Month: April 2024
While ransomware attacks decreased after the LockBit and BlackCat disruptions, they have once again started to ramp up with other operations filling the void. A relatively new operation called RansomHub gained media attention this week after a BlackCat affiliate used the newer operation’s data leak site to extort Change HealthCare once again. Change HealthCare allegedly…
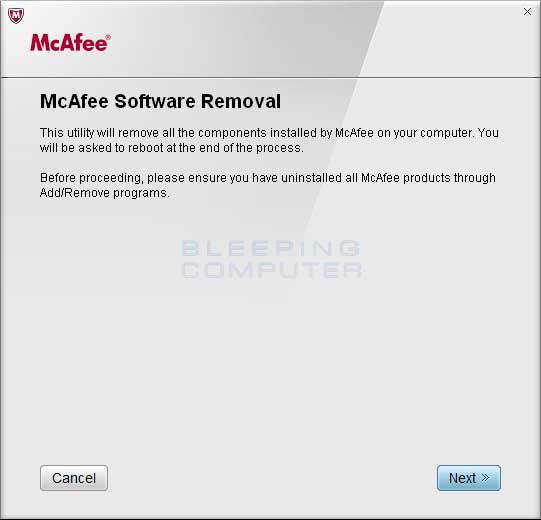
Read MoreScreenshots for McAfee Consumer Products Removal tool BleepingComputer Review: The McAfee Consumer Products Removal tool allows you to remove component data of McAfee consumer products listed below on your windows system. This tool is to be used after uninstalling McAfee software through the windows installer tool. This tool will not run on Windows 98 or ME. Please note, that…
Read MoreTenable Expands Generative AI Capabilities for Faster Attack Path Analysis and Mitigation Guidance
by nlqip
Tenable®, the Exposure Management company, today announced innovative enhancements to ExposureAI, the generative AI capabilities and services within its Tenable One Exposure Management Platform. The new features enable customers to quickly summarize relevant attack paths, ask questions of an AI assistant and receive specific mitigation guidance to act on intelligence and reduce risk. The platform’s generative AI-powered search…
Read MoreTry Tenable Web App Scanning Enjoy full access to our latest web application scanning offering designed for modern applications as part of the Tenable One Exposure Management platform. Safely scan your entire online portfolio for vulnerabilities with a high degree of accuracy without heavy manual effort or disruption to critical web applications. Sign up now.…
Read MoreCisco Hypershield For AI Data Center, Cloud Security ‘The Most Consequential’ Announcement In Cisco’s 40-Year History: Execs
by nlqip
‘With this innovation … we have actually been able to deliver something that’s unlike anything we’ve done in the last 40 years at Cisco. And I will say that we’re just getting started,’ says Jeetu Patel, Cisco’s EVP and general manager of security and collaboration on Cisco Hypershield. Cisco Systems has introduced what the tech…
Read MoreWhy is an AI AUP important for business security? By defining acceptable behavior, data handling practices, and security protocols, an AI acceptable use policy helps mitigate risks, such as data breaches, malicious use of AI algorithms, and unauthorized access. Additionally, this policy promotes accountability and ensures that AI technologies are used ethically and responsibly, safeguarding…
Read MoreMedia Room
by nlqip
https://www.securityinsights.co.uk/podcast/cloud-security-an-identity-problem/ Source link lol
Read MoreYou know Tenable as a cybersecurity industry leader whose world-class exposure management products are trusted by our approximately 43,000 customers, including about 60% of the Fortune 500. But sometimes we like to give you a peek behind the curtain to share how we protect our own house against cyberattacks – and that’s what this blog…
Read MoreIntroduction Black Friday is a popular shopping event throughout the United States of America and around the world. During Thanksgiving weekend and Cyber Monday (the Monday after Thanksgiving), thousands of companies offer steep product discounts that are not available at any other time, and consumers rush to buy these items while they are available. This…
Read MoreWhat Is Authorization? Once a subject is authenticated, authorization (abbreviated as AuthZ) is the process of determining whether the given identity (for example, a user) is allowed to access the requested resource and, if so, what actions they are allowed to take. The goal is to give authenticated users access to the resources (such as…
Read More