Finland warns of Android malware attacks breaching bank accounts
by nlqip

Finland’s Transport and Communications Agency (Traficom) is warning about an ongoing Android malware campaign attempting to breach online bank accounts.
The agency has highlighted multiple cases of SMS messages written in Finnish that instruct recipients to call a number. The scammer who answers the call instructs victims to install a McAfee app for protection.
The messages are supposedly sent from banks or payment service providers like MobilePay, and they use spoofing technology to appear as if they come from a domestic telecom operator or local network.
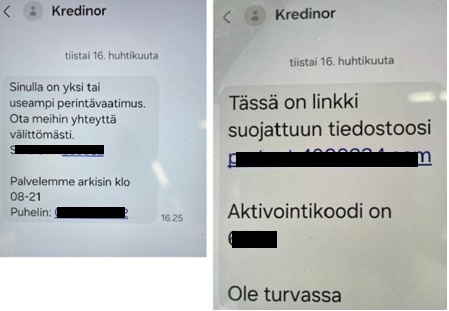
Source: OP Financial Group
However, the McAfee app is malware that will allow threat actors to breach victim’s bank accounts.
“According to reports received by the Cyber Security Center, targets are encouraged to download a McAfee application,” reads the notice. (machine translated)
“The download link offers an .apk application hosted outside the app store for Android devices. However, this is not antivirus software but malware to be installed on the phone.”
The OP Financial Group, a major financial service provider in the country, has also issued an alert on its website about the deceitful messages impersonating banks or national authorities.
The police also highlighted the threat, warning that the malware enables its operators to log in to the victim’s banking account and transfer money. In one case, a victim lost 95,000 euros ($102,000).
Traficom says the campaign targets exclusively Android devices, and there’s no separate infection chain for Apple iPhone users.
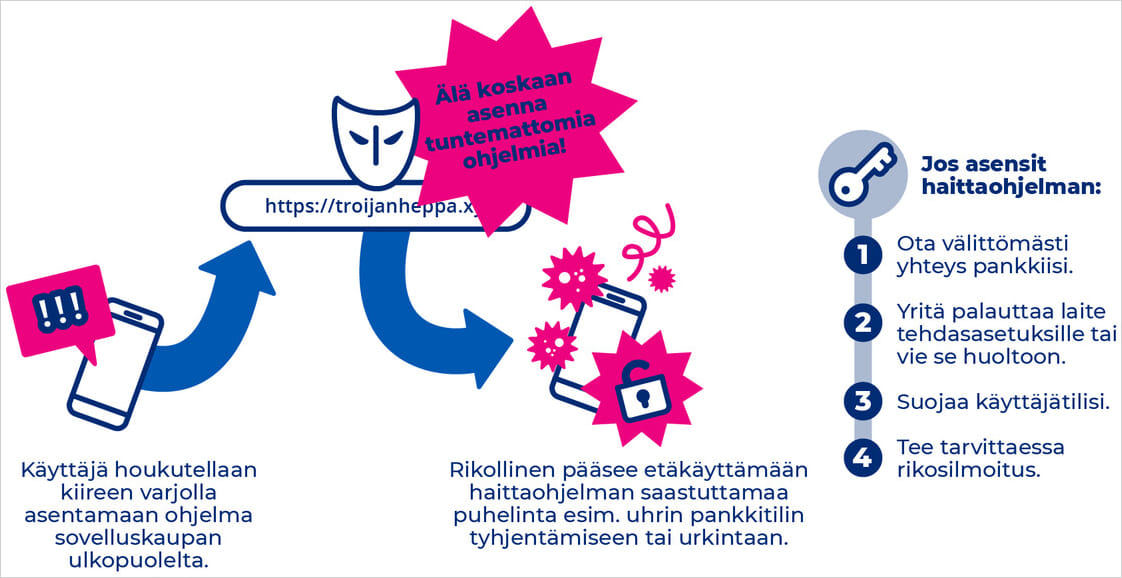
Source: Traficom
Vultur trojan suspected
Although the authorities in Finland haven’t determined the type of malware and have not shared any hashes or IDs for the APK files, the attacks resemble those Fox-IT analysts recently reported in connection to a new version of the Vultur trojan.
The new Vultur version entered circulation recently, using hybrid smishing and phone call attacks to convince targets to download a fake McAfee Security app, which introduces the final payload in three separate parts for evasion.
Its latest features include extensive file management operations, abuse of Accessibility Services, blocking of specific apps from executing on the device, disabling Keyguard, and serving custom notifications in the status bar.
If you have installed the malware, you should contact your bank immediately to enable protection measures and restore “factory settings” on the infected Android device to wipe all data and apps.
OP says they don’t ask customers to share any sensitive data over the phone or install any app to be able to receive or cancel payments, so similar requests should be immediately reported to the bank’s customer service and the police.
Google has previously confirmed to BleepingComputer that Android’s in-built anti-malware tool, Play Protect, automatically protects against known versions of Vultur, so keeping it active at all times is crucial.
Source link
lol
Finland’s Transport and Communications Agency (Traficom) is warning about an ongoing Android malware campaign attempting to breach online bank accounts. The agency has highlighted multiple cases of SMS messages written in Finnish that instruct recipients to call a number. The scammer who answers the call instructs victims to install a McAfee app for protection. The…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
