Month: April 2024
10web — photogallery The current_url parameter of the AJAX call to the GalleryBox action of admin-ajax.php is vulnerable to reflected Cross Site Scripting. The value of the current_url parameter is embedded within an existing JavaScript within the response allowing arbitrary JavaScript to be inserted and executed. No authentication is required to exploit this issue.…
Read MoreApr 03, 2024NewsroomMobile Security / Zero Day Google has disclosed that two Android security flaws impacting its Pixel smartphones have been exploited in the wild by forensic companies. The high-severity zero-day vulnerabilities are as follows – CVE-2024-29745 – An information disclosure flaw in the bootloader component CVE-2024-29748 – A privilege escalation flaw in the firmware…
Read MoreApr 03, 2024NewsroomData Breach / Incident Response The U.S. Cyber Safety Review Board (CSRB) has criticized Microsoft for a series of security lapses that led to the breach of nearly two dozen companies across Europe and the U.S. by a China-based nation-state group called Storm-0558 last year. The findings, released by the Department of Homeland…
Read MoreApr 03, 2024NewsroomBrowser Security / Session Hijacking Google on Tuesday said it’s piloting a new feature in Chrome called Device Bound Session Credentials (DBSC) to help protect users against session cookie theft by malware. The prototype – currently tested against “some” Google Account users running Chrome Beta – is built with an aim to make…
Read MoreRoughly nine years ago, KrebsOnSecurity profiled a Pakistan-based cybercrime group called “The Manipulaters,” a sprawling web hosting network of phishing and spam delivery platforms. In January 2024, The Manipulaters pleaded with this author to unpublish previous stories about their work, claiming the group had turned over a new leaf and gone legitimate. But new research…
Read MoreWhile using public AI tools, fewer than half (47%) have an AI Acceptable Use Policy, opening them to risks of losing intellectual property and competitive advantage. This is despite a high (60% use ChatGPT and 40% use Gemini) usage of such tools. Additionally, among the 80% organizations that believed their data was ready for AI,…
Read MoreApr 03, 2024The Hacker NewsCybersecurity / Penetration Testing Attack surface management (ASM) and vulnerability management (VM) are often confused, and while they overlap, they’re not the same. The main difference between attack surface management and vulnerability management is in their scope: vulnerability management checks a list of known assets, while attack surface management assumes you…
Read MoreClass-Action Lawsuit against Google’s Incognito Mode The lawsuit has been settled: Google has agreed to delete “billions of data records” the company collected while users browsed the web using Incognito mode, according to documents filed in federal court in San Francisco on Monday. The agreement, part of a settlement in a class action lawsuit filed…
Read MoreThe content of this post is solely the responsibility of the author. AT&T does not adopt or endorse any of the views, positions, or information provided by the author in this article. If you’ve ever worked in an IT department, you know how easily a single misclick can lead to data breaches and system compromises.…
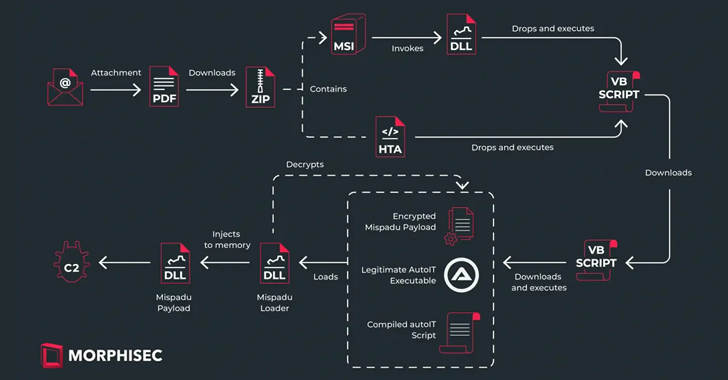
Read MoreThe banking trojan known as Mispadu has expanded its focus beyond Latin America (LATAM) and Spanish-speaking individuals to target users in Italy, Poland, and Sweden. Targets of the ongoing campaign include entities spanning finance, services, motor vehicle manufacturing, law firms, and commercial facilities, according to Morphisec. “Despite the geographic expansion, Mexico remains the primary target,”…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA