Month: May 2024
Tenable®, the Exposure Management company, today announced Noam Dahan, a cloud security research manager for Tenable, will present at Identiverse 2024, taking place on May 28-31, 2024 in Las Vegas. Dahan will give an in-depth presentation on cloud identity and access management policies and guardrails that protect organizations from unknown threats and reduce risks…
Read MoreThe agreement to acquire IBM’s QRadar SaaS assets also opens the door for Palo Alto Networks to pursue the ‘much larger prize’ of migrating on-premises QRadar customers to XSIAM, CEO Nikesh Arora said Monday. Palo Alto Networks’ agreement to acquire IBM’s QRadar SaaS assets is poised to rapidly elevate the cybersecurity vendor’s position in the…
Read More‘Over the last 25 years, how many times have the analysts come and said print is dead. Print is declining. It’s shifting. It’s not going away. I don’t believe in our lifetime we’re going to see it disappear completely. And as a dealer, you just have to be ready to adapt to whatever changes. And…
Read MoreFile Integrity Monitoring (FIM) is an IT security control that monitors and detects file changes in computer systems. It helps organizations audit important files and system configurations by routinely scanning and verifying their integrity. Most information security standards mandate the use of FIM for businesses to ensure the integrity of their data. IT security compliance…
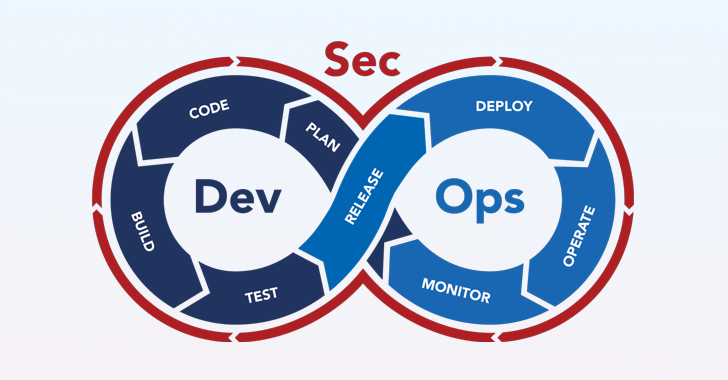
Read MoreOne of the enduring challenges of building modern applications is to make them more secure without disrupting high-velocity DevOps processes or degrading the developer experience. Today’s cyber threat landscape is rife with sophisticated attacks aimed at all different parts of the software supply chain and the urgency for software-producing organizations to adopt DevSecOps practices that…
Read MoreFrom its new generative AI tool IBM Concert to new offerings with AWS, Nvidia, Microsoft and more, here are the 10 biggest product launches today at IBM Think 2024 in Boston. IBM unleashed a slew of new products at IBM Think 2024 today—from its new generative AI tool IBM Concert to watsonx AI assistants, along…
Read MoreDetecting Malicious Trackers From Slashdot: Apple and Google have launched a new industry standard called “Detecting Unwanted Location Trackers” to combat the misuse of Bluetooth trackers for stalking. Starting Monday, iPhone and Android users will receive alerts when an unknown Bluetooth device is detected moving with them. The move comes after numerous cases of trackers…
Read MoreMay 21, 2024NewsroomSupply Chain Security / AI Model A critical security flaw has been disclosed in the llama_cpp_python Python package that could be exploited by threat actors to achieve arbitrary code execution. Tracked as CVE-2024-34359 (CVSS score: 9.7), the flaw has been codenamed Llama Drama by software supply chain security firm Checkmarx. “If exploited, it…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. 88% of cybersecurity professionals believe that artificial intelligence (AI) will significantly impact their jobs, according to a survey by the International Information System…
Read MoreMay 21, 2024NewsroomWindows 11 Security Microsoft on Monday confirmed its plans to deprecate NT LAN Manager (NTLM) in Windows 11 in the second half of the year, as it announced a slew of new security measures to harden the widely-used desktop operating system. “Deprecating NTLM has been a huge ask from our security community as…
Read MoreRecent Posts
- Bob Sullivan Discovers a Scam That Strikes Twice
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA