Month: April 2024
The introduction of Open AI’s ChatGPT was a defining moment for the software industry, touching off a GenAI race with its November 2022 release. SaaS vendors are now rushing to upgrade tools with enhanced productivity capabilities that are driven by generative AI. Among a wide range of uses, GenAI tools make it easier for developers…
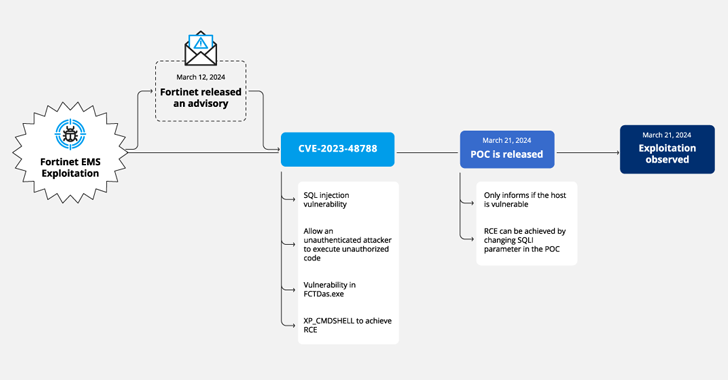
Read MoreApr 17, 2024NewsroomVulnerability / Web Application Firewall Cybersecurity researchers have discovered a new campaign that’s exploiting a recently disclosed security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun payloads. The activity entails the exploitation of CVE-2023-48788 (CVSS score: 9.3), a critical SQL injection flaw that could permit an unauthenticated attacker to…
Read MoreApr 17, 2024NewsroomEncryption / Vulnerability Threat actors are exploiting unpatched Atlassian servers to deploy a Linux variant of Cerber (aka C3RB3R) ransomware. The attacks leverage CVE-2023-22518 (CVSS score: 9.1), a critical security vulnerability impacting the Atlassian Confluence Data Center and Server that allows an unauthenticated attacker to reset Confluence and create an administrator account. Armed…
Read MoreUsing AI-Generated Legislative Amendments as a Delaying Technique Canadian legislators proposed 19,600 amendments—almost certainly AI-generated—to a bill in an attempt to delay its adoption. I wrote about many different legislative delaying tactics in A Hacker’s Mind, but this is a new one. Tags: A Hacker’s Mind, artificial intelligence, laws, LLM, noncomputer hacks Posted on April…
Read MoreApr 17, 2024NewsroomIoT Security / Network Security Cisco is warning about a global surge in brute-force attacks targeting various devices, including Virtual Private Network (VPN) services, web application authentication interfaces, and SSH services, since at least March 18, 2024. “These attacks all appear to be originating from TOR exit nodes and a range of other…
Read MoreRosenquist points to a past client that wanted to replace its human help desk with an AI chatbot for password resets. That bot, he says, would validate the user and reset corporate passwords for the IT department — a huge time-saver, but the system would require administrative access to sensitive credential systems that would be…
Read MoreThe proposed regulation in the NPRM applies to all organizations that are not considered “small businesses” as defined by the US Small Business Administration, except for small businesses that are considered “high-risk,” such as critical access hospitals in rural areas, owners and operators of nuclear facilities, and central school districts. In its 450-page NPRM, CISA…
Read MoreThe OpenJS Foundation was formed from the merging of the Node.js Foundation and the JS Foundation and hosts many JavaScript projects and technologies that are used by millions of websites and applications including Appium, Electron, jQuery, Node.js and webpack. In addition to detecting the social engineering attempt targeting one of its own projects, the Foundation…
Read MoreApply appropriate updates provided by Mozilla to vulnerable systems immediately after appropriate testing. (M1051: Update Software) Safeguard 7.1: Establish and Maintain a Vulnerability Management Process: Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard.o Safeguard 7.4: Perform…
Read MoreErin West is the Deputy District Attorney in Santa Clara County, California and the founder of Project Shamrock. Whether she’s prosecuting eye-popping SIM-swap money grabs or large-scale pig butchering operations out of business, her stories and experience can help you stay safer. And if you don’t scare so easily because you’re feeling really good about…
Read MoreRecent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict