Month: April 2024
Media Room
by nlqip
https://www.globalsecuritymag.com/bernard-montel-tenable-faced-with-the-increas… Source link lol
Read More‘When you think about how much of [our revenue] is actually managed on a day-to-day [basis] by the partners, they’re massive custodians of the brand and customer success and lifetime value,’ says Salesforce channel chief Steve Corfield. Steve Corfield, capping off his first year as Salesforce channel chief, is at work on what he calls…
Read MoreTenable Introduces Groundbreaking Visibility Across IT, OT and IoT Domains to Fully Illuminate Attack Vectors and Risks
by nlqip
Tenable®, the Exposure Management company, today announced the release of Tenable One for OT/IoT. It is the first and only exposure management platform that provides holistic visibility into assets across IT and operational technology (OT) environments. The convergence of physical assets and IT – such as HVAC systems in data centers, badge readers in office buildings, cameras…
Read MoreTry Tenable Web App Scanning Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.…
Read MoreThe deal is the second acquisition to date for cybersecurity unicorn Armis. Armis announced its acquisition Wednesday of a startup focused on helping organizations prioritize their response efforts to cybersecurity risk. The acquisition of the startup, Silk Security, is the second to date for cybersecurity unicorn Armis. The company said the deal is worth $150…
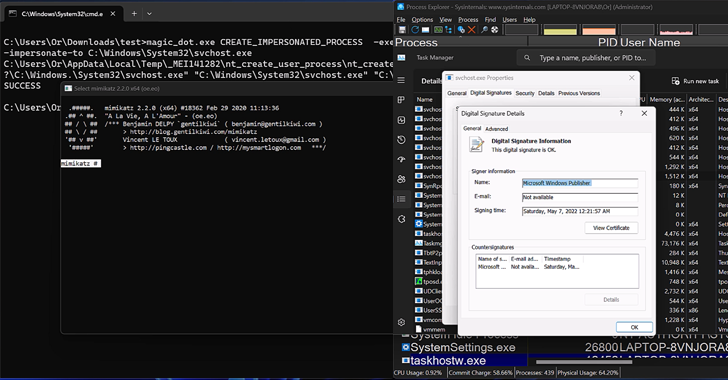
Read MoreApr 22, 2024NewsroomRootkit / Software Security New research has found that the DOS-to-NT path conversion process could be exploited by threat actors to achieve rootkit-like capabilities to conceal and impersonate files, directories, and processes. “When a user executes a function that has a path argument in Windows, the DOS path at which the file or…
Read MoreOverall Scanning Traffic Changes Lest the downward trend shown in Figure 2 makes it seem like overall scanning traffic may be abating, it’s important to note that the volume of scanning we observed has remained relatively constant, at least over the last three months, increasing by approximately 5.1% from August to September, then falling approximately…
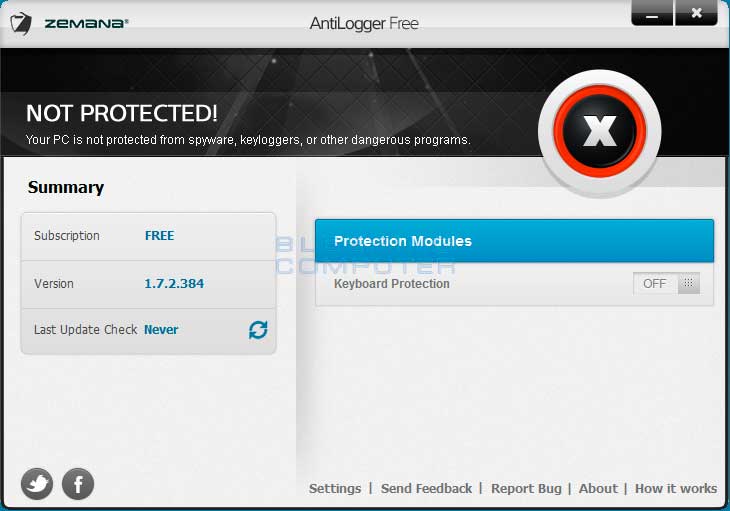
Read MoreScreenshots for Zemana AntiLogger Free BleepingComputer Review: Zemana AntiLogger Free is a program that protects your computer from keyloggers by encrypting your keystrokes. When a computer is infected with a keylogger it can see and record all keystrokes that you type on your computer. It can then log this information and send it to a…
Read MoreIn part two of this multi-part series on fake account creation bots, we look at why automation is used to create fake accounts and how they impact businesses. What is a Fake Account Creation Bot? A fake account creation bot is an automated computer program designed to create large numbers of fake accounts inside online…
Read MoreMutual Transport Layer Security (mTLS) allows two parties to authenticate each other during the initial connection of an SSL/TLS handshake. Source link lol
Read MoreRecent Posts
- AMD Takes On Intel, Apple And Nvidia With Ryzen AI Max Chips
- Vulnerability Summary for the Week of December 30, 2024 | CISA
- Intel: ‘Lead’ Intel 18A Product Set For Production In Second Half Of 2025
- Intel Slugs AMD, Qualcomm With Core Ultra 200V Chips For Commercial Laptops
- Tenable Chairman and CEO Amit Yoran Has Died