Europol on Thursday said it shut down the infrastructure associated with several malware loader operations such as IcedID, SystemBC, PikaBot, SmokeLoader, Bumblebee, and TrickBot as part of a coordinated law enforcement effort codenamed Operation Endgame.
“The actions focused on disrupting criminal services through arresting High Value Targets, taking down the criminal infrastructures and freezing illegal proceeds,” Europol said in a statement. “The malware […] facilitated attacks with ransomware and other malicious software.”
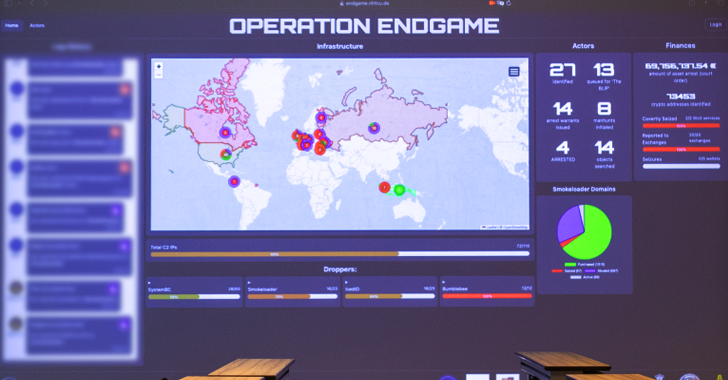
The action, which took place between May 27 and May 29, has resulted in the dismantling of over 100 servers worldwide and the arrest of four people, one in Armenia and three in Ukraine, following searches across 16 locations in Armenia, the Netherlands, Portugal, and Ukraine.
The servers, according to Europol, were located in Bulgaria, Canada, Germany, Lithuania, the Netherlands, Romania, Switzerland, Ukraine, the United Kingdom, and the United States. More than 2,000 domains have been confiscated by law enforcement.
One of the main suspects is alleged to have netted at least €69 million ($74.6 million) by renting out criminal infrastructure sites to deploy ransomware.
“Via so-called ‘sinkholing’ techniques or the use of tools to access the systems of operators behind the malware, investigators managed to block and take down the botnets,” Eurojust said.
Separately, authorities are seeking the arrest of seven people associated with a criminal organization whose aim was to spread the TrickBot malware. An eighth person is suspected of being one of the ringleaders of the group behind SmokeLoader.
Loaders, also known as droppers, are malicious software designed to gain initial access and deliver additional payloads onto compromised systems, including ransomware variants. They are typically propagated via phishing campaigns, compromised sites, or bundled with popular software.
“Droppers are designed to avoid detection by security software,” Europol said. “They may use methods like obfuscating their code, running in memory without saving to disk, or impersonating legitimate software processes.”
“After deploying the additional malware, the dropper may either remain inactive or remove itself to evade detection, leaving the payload to carry out the intended malicious activities.”
The agency described the takedowns as the largest-ever operation against botnets, involving authorities from Armenia, Bulgaria, Denmark, France, Germany, Lithuania, the Netherlands, Portugal, Romania, Switzerland, Ukraine, the United Kingdom, and the United States.