CISA: Black Basta ransomware breached over 500 orgs worldwide
by nlqip

CISA and the FBI said today that Black Basta ransomware affiliates breached over 500 organizations between April 2022 and May 2024.
In a joint report published in collaboration with the Department of Health and Human Services (HHS) and the Multi-State Information Sharing and Analysis Center (MS-ISAC), the two federal agencies added that the gang also encrypted and stole data from at least 12 out of 16 critical infrastructure sectors.
“Black Basta affiliates have targeted over 500 private industry and critical infrastructure entities, including healthcare organizations, in North America, Europe, and Australia,” CISA said.
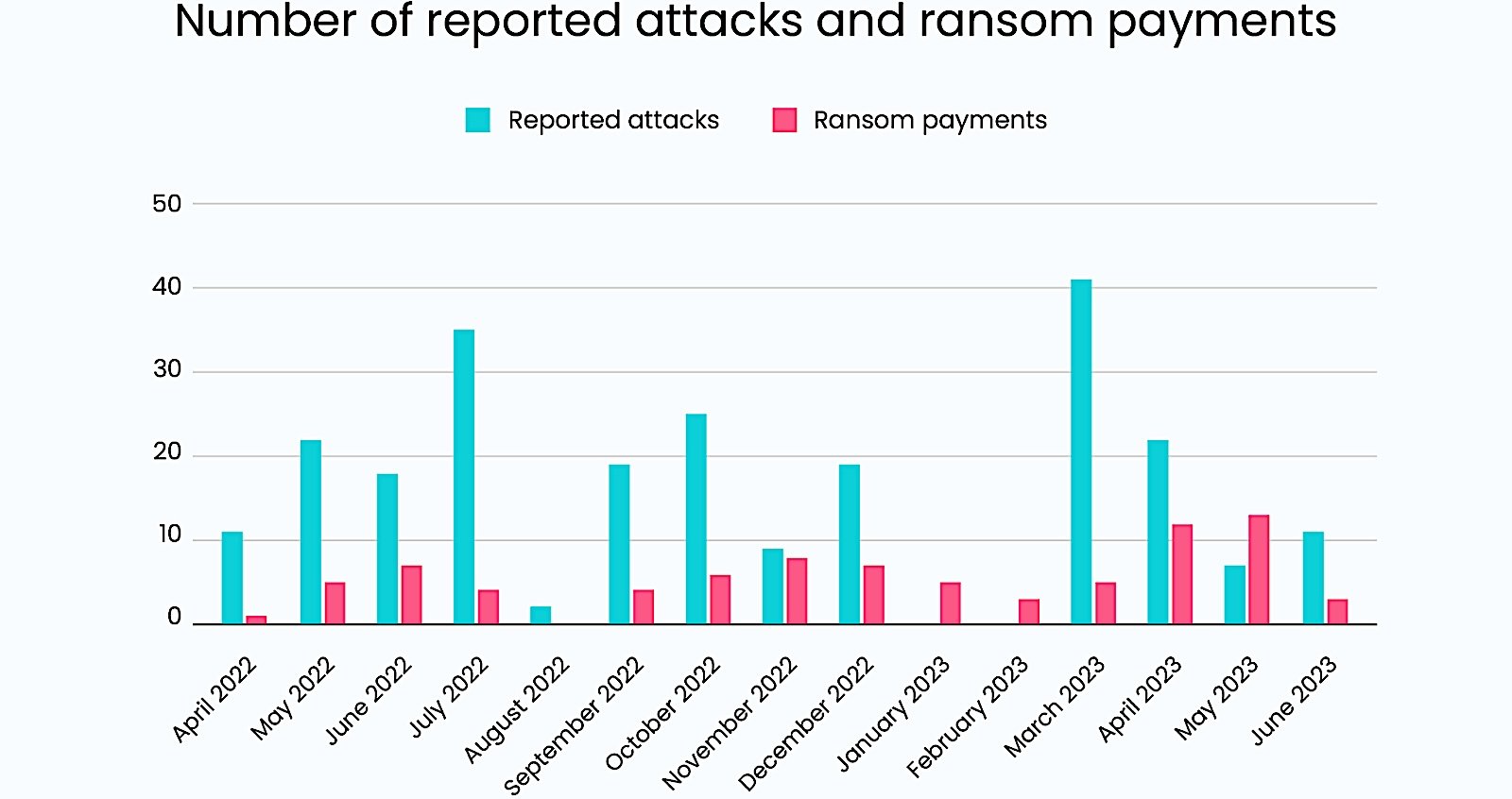
While the federal agencies didn’t share what prompted today’s advisory, Black Basta was linked this week to a suspected ransomware attack that hit the systems of healthcare giant Ascension, forcing the U.S. healthcare network to redirect ambulances to unaffected facilities.
On Friday, Health-ISAC (Information Sharing and Analysis Center) also issued a threat bulletin warning that the Black Basta ransomware gang “has recently accelerated attacks against the healthcare sector.”
Black Basta emerged as a Ransomware-as-a-Service (RaaS) operation in April 2022. Its affiliates have since breached many high-profile victims, including German defense contractor Rheinmetall, Hyundai’s European division, U.K. technology outsourcing company Capita, industrial automation company and government contractor ABB, the Toronto Public Library, the American Dental Association, Sobeys, Knauf, and Yellow Pages Canada.
After the Conti cybercrime syndicate shut down in June 2022 following a series of embarrassing data breaches, it split into multiple groups, one of these factions believed to be Black Basta.
“The threat group’s prolific targeting of at least 20 victims in its first two weeks of operation indicates that it is experienced in ransomware and has a steady source of initial access,” the Department of Health and Human Services security team said in a March 2023 report.
“The level of sophistication by its proficient ransomware operators, and reluctance to recruit or advertise on Dark Web forums, supports why many suspect the nascent Black Basta may even be a rebrand of the Russian-speaking RaaS threat group Conti, or also linked to other Russian-speaking cyber threat groups.”
According to Elliptic and Corvus Insurance research, this Russian-linked ransomware gang has also raked in at least $100 million in ransom payments from more than 90 victims until November 2023.
The joint advisory also provides defenders tactics, techniques, and procedures (TTPs) and indicators of compromise (IOCs) used by Black Basta affiliates and identified during FBI investigations.
Defenders should keep operating systems, software, and firmware up-to-date, require phishing-resistant Multi-Factor Authentication (MFA) for as many services as possible, and train users to recognize and report phishing attempts to mitigate Black Basta ransomware attack risks.
They should also secure remote access software by applying CISA-recommended mitigations, making backups of device configurations and critical systems as often as possible to enable faster repairs and restoration, and implementing mitigations shared in the StopRansomware Guide.
The agencies specifically highlighted the increased risks healthcare orgs are facing from this ransomware operation and urged them to ensure that these recommended mitigations are applied to block potential attacks.
“Healthcare organizations are attractive targets for cybercrime actors due to their size, technological dependence, access to personal health information, and unique impacts from patient care disruptions,” CISA and the FBI warned.
“The authoring organizations urge HPH Sector and all critical infrastructure organizations to apply the recommendations in the Mitigations section of this CSA to reduce the likelihood of compromise from Black Basta and other ransomware attacks.”
Source link
lol
CISA and the FBI said today that Black Basta ransomware affiliates breached over 500 organizations between April 2022 and May 2024. In a joint report published in collaboration with the Department of Health and Human Services (HHS) and the Multi-State Information Sharing and Analysis Center (MS-ISAC), the two federal agencies added that the gang also…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
