Month: April 2024
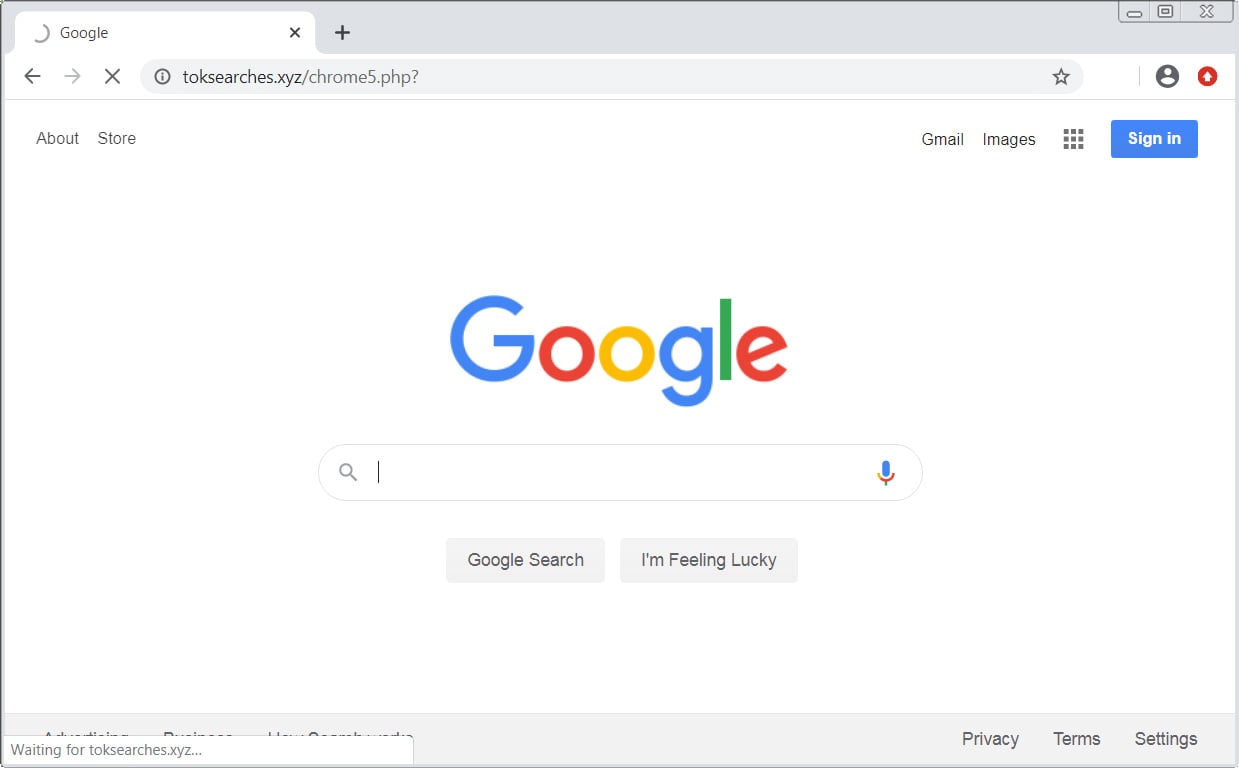
In order to remove Toksearches.xyz completely you will need to reset Chrome back to its initial settings. Doing these steps will erase all configuration information from Chrome such as your home page, tab settings, saved form information, browsing history, and cookies. This process will also disable any installed extensions. All of your bookmarks, though, will…
Read MoreDisclaimer It is assumed that users are familiar with the operating system they are using and comfortable with making the suggested changes. BleepingComputer.com will not be held responsible if changes you make cause a system failure. This is NOT a list of tasks/processes taken from Task Manager or the Close Program window (CTRL+ALT+DEL) but a…
Read MoreGartner recognizes 10 security service edge (SSE) vendors in its latest Magic Quadrant ranking for the cybersecurity category. Netskope, Palo Alto Networks and Zscaler once again appeared in the sought-after “Leaders” quadrant in the 2024 Gartner Magic Quadrant for security service edge (SSE) vendors, according to the report released Thursday. The three vendors in the…
Read More‘When you look at the whole class of ecosystem that’ll be built around AI, it’ll be one of the most exciting ecosystem shuffles in adding value that we’ve seen,’ Red Hat CEO Matt Hicks tells CRN. Red Hat CEO Matt Hicks told CRN that channel partners have an immense opportunity to add value and drive…
Read More“The customers that are coming from all of those competitors are saying the same thing, which is, ‘I want a beautifully well-engineered, elegantly written, modern architecture platform for my business,’” says Michael George, Syncro CEO. While Michael George knows competition is healthy, he believes Syncro’s toolset is perfectly aligned to help MSPs grow. “I’d like…
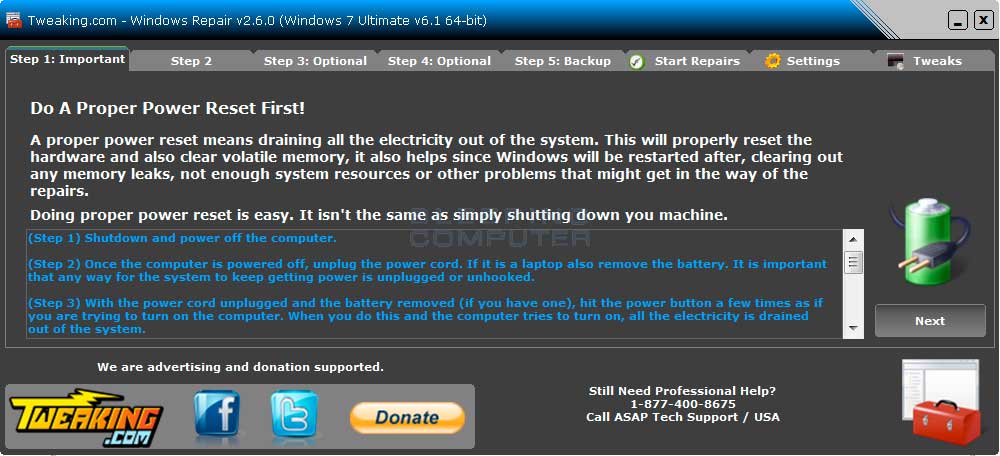
Read MoreScreenshots for Windows Repair (All In One) BleepingComputer Review: Windows Repair is a utility that contains numerous mini-fixes for Windows. This tool will allow you to repair common issues with your computer such as firewall, file permission, and Windows Update problems. When using this tool you can select the particular fixes you would like to…
Read MorePublished by Aghiath Chbib Results-oriented, adaptable, established executive equipped with 20 years of success driving global business in large, multimillion-dollar organizations and private start-ups. Extensive experience spearheading operations within complex, technology-driven environments ensuring adherence to organizational strategies and best practices. Expert at building and directing high- performing, cross-functional teams with a focus on leadership, collaboration,…
Read MoreApply appropriate updates provided by Ivanti to vulnerable systems immediately after appropriate testing. (M1051: Update Software) Safeguard 7.1 : Establish and Maintain a Vulnerability Management Process: Establish and maintain a documented vulnerability management process for enterprise assets. Review and update documentation annually, or when significant enterprise changes occur that could impact this Safeguard. Safeguard 7.2:…
Read MoreSUMMARY Note: This joint Cybersecurity Advisory (CSA) is part of an ongoing #StopRansomware effort to publish advisories for network defenders that detail various ransomware variants and ransomware threat actors. These #StopRansomware advisories include recently and historically observed tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) to help organizations protect against ransomware. Visit stopransomware.gov…
Read MoreTo ensure they have the most complete information about the security posture of assets, organizations should deploy scans that use credentials. Scans that use credentials and successfully authenticate on a system (and run with Local Security Checks enabled) return a more comprehensive set of data about the system. This Assurance Report Card (ARC) provides the…
Read More