Month: April 2024
Ransomware actors have had a rough start this year, as stats from cybersecurity firm Coveware show companies are increasingly refusing to pay extortion demands, leading to a record low of 28% of companies paying ransom in the first quarter of 2024. This figure was 29% in Q4 2023, and Coveware’s stats show that diminishing payments have…
Read More‘This flexibility is crucial for adapting to business dynamics like mergers, acquisitions or shifts in customer preferences. It allows us to be more responsible and agile in how we manage our client relationships,’ Jean Prejean, president of Guardian Computer, tells CRN. Microsoft has confirmed that it is changing one of the most controversial parts of…
Read MoreTenable®, the Exposure Management company, today announced it has been recognized by CRN, a brand of The Channel Company, on the inaugural 2024 AI 100 list in the Artificial Intelligence (AI) for Cybersecurity category. This list spotlights vendors at the forefront of the AI revolution with offerings in areas such as cloud, data center and edge, software,…
Read More[R1] Stand-alone Security Patch Available for Tenable Security Center versions 5.23.1, 6.1.1, 6.2.0 and 6.2.1: SC-202403.1
by nlqip
Try Tenable Web App Scanning Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.…
Read More‘Pax8 recently made the difficult decision to conduct a reduction in workforce. This move primarily impacted North America and was less than five percent of our global workforce. Parting with valued teammates is never easy, but these actions will enable us to optimize operations, increase alignment, and position our business for long-term success,’ said a…
Read MoreThe departure of Sam Altman, Greg Brockman and, potentially, a large percentage of OpenAI employees to Microsoft may not ultimately be the best thing for the tech giant’s aspirations in GenAI. One of the biggest strengths of OpenAI has long been that it had backing, financial and otherwise, from Microsoft, without needing Microsoft to approve…
Read MorePRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure | CISA
by nlqip
SUMMARY The Cybersecurity and Infrastructure Security Agency (CISA), National Security Agency (NSA), and Federal Bureau of Investigation (FBI) assess that People’s Republic of China (PRC) state-sponsored cyber actors are seeking to pre-position themselves on IT networks for disruptive or destructive cyberattacks against U.S. critical infrastructure in the event of a major crisis or conflict with…
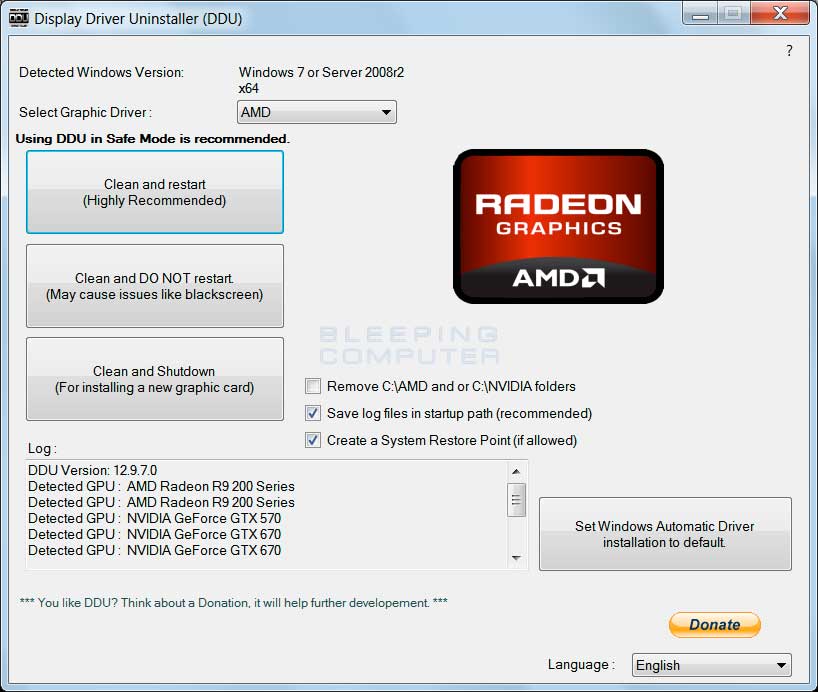
Read MoreScreenshots for Display Driver Uninstaller BleepingComputer Review: Display Driver Uninstaller, or DDU, is a driver utility programs that allows you to remove all traces of NVIDIA, AMD, and INTEL display and audio drivers from Windows. This allows you to perform a clean install of new drivers so that there are no potential issues with previous…
Read MoreIntroduction Once attackers have gained a foothold, perhaps by exploiting a remote code execution (RCE) vulnerability, leveraging a file upload, or some other tactic to gain execution on the target, they may end up using a web shell, as we described in a previous article. However, web shells are limited, and attackers may often want…
Read MoreAfter analyzing traffic from 159 bot defense customers, this review found that in the absence of a bot defense solution, Mobile APIs experience significantly more automation than Web applications. However, once a bot defense solution is deployed in mitigation/blocking mode, we see a reversal, with Web having higher levels of persistent attacks despite consistent mitigation.…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA