Russian hackers use new Lunar malware to breach a European govt’s agencies
by nlqip

Security researchers discovered two previously unseen backdoors dubbed LunarWeb and LunarMail that were used to compromise a European government’s diplomatic institutions abroad.
The pieces of malware have been used to breach the Ministry of Foreign Affairs of a European country with diplomatic missions in the Middle East and have been active since at least 2020.
Researchers at cybersecurity company ESET believe that the backdoors may be connected to the Russian state-sponsored hacker group Turla, although attribution has medium confidence at this point.
Lunar attack chain
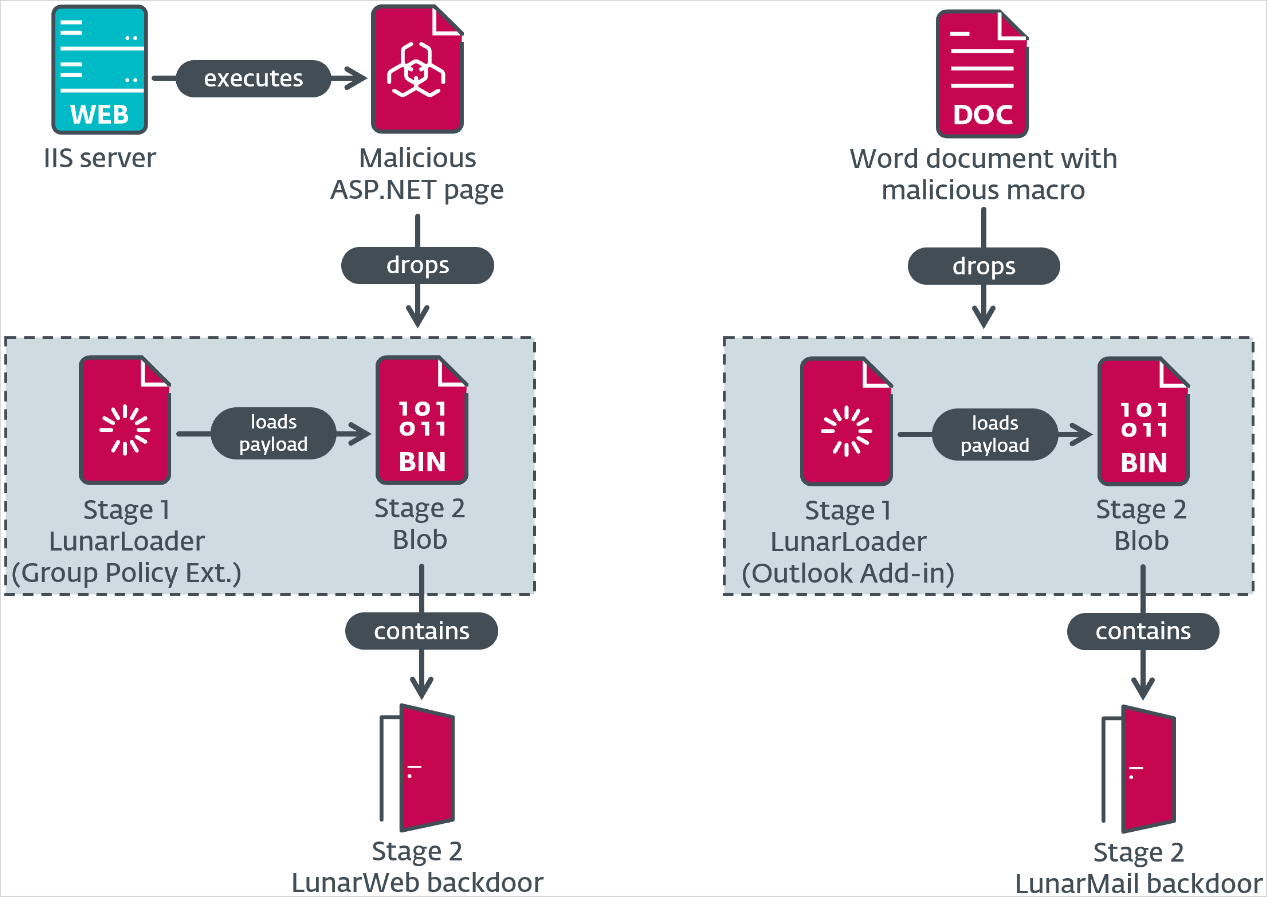
In its report, ESET says that the attack starts with spear-phishing emails that carry Word files with malicious macro code to install the LunarMail backdoor onto the target system.
The VBA macro also establishes persistence on the infected host by creating an Outlook add-in, ensuring it is activated whenever the email client is launched.
Source: ESET
ESET analysts have also seen evidence pointing to the potential abuse of a misconfigured open-source network monitoring tool Zabbix to drop the LunarWeb payload.
Specifically, a component mimicking a Zabbix agent log is deployed on a server, and when accessed with a specific password via an HTTP request, it decrypts and executes the loader and backdoor components.
LunarWeb persists on the breached device using several techniques that include creating Group Policy extensions, replacing system DLLs, and deploying as part of legitimate software.
Both payloads are decrypted by a malware loader that the researchers called ‘LunarLoader’ from an encrypted blob using the RC4 and AES-256 ciphers. The loader uses the DNS domain name for decryption and ensures that it runs only within the targeted environment.
Once the Lunar backdoors are running on the host, the attackers may send commands directly via the command and control (C2) server and use stolen credentials and compromised domain controllers for lateral movement on the network.
Source: ESET
LunarWeb and LunarMail
The two Lunar backdoors are designed for prolonged and covert surveillance, data theft, and maintaining control over compromised systems, such as high-value targets like government and diplomatic institutions.
LunarWeb is deployed on servers, mimicking legitimate traffic by spoofing HTTP headers from Windows and ESET product updates.
It receives commands for execution which are hidden in .JPG and .GIF image files using the steganopraphy technique.
The commands LunarWeb supports include executing shell and PowerShell commands, collecting system information, running Lua code, zipping files, and exfiltrating data in AES-256 encrypted form.
ESET researchers say that they observed an attack where the threat actor dropped LunarWeb at three diplomatic institutions of the targeted European Ministry of Foreign Affairs just minutes apart.
The attacker may have been able to move this quickly because they had previously gained access to the domain controller of the ministry and leveraged it to move to machines from other institutions on the network.
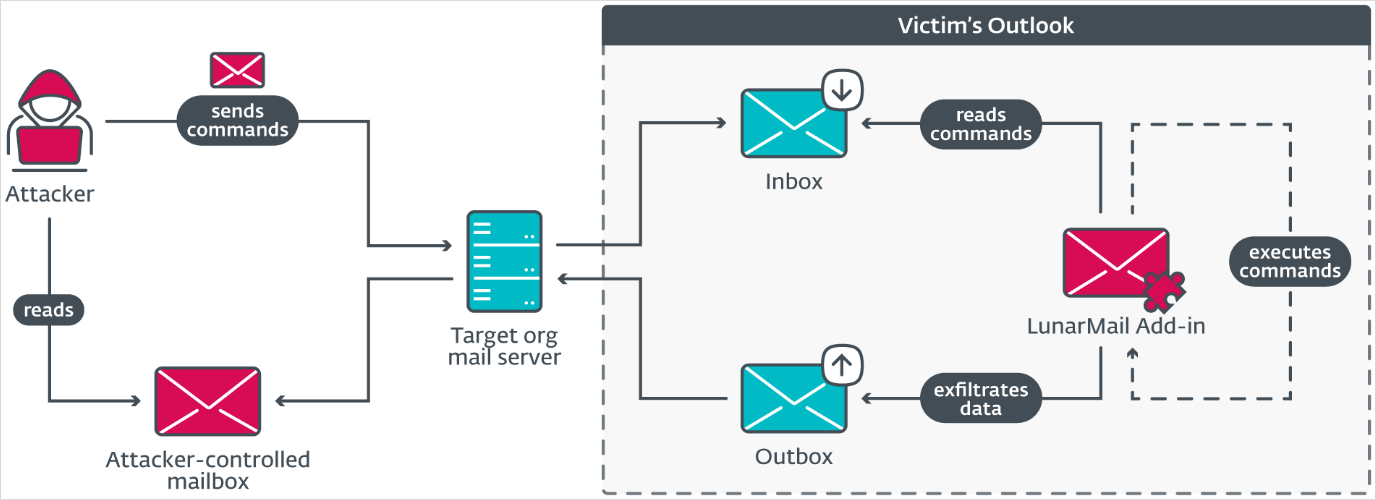
LunarMail is deployed on user workstations with Microsoft Outlook installed.
It uses an email-based communication system (Outlook MAPI) for data exchange with specific Outlook profiles linked to the C2 to evade detection in environments where HTTPS traffic may be more closely monitored.
Commands sent from the C2 are embedded in email attachments, typically hidden in .PNG images, which the backdoor parses to extract the hidden instructions.
LunarMail can create processes, take screenshots, write files, and run Lua code. Lua script execution allows it to indirectly run shell and PowerShell commands if needed.
Source: ESET
Based on similarities in observed tactics, techniques, and procedures (TTPs) between the Lunar toolset and and past activities, ESET attributes the backdoors to the Russian hacking group Turla with medium confidence.
However, the researchers noticed “varying degrees of sophistication in the compromises,” which suggests that the tools were developed and operated by multiple individuals.
Despite the intrusions being of a more recent date, ESET found artifacts indicating that the backdoors have been used in operations and evaded detection since at least 2020.
The cybersecurity company is providing a list of indicators of compromise (IoCs) for files, file paths, network, and registry keys observed in compromised environments. A complete list is available here.
Source link
lol
Security researchers discovered two previously unseen backdoors dubbed LunarWeb and LunarMail that were used to compromise a European government’s diplomatic institutions abroad. The pieces of malware have been used to breach the Ministry of Foreign Affairs of a European country with diplomatic missions in the Middle East and have been active since at least 2020. Researchers at cybersecurity…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
