Month: April 2024
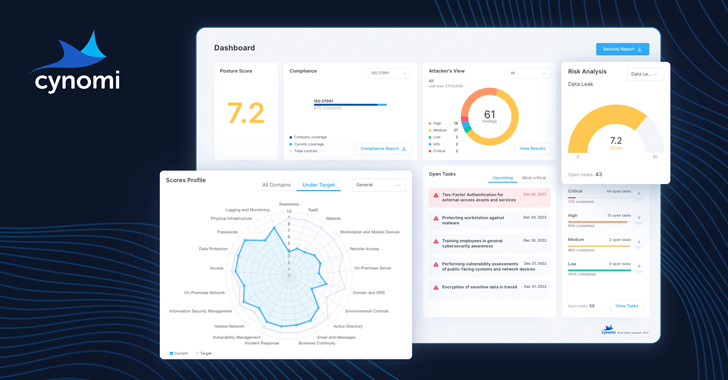
The need for vCISO services is growing. SMBs and SMEs are dealing with more third-party risks, tightening regulatory demands and stringent cyber insurance requirements than ever before. However, they often lack the resources and expertise to hire an in-house security executive team. By outsourcing security and compliance leadership to a vCISO, these organizations can more…
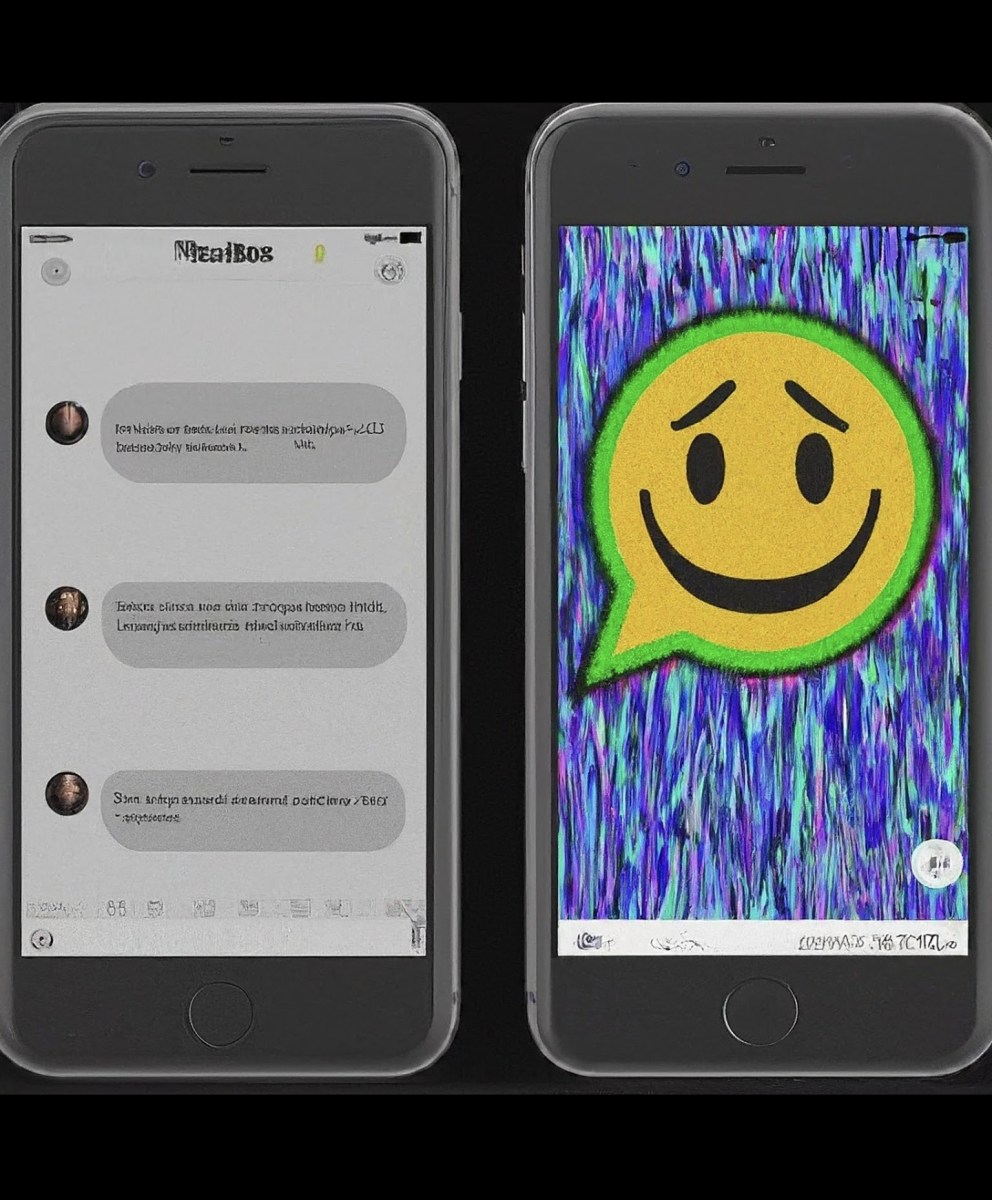
Read MoreWhatsApp mods have become increasingly popular in recent years, offering users a variety of features not available in the official app. However, these unauthorized modifications come with hidden risks that can compromise your privacy and security. A recent report by Kaspersky Lab revealed a malicious WhatsApp mod targeting Arabic-speaking users. This mod, spread through Telegram…
Read MoreLast week I posted a short memorial of Ross Anderson. The Communications of the ACM asked me to expand it. Here’s the longer version. Source link lol
Read MoreApr 10, 2024NewsroomHardware Security / Linux Cybersecurity researchers have disclosed what they say is the “first native Spectre v2 exploit” against the Linux kernel on Intel systems that could be exploited to read sensitive data from the memory. The exploit, called Native Branch History Injection (BHI), can be used to leak arbitrary kernel memory at…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. AI has long since been an intriguing topic for every tech-savvy person, and the concept of AI chatbots is not entirely new. In…
Read MoreApr 10, 2024The Hacker NewsWebinar / Identity Security We all know passwords and firewalls are important, but what about the invisible threats lurking beneath the surface of your systems? Identity Threat Exposures (ITEs) are like secret tunnels for hackers – they make your security way more vulnerable than you think. Think of it like this:…
Read MoreTargus, the well-known laptop bag and case manufacturer, has been hit by a cyber attack that has interrupted its normal business operations. In an SEC filing, Targus described discovering last Friday that hackers had gained unauthorised access to its IT systems. As a consequence, there has been a “temporary interruption” to the business’s operations as…
Read MoreChina for its part denies everything and can occasionally be found to make counter-accusations. Indeed, following the recent sanctioning and protest of a Chinese attempt to purloin the data of approximately 40 million United Kingdom voters, China responded with protests that such allegations were nothing more than “malicious slander.” Why should CISOs care about expat…
Read MoreMicrosoft has released security updates for the month of April 2024 to remediate a record 149 flaws, two of which have come under active exploitation in the wild. Of the 149 flaws, three are rated Critical, 142 are rated Important, three are rated Moderate, and one is rated Low in severity. The update is aside…
Read MoreApr 10, 2024NewsroomSoftware Security / Vulnerability A critical security flaw in the Rust standard library could be exploited to target Windows users and stage command injection attacks. The vulnerability, tracked as CVE-2024-24576, has a CVSS score of 10.0, indicating maximum severity. That said, it only impacts scenarios where batch files are invoked on Windows with…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA