Month: April 2024
One of the missteps I found was that, by default, the Tor node would accept and relay BitTorrent traffic. My American ISP detected the BitTorrent traffic exiting my node and started sending me emails, and, I suspect, interfering with my network traffic (though I didn’t prove that beyond a suspicion). Fortunately, the Tor Project…
Read MoreThe Department of State has started imposing visa restrictions on mercenary spyware makers and peddlers, prohibiting their entry into the United States, as announced earlier in February. The crackdown has begun with 13 individuals and their close families (i.e., spouses and children) linked to commercial spyware operations. Taken pursuant to Section 212 (a)(3)(C) of the…
Read MoreCertificate revocation is an important, if ill understood, part of enterprise security. In this three-part blog series, I’ll explore why we need it, how you do it, and strategies for maximizing the benefits you get for it. Certificates Everywhere The use of digital certificates is growing exponentially. In particular, the move to a fully encrypted…
Read MoreBecky Holmes loves DMing with scammers. When it comes to romance scammers, she will do whatever it takes, pursuing them to the great delight of her fans on social media. From flings with A-listers to the lantern-jawed soldier with a heart of gold, Becky’s on a mission to unravel the weird world of online swindler…
Read MoreAny CISO who’s been around the block understands Erik’s words. So, let’s roll up our sleeves and get started by understanding the scope of the problem. Understand Needs The first step in any security project is to be sure you have a clear inventory of your asset and applications. Everything flows from them. For most,…
Read MoreMost blogs are written in the first person, and this one is for a particular reason. I myself am half Filipino, have had transactions with Filipino government systems, and I am also a security expert. So, my personal insight may be more useful and impactful than a corporate statement. The 2018 Philippine Identification System Act,…
Read MoreThreat actors continue to find creative yet relatively unsophisticated ways to launch new campaigns to reap profits from crypto-mining operations. Source link lol
Read MoreCISA has added one new vulnerability to its Known Exploited Vulnerabilities Catalog, based on evidence of active exploitation. CVE-2022-38028 Microsoft Windows Print Spooler Privilege Escalation Vulnerability These types of vulnerabilities are frequent attack vectors for malicious cyber actors and pose significant risks to the federal enterprise. Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of…
Read MoreBroadcom Price Hikes And Partner Snubs Fueling Scale Computing’s Record Growth, CEO Jeff Ready Says
by nlqip
‘A lot of people thought Broadcom would treat VMware differently, and it turns out no. It was the second week of January when the partner stuff got announced and it was like the floodgates opened. I’m still up at night sending emails like I’m an inside sales guy, just trying to help the team,’ Scale…
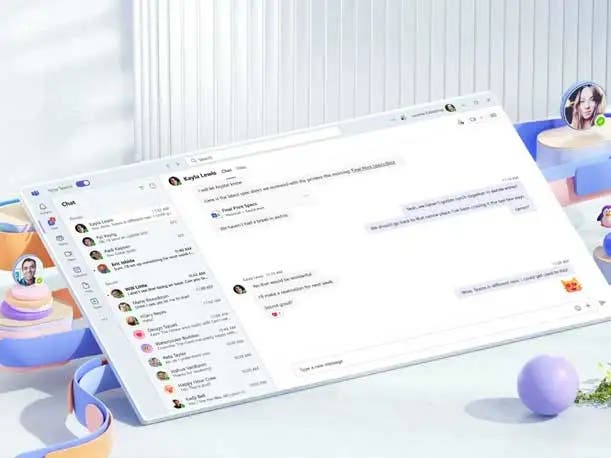
Read MoreChanda Wong, a senior product marketing manager for Microsoft 365 for SMBs, told partners on a call last week that they have until Aug. 1 to sell the suites with Teams to a customer as long as the partner quoted the customer before Microsoft announced the end of Teams suites on April 1. Microsoft solution…
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm