Month: April 2024
Upwind adds API security to its cloud security platform March 13: The Upwind Cloud Security Platform can now detect and respond to API threats in real time at the runtime level, according to the company. The API Security solution catalogs and maps an enterprise’s APIs using real-time traffic analysis and extended Berkeley Packet Filter (eBPF)…
Read MoreYou rarely root for a cybercriminal, but a new malware campaign targeting child exploiters doesn’t make you feel bad for the victims. Since 2012, threat actors have been creating a variety of malware and ransomware that pretend to be government agencies warning infected Windows users that they were viewing CSAM. The malware tells victims they…
Read MoreScreenshots for ESET Uninstaller BleepingComputer Review: The ESET Uninstaller is a tool that allows you to remove ESET products that you are not able to uninstall through normal methods. This tool performs a manual removal of ESET products that it detects on your computer. To use the uninstaller, simply download it and then double-click on…
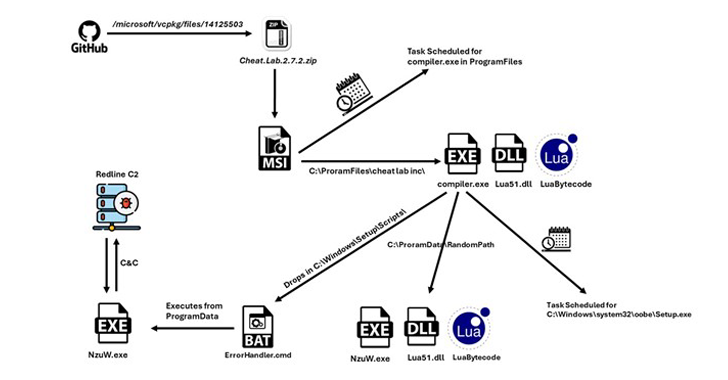
Read MoreA new information stealer has been found leveraging Lua bytecode for added stealth and sophistication, findings from McAfee Labs reveal. The cybersecurity firm has assessed it to be a variant of a known malware called RedLine Stealer owing to the fact that the command-and-control (C2) server IP address has been previously identified as associated with…
Read MoreMalware, Digital Security There is more to some images than meets the eye – their seemingly innocent façade can mask a sinister threat. 02 Apr 2024 • , 4 min. read Cybersecurity software has grown quite capable of detecting suspicious files, and with businesses becoming increasingly aware of the need to up their security posture…
Read MoreDigital Security And is that actually the right question to ask? Here’s what else you should consider when it comes to keeping your accounts safe. 03 Apr 2024 • , 5 min. read Much has been made over the past few years about the growing potential in passwordless authentication and passkeys. Thanks to the near-ubiquity…
Read MoreVideo Temu’s cash giveaway where people were asked to hand over vast amounts of their personal data to the platform puts the spotlight on the data-slurping practices of online services today 05 Apr 2024 Temu, the popular China-based online marketplace, recently launched a promotion where people received cash in exchange for new sign-ups that involved…
Read MoreWhenever we’re online, we leave a trail of data behind. As our lives are increasingly intertwined with digital technology, our digital footprints continue to grow larger. Some pieces of data that we generate, such as when posting on social media or purchasing products online, could hold immense value to cybercriminals lurking in the shadows of…
Read MoreESET researchers have discovered an active espionage campaign targeting Android users with apps primarily posing as messaging services. While these apps offer functional services as bait, they are bundled with open-source XploitSPY malware. We have named this campaign eXotic Visit and have tracked its activities from November 2021 through to the end of 2023. The…
Read MoreKids Online Should children’s apps come with ‘warning labels’? Here’s how to make sure your children’s digital playgrounds are safe places to play and learn. 11 Apr 2024 • , 6 min. read Our children spend more time on their phones than ever. Some 80% of European 9-16-year-olds access the internet from their phones every…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA