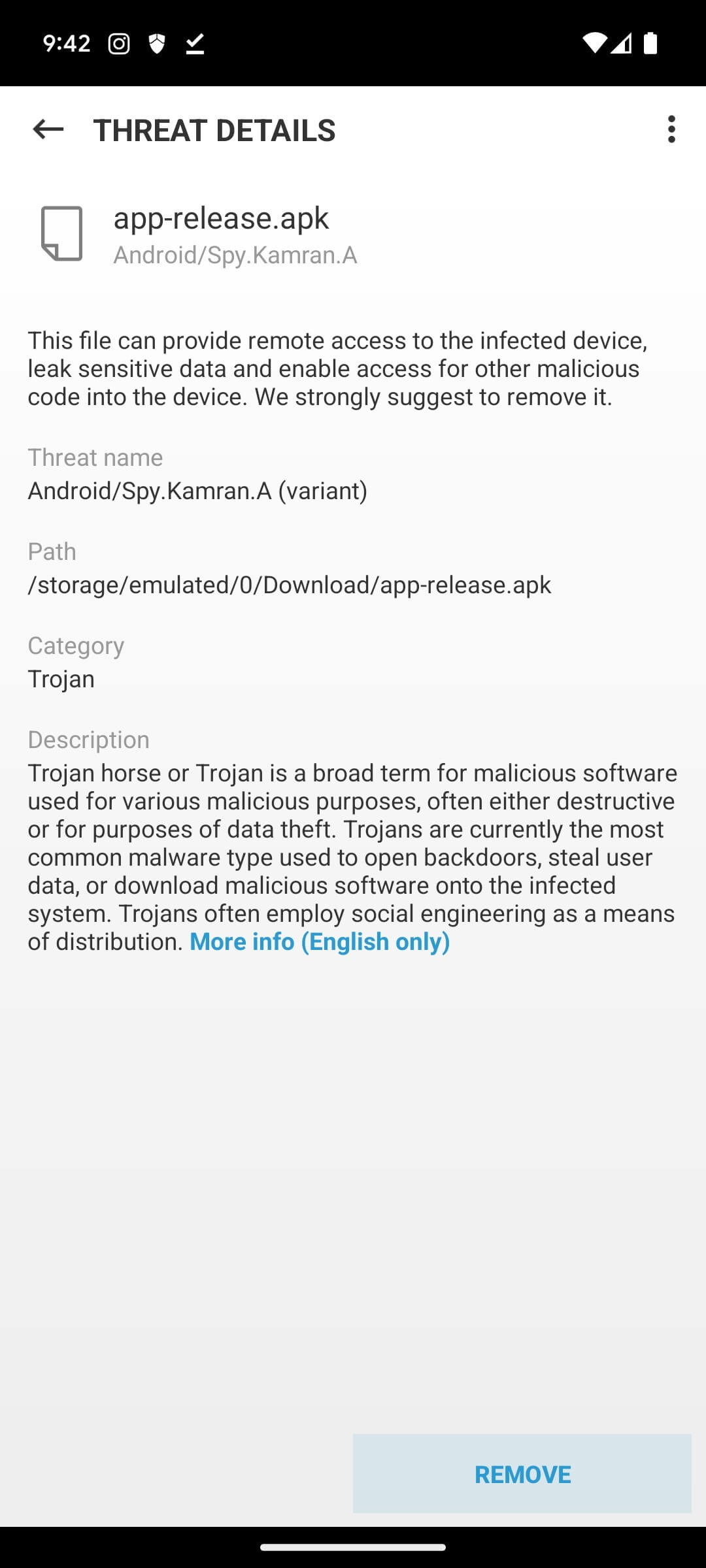
Whether by need or a sense of adventure, if you are diving into the unknown waters of budget-friendly phones from obscure manufacturers, third-party app stores and non-mainstream apps, you may face a perilous journey. In such as journey prioritizing security is a must. The easiest thing you can do is to download a time-tested security solution such as ESET Mobile Security, repeatedly awarded by third party testers like AV Comparatives and others.
Source link
lol
When shopping for a new smartphone, you’re likely to look for the best bang for your buck. If you’re on the hunt for a top-of-the-range device but aren’t keen on paying top dollar for it, offerings from lesser-known manufacturers will probably make your shortlist. Indeed, in the fiercely competitive smartphone market you may be even…
Recent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
