Month: April 2024
Video Almost 400 people in India and Pakistan have fallen victim to an ongoing Android espionage campaign called eXotic Visit 12 Apr 2024 Could your messaging app of choice have been authored by a threat actor known as Virtual Invaders? As described by ESET researchers this week, this is what happened to the victims of…
Read MoreScams Here’s how cybercriminals target cryptocurrencies and how you can keep your bitcoin or other crypto safe 15 Apr 2024 • , 6 min. read Bitcoin is on a tear. The world’s largest digital currency by market cap passed its previous record value of nearly $69,000 in early March. It’s now worth an estimated $1.3…
Read MoreKids Online From promoting questionable content to posing security risks, inappropriate ads present multiple dangers for children. Here’s how to help them stay safe. 16 Apr 2024 • , 5 min. read In today’s digital world, ads are practically unavoidable. From pop-up ads on your daily Wordle to sneaky affiliate posts on your favorite social…
Read MoreScams What are some of the most common giveaway signs that the person behind the screen or on the other end of the line isn’t who they claim to be? 18 Apr 2024 • , 5 min. read Our world is becoming more impersonal as it becomes more digital-centric. And because we can’t see the…
Read MoreWhat are the risks and consequences of having your health data exposed and what are the steps to take if it happens to you? Source link wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3 wse3…
Read MoreApr 20, 2024NewsroomVulnerability / Endpoint Security Users of the CrushFTP enterprise file transfer software are being urged to update to the latest version following the discovery of a security flaw that has come under targeted exploitation in the wild. “CrushFTP v11 versions below 11.1 have a vulnerability where users can escape their VFS and download…
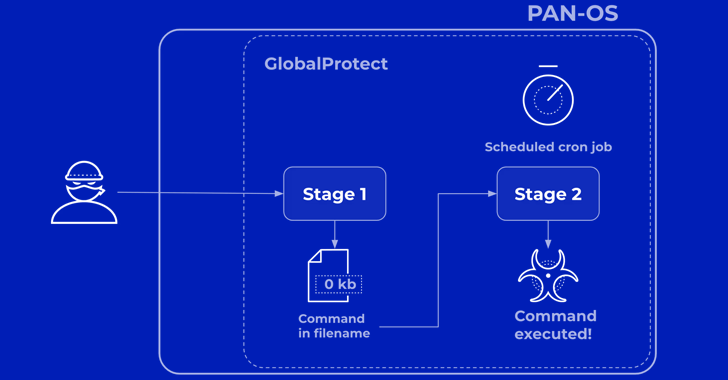
Read MoreApr 20, 2024NewsroomVulnerability / Network Security Palo Alto Networks has shared more details of a critical security flaw impacting PAN-OS that has come under active exploitation in the wild by malicious actors. The company described the vulnerability, tracked as CVE-2024-3400 (CVSS score: 10.0), as “intricate” and a combination of two bugs in versions PAN-OS 10.2,…
Read MoreChief information security officers (CISOs) understand the importance of having an incident response plan in place to help decrease the impact of a cyberattack. That’s because despite increased awareness and evolving security technology and practices, cyber threats continue to grow in both volume and sophistication. Microsoft security researchers have seen a 130.4% increase in organizations that have…
Read MoreFriday Squid Blogging: Squid Trackers A new bioadhesive makes it easier to attach trackers to squid. Note: the article does not discuss squid privacy rights. As usual, you can also use this squid post to talk about the security stories in the news that I haven’t covered. Read my blog posting guidelines here. Tags: privacy,…
Read MoreVulnerability exploits the difference between DOS and NT paths When someone is asked to type the path to a file on a Windows system, they are likely to type something of the form C:directorysubdirectoryfile.txt. This is known as a DOS-style file path and has been the most common way to represent a file’s location ever…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA