Widely used Telit Cinterion modems open to SMS takeover attacks
by nlqip

Security flaws in Telit Cinterion cellular modems, widely used in sectors including industrial, healthcare, and telecommunications, could allow remote attackers to execute arbitrary code via SMS.
A set of eight separate issues, seven of them with identifiers CVE-2023-47610 through CVE-2023-47616 and another that has yet to be registered, were disclosed last November by security researchers at Kaspersky’s ICS CERT division.
Before publishing the security issues, the security company had reported them to the vendor in February 2023.
On Saturday, at the OffensiveCon conference in Berlin, Alexander Kozlov and Sergey Anufrienko will be providing low level technical details about the security issues and how a threat actor could exploit them to take control of vulnerable Telit Cinterion devices.
SMS to device takeover
The most severe of the vulnerabilities is CVE-2023-47610, a heap overflow problem that affects the modem’s User Plane Location (SUPL) message handlers.
Kaspersky, in collaboration with Telit and based on a thorough analysis of the technical details, assigned it a severity score of 8.8 out of the maximum 10. However, NIST’s assessment is that the issue has critical impact and received a severity score of 9.8.
Attackers exploiting the flaw via specially crafted SMS messages could trigger the vulnerability and execute arbitrary code remotely on the modem without requiring authentication.
In a report shared with BleepingComputer, the researchers say that the SMS messaging interface is present on all modems and that accessing it is possible if the subscriber number of the target modem in the cellular operator’s network is known.
They explain that operator restrictions may sometimes prevent sending binary SMS but a fake base station should bypass this limitation.
“According to the transmission protocol, the ULPSizeFromPacket and wapTpduLen variables are calculated independently,” the researchers note in the technical report.
“These variables are interrelated only in the part of WAP messages reception algorithm: the sum of the sizes of all received WAP messages in a UPL message must not exceed ULPSizeFromPacket.”
“But the algorithm used to receive WAP messages does not check it. Therefore, a received WAP packet of size wapTpduLen will be copied to a buffer of size ULPSizeFromPacket.”
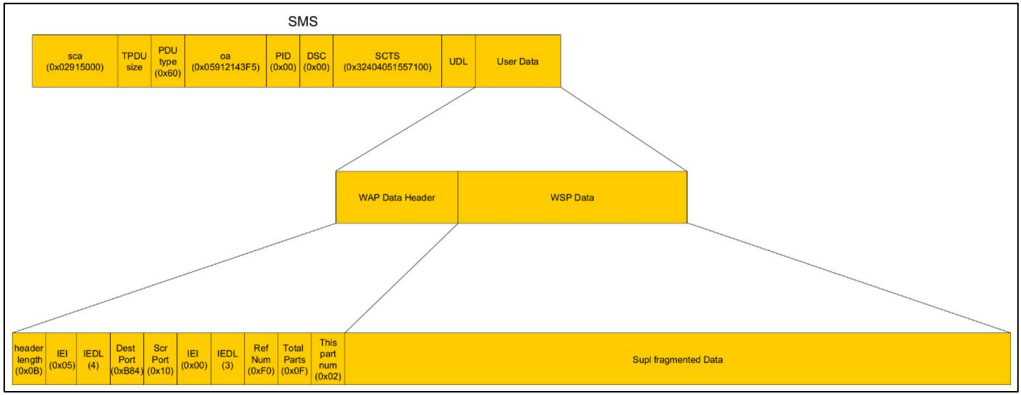
Source: Kaspersky
By exploiting CVE-2023-47610 to execute arbitrary code via SMS, an attacker can get deep-level access to the modem’s operating system.
“This access also facilitates the manipulation of RAM and flash memory, increasing the potential to seize complete control over the modem’s functionalities—all without authentication or requiring physical access to the device” – Kaspersky
Although the rest of the vulnerabilities that Kaspersky researchers discovered received a lower severity score, they can be used to compromise the integrity of MIDlets – Java-based applications with various functions.
According to Kaspersky, an attacker could achieve code execution with elevated privileges (manufacturer level) by circumventing digital signature checks (CVE-2023-47611). This would pose a threat not just to data confidentiality and integrity but also to broader network security and device integrity.
Although the research targeted the Cinterion EHS5-E series modem, because other products from the vendor have similar software and hardware architecture additional variants are also impacted:
- Cinterion BGS5
- Cinterion EHS5/6/7
- Cinterion PDS5/6/8
- Cinterion ELS61/81
- Cinterion PLS62
Telit fixed some of the disclosed vulnerabilities but some remain unpatched, Kaspersky told BleepingComputer.
“The vulnerabilities we found, coupled with the widespread deployment of these devices in various sectors, highlight the potential for extensive global disruption,” says Evgeny Goncharov, head of Kaspersky ICS CERT.
Goncharov notes that because the modems are embedded in other solutions, it is a challenge to determine which products are impacted.
The security company has some recommendations to mitigate the threats, which is most of the times possible by working with the telecom operator. One strategy is to disable SMS sending to impacted devices and using a securely configured private APN.
Kaspersky also recommends enforcing application signature verification to prevent the installation of untrusted MIDIets on the modem and take measures to prevent unauthorized physical access to the devices.
Source link
lol
Security flaws in Telit Cinterion cellular modems, widely used in sectors including industrial, healthcare, and telecommunications, could allow remote attackers to execute arbitrary code via SMS. A set of eight separate issues, seven of them with identifiers CVE-2023-47610 through CVE-2023-47616 and another that has yet to be registered, were disclosed last November by security researchers…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
