Arc browser’s Windows launch targeted by Google ads malvertising
by nlqip

A new Google Ads malvertising campaign, coinciding with the launch of the Arc web browser for Windows, was tricking people into downloading trojanized installers that infect them with malware payloads.
The Arc browser is a new web browser featuring an innovative user interface design that sets it apart from traditional browsers.
Launched in July 2023 for macOS and after receiving glowing reviews from tech publications and users, its recent launch on Windows was highly anticipated.
Cybercriminals target Arc for Windows launch
According to a report by Malwarebytes, cybercriminals prepared for the product launch, setting up malicious advertisements on Google Search to lure users looking to download the new web browser.
Google’s ad platform has a significant problem that allows threat actors to take out ads displaying legitimate URLs, which has been abused to target Amazon, Whales Market, WebEx, and Google’s own video platform, YouTube.
Malwarebytes found promoted results for the search terms “arc installer” and “arc browser windows” displaying the correct URL for Arc.
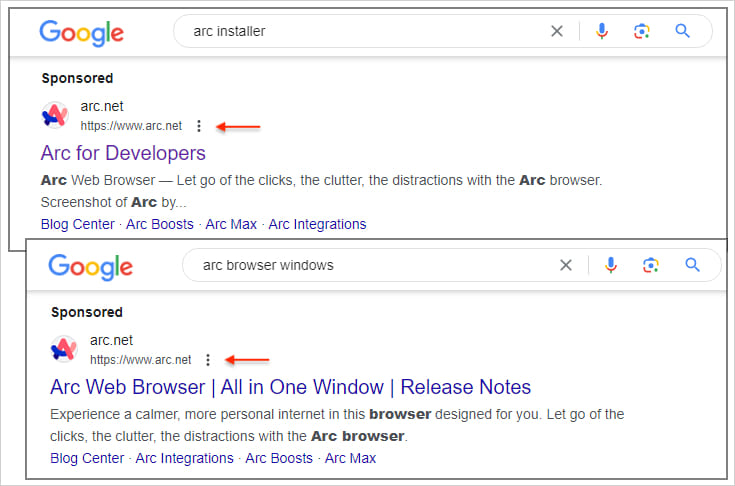
Source: Malwarebytes
However, after clicking the advertisement, searchers are redirected to typo-squatted domains that visually resemble the genuine website.
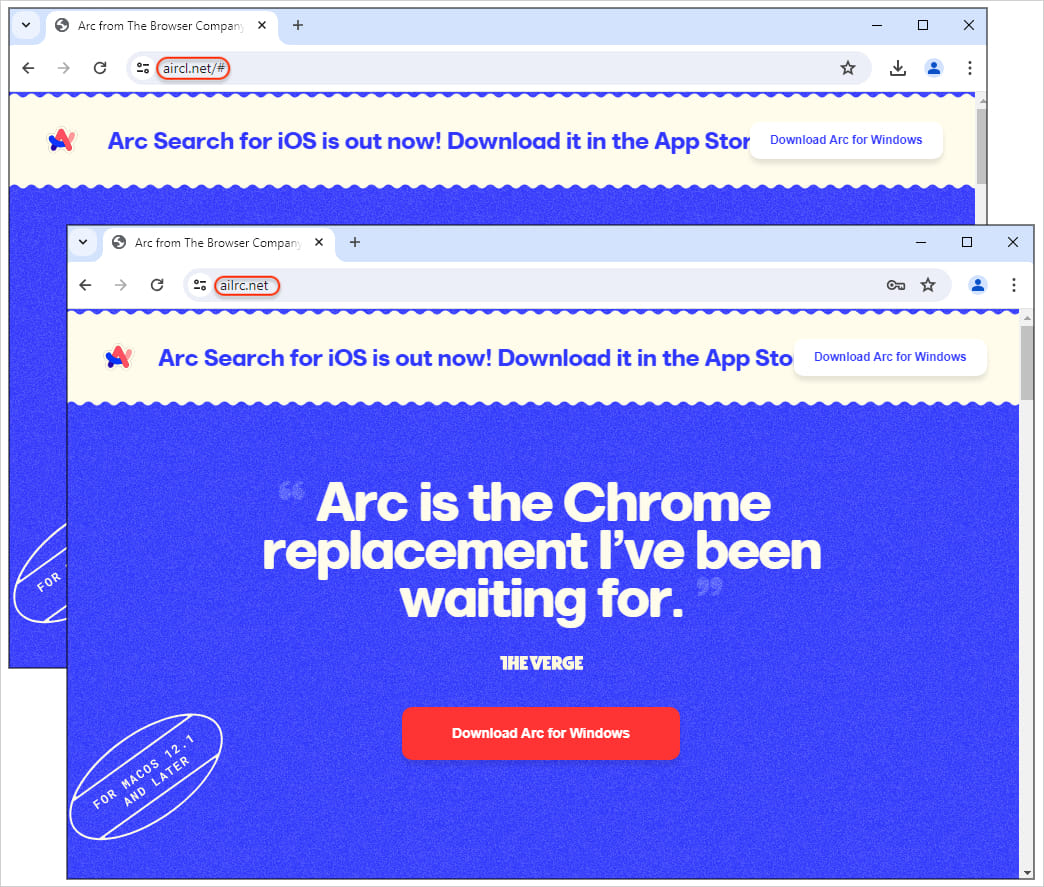
Source: Malwarebytes
If the “Download” button is clicked, a trojanized installer file is retrieved from the MEGA hosting platform, which downloads an additional malicious payload named ‘bootstrap.exe’ from an external resource.
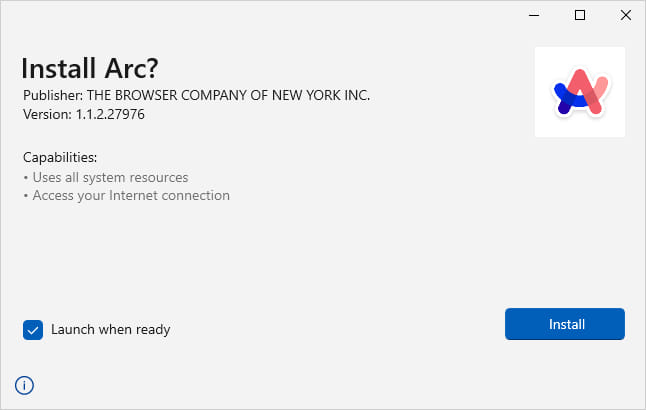
Source: Malwarebytes
MEGA’s API is abused for command and control (C2) operations, sending and receiving operational instructions and data.
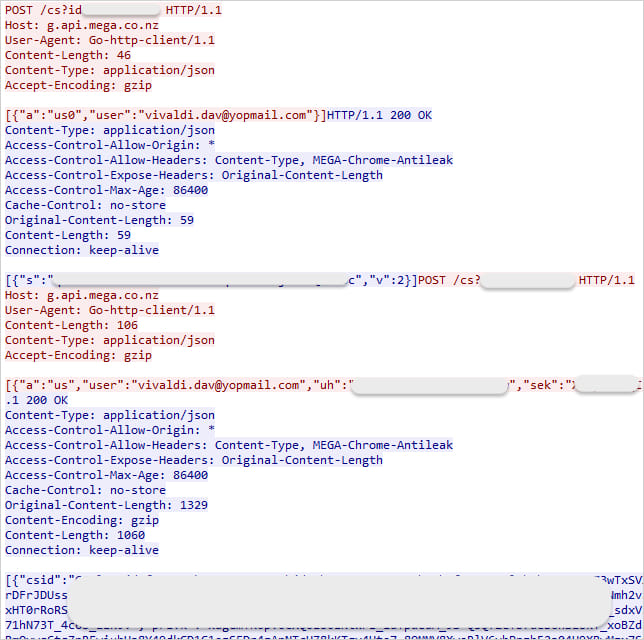
Source: Malwarebytes
The installer file fetches a PNG file containing malicious code that compiles and drops the final payload, ‘JRWeb.exe,’ onto the victim’s disk.
Malwarebytes also observed a separate infection chain that involves the installer using a Python executable to inject code into msbuild.exe, which queries an external site to retrieve commands for execution.
The analysts suggest that the final payload in these attacks is an info-stealer, though this hasn’t been determined yet.
Due to the Arc browser getting installed as expected on the victim’s machine and the malicious files running stealthily in the background, it’s unlikely for the victim to realize they have now become infected with malware.
Threat actors capitalizing on the hype surrounding new software/game launches isn’t new, but continues to be an effective method to distribute malware.
Users looking to download software should skip all promoted results on Google Search, use ad blockers that hide those results, and bookmark official project websites for future use.
Additionally, always verify the authenticity of the domains you’re about to download installers from, and always scan downloaded files on an up-to-date AV tool before executing them.
Source link
lol
A new Google Ads malvertising campaign, coinciding with the launch of the Arc web browser for Windows, was tricking people into downloading trojanized installers that infect them with malware payloads. The Arc browser is a new web browser featuring an innovative user interface design that sets it apart from traditional browsers. Launched in July 2023 for…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
