Month: April 2024
Some Google Chrome users report having issues connecting to websites, servers, and firewalls after Chrome 124 was released last week with the new quantum-resistant X25519Kyber768 encapsulation mechanism enabled by default. Google started testing the post-quantum secure TLS key encapsulation mechanism in August and has now enabled it in the latest Chrome version for all users. The new version utilizes the Kyber768…
Read MoreSecurity researchers analyzing phishing campaigns that target United States Postal Service (USPS) saw that the traffic to the fake domains is typically similar to what the legitimate site records and it is even higher during holidays. Phishing operations typically target people’s sensitive information (account credentials, card details) or try to trick users into making payments…
Read MoreApr 28, 2024NewsroomCredential Stuffing / Data Breach Identity and access management (IAM) services provider Okta has warned of a spike in the “frequency and scale” of credential stuffing attacks aimed at online services. These unprecedented attacks, observed over the last month, are said to be facilitated by “the broad availability of residential proxy services, lists…
Read MoreImage: AI-generated via Midjourney Japanese police placed fake payment cards in convenience stores to protect the elderly targeted by tech support scams or unpaid money fraud. The cards are labeled “Virus Trojan Horse Removal Payment Card” and “Unpaid Bill Late Fee Payment Card,” and were created by the Echizen Police in the Fukui prefecture in Japan…
Read MoreVideo The investigation uncovered at least 40,000 phishing domains that were linked to LabHost and tricked victims into handing over their sensitive details 26 Apr 2024 One of the world’s largest phishing-as-a-service (Phaas) platforms known as LabHost has been disrupted in a global law enforcement operation, Europol has announced. Authorities from no fewer than 19…
Read MoreOkta warns of an “unprecedented” spike in credential stuffing attacks targeting its identity and access management solutions, with some customer accounts breached in the attacks. Threat actors use credential stuffing to compromise user accounts by trying out in an automated manner lists of usernames and passwords typically purchased from cybercriminals. In an advisory today, Okta says…
Read MoreInternational Business Machines (IBM) has announced its intention to acquire HashiCorp, a cloud infrastructure automation company, in a deal valued at $6.4 billion. This strategic move aims to expand IBM’s cloud-based software offerings and capitalize on the surging demand driven by artificial intelligence (AI). The deal comes as IBM experiences mixed results, with its software…
Read MoreApr 27, 2024NewsroomCyber Attack / Malware Cybersecurity researchers have discovered a targeted operation against Ukraine that has been found leveraging a nearly seven-year-old flaw in Microsoft Office to deliver Cobalt Strike on compromised systems. The attack chain, which took place at the end of 2023 according to Deep Instinct, employs a PowerPoint slideshow file (“signal-2023-12-20-160512.ppsx”)…
Read MoreIn a major move within the cybersecurity sector, KnowBe4, a leading security awareness training platform, has announced the acquisition of Egress, a prominent cloud email security provider. This strategic partnership blends two powerful forces in the battle against cyber threats. Who are KnowBe4 and Egress? KnowBe4: A pioneer in security awareness training, KnowBe4 empowers organizations…
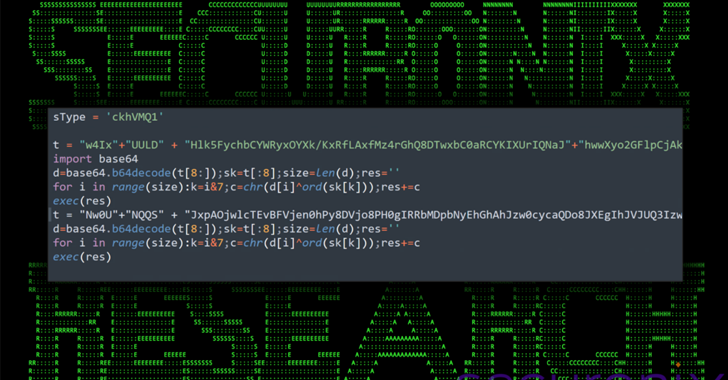
Read MoreApr 27, 2024NewsroomMalware / Software Security An ongoing social engineering campaign is targeting software developers with bogus npm packages under the guise of a job interview to trick them into downloading a Python backdoor. Cybersecurity firm Securonix is tracking the activity under the name DEV#POPPER, linking it to North Korean threat actors. “During these fraudulent…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA