Two-factor authentication (2FA) explained: How it works and how to enable it
by nlqip
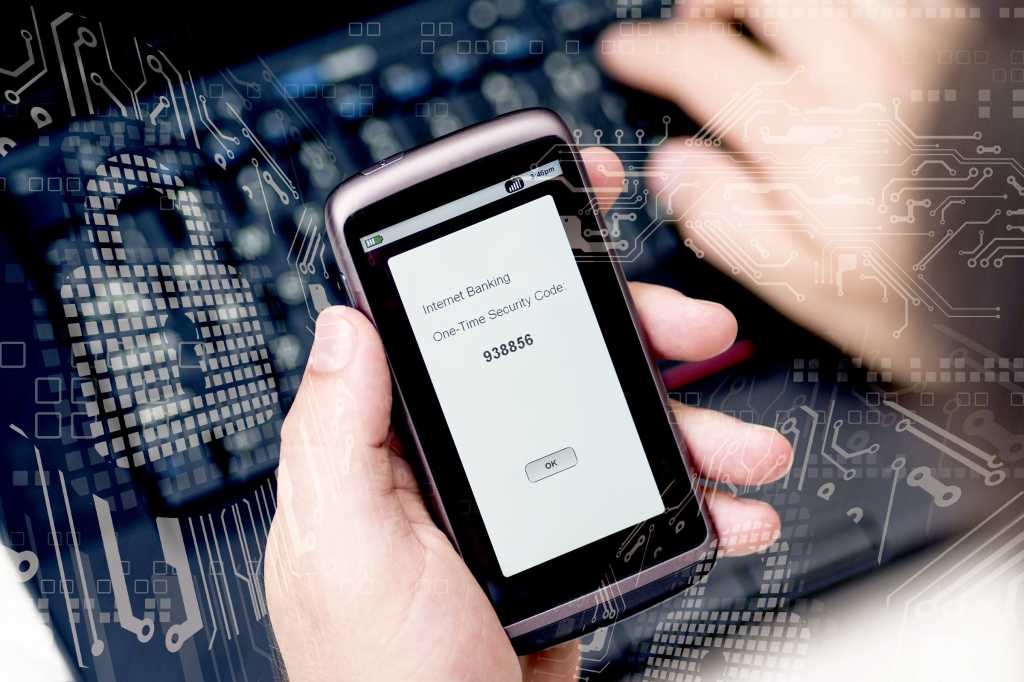
- Improved security: 2FA significantly reduces the risk of unauthorized access by including a second factor for identification beyond just a password. This added layer provides added security in the event that a password gets into the wrong hands.
- Compliance: Due to widespread breaches, some industries, such as defense, law enforcement, and government, have instituted regulations requiring access controls beyond passwords, including 2FA, to access specific systems or entities. Other industries, such as finance and healthcare, have regulations around data security and privacy that require addressing password security practices.
- Extra protection versus phishing: According to CISA, more than 90% of cyberattacks begin with phishing. Two-factor authentication provides another layer of defense, should an employee fall prey to a phishing attempt, compromising their password credentials.
- Customer ease-of-mind: While 2FA does require an extra hoop for customers to jump through to access their accounts, having 2FA in place for your organization’s services may help ease customer’s concerns about the safety of their data or transactions.
How does two-factor authentication work?
To understand what 2FA entails, you first need to know what a “factor” is in security access terminology. A factor is a piece of information required for authenticating an identity. Broadly speaking, factors can be broken down into six categories:
- Knowledge: This type of factor involves something the user knows, such as a password or answer to a security question.
- Possession: To validate a user’s identity, a security system can make use of something the user is expected to possess, such as a specific phone number or security token.
- Inherence: Biometrics, such as a fingerprint or facial recognition, can be used to authenticate a user based on something inherent to their identity.
- Behavior: This type of factor makes use of identifying features in behaviors specific to a user, such as voice recognition.
- Location: Geographic locations can also be used to authenticate a user, for example, through GPS or IP geolocation.
- Time: Time can also be involved as a factor, most often in conjunction with one of the above. For example, a one-time passcode (OTP) sent via text message to a device (possession) that has an authentication window of 5 minutes.
True 2FA pairs your first authentication factor — typically a password (i.e., knowledge) — with a second factor of an entirely different kind, such as:
- Something you have (possession)
- Something you are (inherence)
- Something you do (behavior)
- Somewhere you are (location)
Users will need to supply both factors to get access to their accounts.
On the back end, organizations deploying 2FA need to provide users with the requisite interfaces for providing both factors of identification, which can include integrating with SMS systems for sending OTPs to smartphones, making use of hardware biometic APIs on a laptop or handheld device, or development an app for smartphone platforms for second factor authentication, for example.
Organizations will also require an authentication server capable of verifying both factors employed. This server will also need to be integrated with the application or service that 2FA is meant to protect for allowing access.
Examples of authentication methods for 2FA
Given the myriad factors that can be used for 2FA, the range of possibilities for two-factor authentication is broad. Common methods include supplementing a password with one of the following:
Source link
lol
Improved security: 2FA significantly reduces the risk of unauthorized access by including a second factor for identification beyond just a password. This added layer provides added security in the event that a password gets into the wrong hands. Compliance: Due to widespread breaches, some industries, such as defense, law enforcement, and government, have instituted regulations…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
