Month: April 2024
What Is MITRE ATT&CK®? MITRE ATT&CK is a documented collection of information about the malicious behaviors advanced persistent threat (APT) groups have used at various stages in real-world cyberattacks. ATT&CK, which stands for Adversarial Tactics, Techniques, and Common Knowledge, includes detailed descriptions of these groups’ observed tactics (the technical objectives they’re trying to achieve), techniques…
Read More‘The combined power of the BMC Helix platform and Netreo solutions provides IT Operations, DevOps practitioners, developers, and network teams with comprehensive insights spanning applications, infrastructure, and networks, helping them increase the overall reliability and performance,’ wrote Margaret Lee, BMC’s senior vice president and general manager of digital service and operations management, in a blog…
Read MoreBroadcom CEO Hock Tan: Focus On Upselling VMware’s ‘Largest 2,000’ Customers Proves ‘Very Successful’
by nlqip
Tan says Broadcom expects double-digit revenue gains from its VMware Cloud Foundation as it is focused on providing resources, support and upselling for VMware’s ‘largest 2,000 strategic customers.’ Broadcom CEO Hock Tan expects his company’s VMware business to grow double-digits for the rest of the year as Broadcom’s sales teams work on upselling the 2,000…
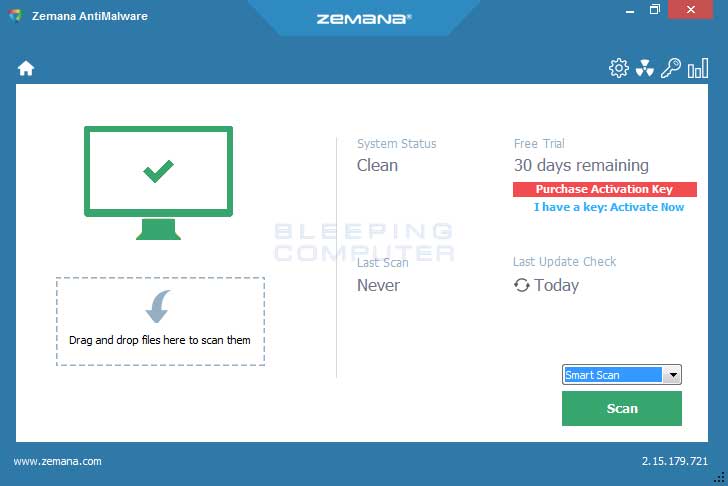
Read MoreScreenshots for Zemana AntiMalware BleepingComputer Review: Zemana AntiMalware is a cloud based malware scanner that provides excellent malware detection, quick scans, and easy malware removal. As it is cloud based, it always has the most current virus definitions and new definitions can be quickly pushed out by the developers when new malware is discovered. Zemana…
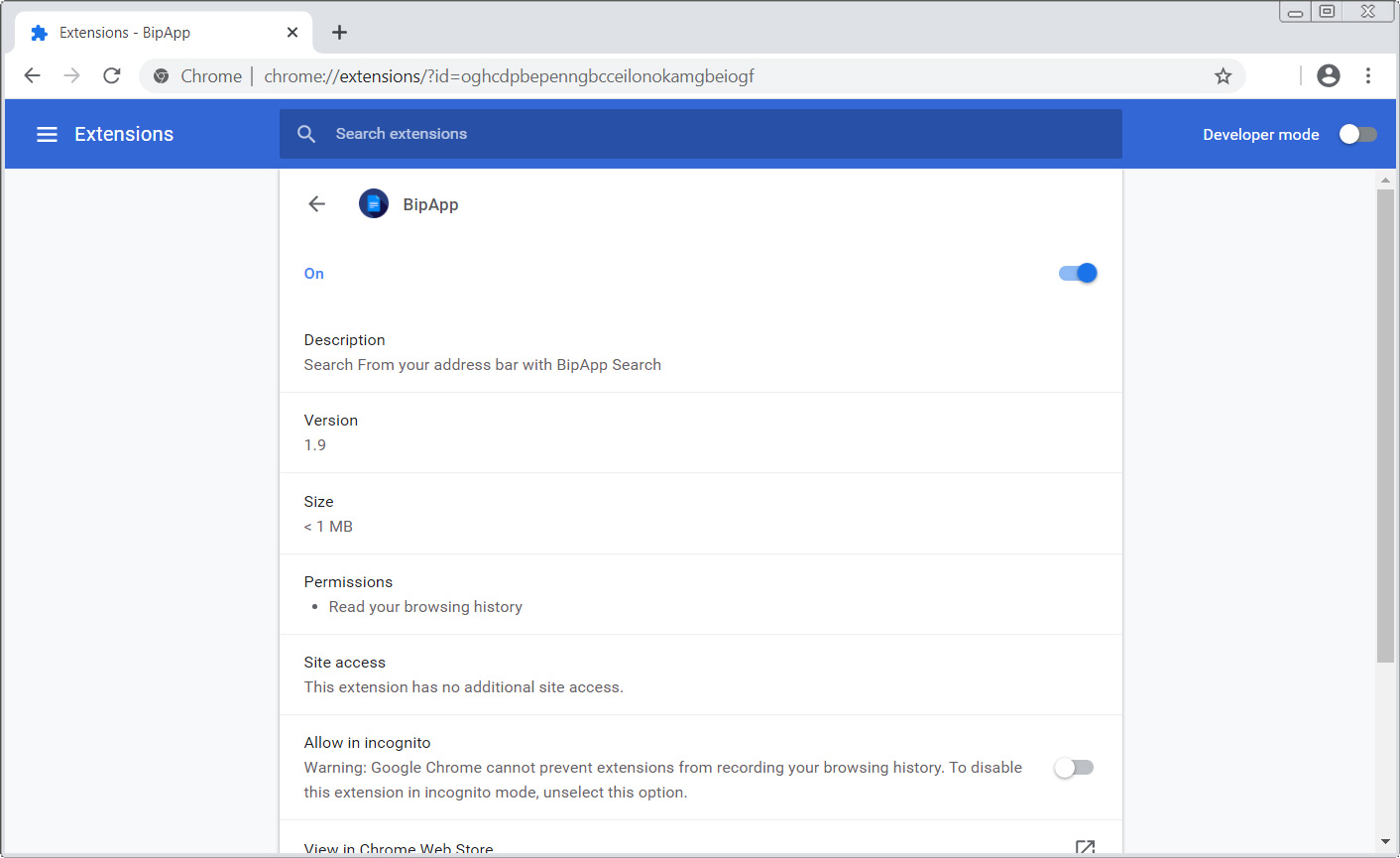
Read MoreIn order to remove BipApp Chrome Extension completely you will need to reset Chrome back to its initial settings. Doing these steps will erase all configuration information from Chrome such as your home page, tab settings, saved form information, browsing history, and cookies. This process will also disable any installed extensions. All of your bookmarks,…
Read More“As time goes on, you’re going to see the generative AI really drag not just compute systems, but the traditional core servers as well as traditional storage, because everything is going to be optimized for AI,” Dell ISG president Arthur Lewis told Morgan Stanley Technology, Media & Telecom Conference this week. Dell ISG President Arthur…
Read MoreBetween crossovers – Do threat actors play dirty or desperate? In our dataset of over 11,000 victim organizations that have experienced a Cyber Extortion / Ransomware attack, we noticed that some victims re-occur. Consequently, the question arises why we observe a re-victimization and whether or not this is an actual second attack, an affiliate crossover…
Read MoreProtecting information system media containing Controlled Unclassified Information (CUI), and monitoring for the use of portable storage devices and removable media is essential to protecting the integrity of information systems. Monitoring organizational communications at external boundaries, as well as key internal boundaries is essential to detect attacks, and potential indicators of attacks. Removable media is…
Read MoreFor the week ending April 12, CRN takes a look at the companies that brought their ‘A’ game to the channel including Google Cloud, Intel, Wiz, Zscaler, Lumen Technologies and startup solution provider Ensemble AI. The Week Ending April 12 Topping this week’s Came to Win is Google Cloud which used this week’s Google Next…
Read MoreCybersecurity Snapshot: CISA Says Midnight Blizzard Swiped U.S. Gov’t Emails During Microsoft Hack, Tells Fed Agencies To Take Immediate Action
by nlqip
Check out CISA’s urgent call for federal agencies to protect themselves from Midnight Blizzard’s breach of Microsoft corporate emails. Plus, a new survey shows cybersecurity pros are guardedly optimistic about AI. Meanwhile, SANS pinpoints the four trends CISOs absolutely must focus on this year. And the NSA is sharing best practices for data security. And…
Read More