New BIG-IP Next Central Manager bugs allow device takeover
by nlqip

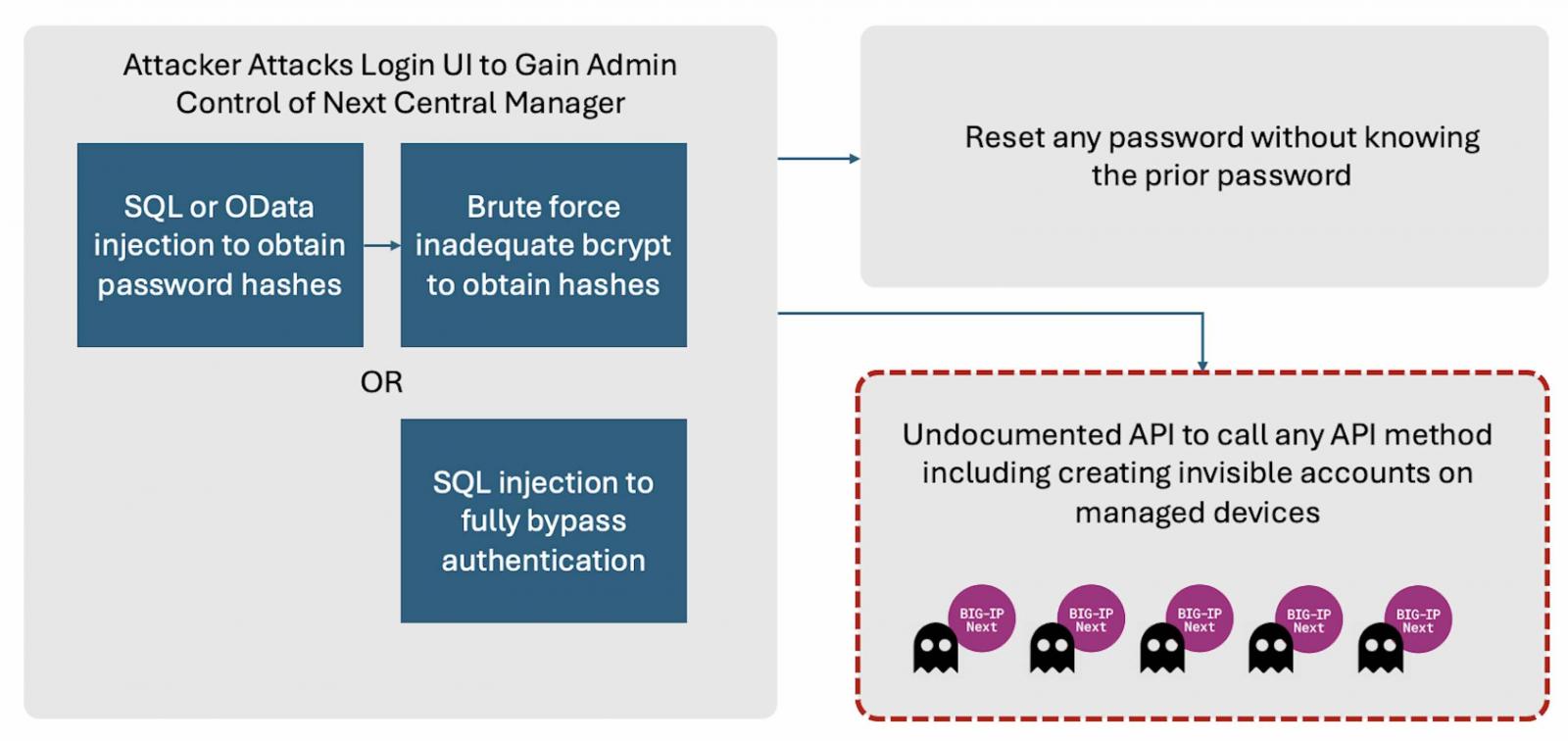
F5 has fixed two high-severity BIG-IP Next Central Manager vulnerabilities, which can be exploited to gain admin control and create hidden rogue accounts on any managed assets.
Next Central Manager allows administrators to control on-premises or cloud BIG-IP Next instances and services via a unified management user interface.
The flaws are an SQL injection vulnerability (CVE-2024-26026) and an OData injection vulnerability (CVE-2024-21793) found in the BIG-IP Next Central Manager API that would allow unauthenticated attackers to execute malicious SQL statements on unpatched devices remotely.
SQL injection attacks involve injecting malicious SQL queries into input fields or parameters in database queries. This exploits vulnerabilities in the application’s security and allows unintended SQL commands to execute, resulting in unauthorized access, data breaches, and system takeovers.
Supply chain security firm Eclypsium, which reported the flaws and shared a proof-of-concept exploit on Wednesday, says that rogue accounts created after compromising an unpatched instance are not visible from Next Central Manager and can thus be used for malicious persistence within a victim’s environment.
“The management console of the Central Manager can be remotely exploited by any attacker able to access the administrative UI via CVE 2024-21793 or CVE 2024-26026. This would result in full administrative control of the manager itself,” Eclypsium says.
“Attackers can then take advantage of the other vulnerabilities to create new accounts on any BIG-IP Next asset managed by the Central Manager. Notably, these new malicious accounts would not be visible from the Central Manager itself.”
PoC exploit and temporary mitigation available
According to F5’s recommendations, administrators who can’t immediately install today’s security updates should restrict Next Central Manager access to trusted users over a secure network to mitigate attack risks.
Luckily, according to Eclypsium, there is no evidence that the two security vulnerabilities have been exploited in attacks.
While adoption rates for F5’s BIG-IP Next Central Manager are currently unknown, Shodan currently tracks over 10,000 F5 BIG-IP devices with management ports exposed online.
In November, F5 warned customers that “skilled” attackers were exploiting two critical BIG-IP vulnerabilities (CVE-2023-46747 and CVE-2023-46748) fixed one month before to hack into unpatched devices, executing malicious code and erasing signs of the breach.
Two years ago, CISA also cautioned of widespread exploitation of another F5 BIG-IP flaw (CVE-2022-1388)—also allowing device takeover—across government and private sector networks and shared guidance to block the ongoing attacks.
Source link
lol
F5 has fixed two high-severity BIG-IP Next Central Manager vulnerabilities, which can be exploited to gain admin control and create hidden rogue accounts on any managed assets. Next Central Manager allows administrators to control on-premises or cloud BIG-IP Next instances and services via a unified management user interface. The flaws are an SQL injection vulnerability…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
