Month: May 2024
Spear phishing, as the name implies, involves attempting to catch a specific fish. A spear phishing email includes information specific to the recipient to convince them to take the action the attacker wants them to take. This starts with the recipient’s name and may include information about their job or personal life that the attackers…
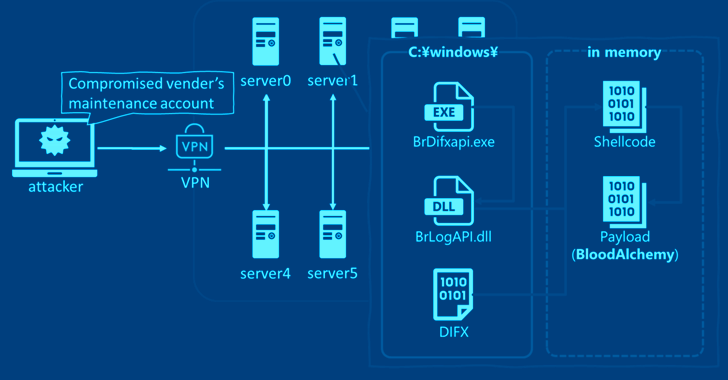
Read MoreMay 24, 2024NewsroomAPT Malware / Cyber Espionage Cybersecurity researchers have discovered that the malware known as BLOODALCHEMY used in attacks targeting government organizations in Southern and Southeastern Asia is in fact an updated version of Deed RAT, which is believed to be a successor to ShadowPad. “The origin of BLOODALCHEMY and Deed RAT is ShadowPad…
Read MoreMay 24, 2024NewsroomSupply Chain Attack / Malware Malicious actors have backdoored the installer associated with courtroom video recording software developed by Justice AV Solutions (JAVS) to deliver malware that’s associated with a known backdoor called RustDoor. The software supply chain attack, tracked as CVE-2024-4978, impacts JAVS Viewer v8.3.7, a component of the JAVS Suite 8…
Read MoreGoogle has released a new emergency security update to address the eighth zero-day vulnerability in Chrome browser confirmed to be actively exploited in the wild. The security issue was discovered internally by Google’s Clément Lecigne and is tracked as CVE-2024-5274. It is a high-severity ‘type confusion’ in V8, Chrome’s JavaScript engine responsible for executing JS…
Read MoreBut incidents such as these quickly lead to a loss of trust in the cybercriminal world and partners will quickly move on to the next program. This effect has been visible in LockBit’s recent activity. According to GuidePoint’s statistics, LockBit still accounted for 60% of ransomware incidents in March, but its market share dropped to…
Read MoreLogRhythm and Exabeam announce plan to merge May 15: Security intelligence and analytics firm LogRhythm, owned by private equity investment firm Thoma Bravo, will merge with competitor Exabeam, a provider of AI-driven security operations. “The combined company will leverage the complementary strengths from each organization to take AI-driven security operations to new heights,” Thoma Bravo…
Read MoreESET Research Available as both an IDA plugin and a Python script, Nimfilt helps to reverse engineer binaries compiled with the Nim programming language compiler by demangling package and function names, and applying structs to strings 23 May 2024 • , 5 min. read The Nim programming language has become increasingly attractive to malware developers…
Read MoreMicrosoft has released an emergency out-of-band (OOB) update for Windows Server 2019 that fixes a bug causing 0x800f0982 errors when attempting to install the May 2024 Patch Tuesday security updates. As reported by BleepingComputer last week, many system administrators have reported that they could not install this month’s Patch Tuesday security updates, receiving a 0x800f0982 when attempting to do so. “Yep, 6…
Read MoreThe homepage of Stark Industries Solutions. Two weeks before Russia invaded Ukraine in February 2022, a large, mysterious new Internet hosting firm called Stark Industries Solutions materialized and quickly became the epicenter of massive distributed denial-of-service (DDoS) attacks on government and commercial targets in Ukraine and Europe. An investigation into Stark Industries reveals it is…
Read MoreThe British Government is proposing sweeping change in its approach to ransomware attacks, proposing mandatory reporting by victims and licensing regime for all payments. Read more in my article on the Exponential-e blog. Source link lol
Read MoreRecent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict