Month: May 2024
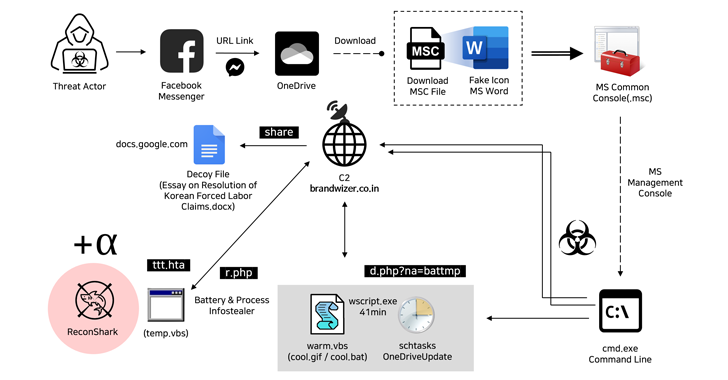
May 16, 2024NewsroomMalware / Cyber Espionage The North Korea-linked Kimsuky hacking group has been attributed to a new social engineering attack that employs fictitious Facebook accounts to targets via Messenger and ultimately delivers malware. “The threat actor created a Facebook account with a fake identity disguised as a public official working in the North Korean…
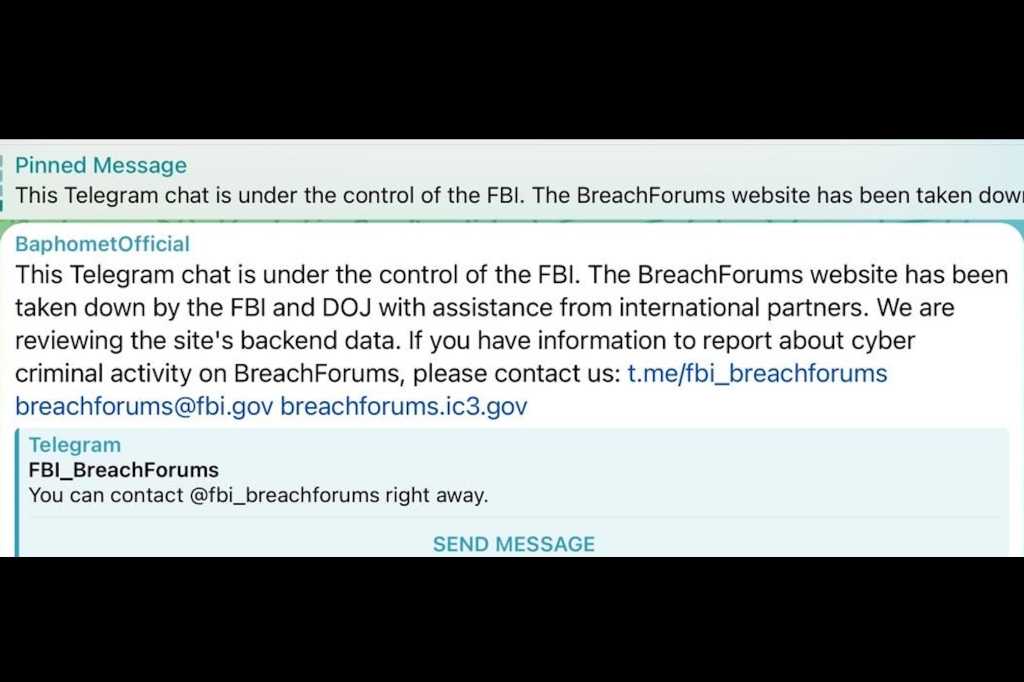
Read MoreThe seizure comes two days after IntelBroker, a prominent hacker on BreachForums, put up for sale some classified data stolen from one of Europol’s websites. The FBI’s claim that it is reviewing the hacking forum’s backend data is raising speculation regarding its possession of forum members’ email addresses, IP addresses, and private messages. “While details…
Read MoreThe North Korean hacker group Kimsuki has been using a new Linux malware called Gomir that is a version of the GoBear backdoor delivered via trojanized software installers. Kimsuky is a state-sponsored threat actor linked to North Korea’s military intelligence, the Reconnaissance General Bureau (RGB). In early February 2024, researchers at the SW2 threat intelligence company…
Read MoreThe North Korean hacker group Kimsuki has been using trojanized software packages to deliver a new Linux malware called Gomir in cyberespionage campaigns against targets in South Korea. Kimsuky is a state-sponsored threat actor linked to North Korea’s military intelligence, the Reconnaissance General Bureau (RGB). In early February 2024, researchers at the SW2 threat intelligence company…
Read MoreThe International Monetary Fund (IMF) Managing Director, Kristalina Georgieva, has sounded the alarm about the potentially disruptive impact of artificial intelligence (AI) on the global workforce. Speaking at a conference in London, Georgieva predicted a coming “tsunami” of job losses, driven by the rapid advancement of AI technologies. Georgieva’s warning highlights a growing concern among…
Read MoreThe company’s endpoint detection and response offering for iOS, Android and ChromeOS is positioned to help fill a major gap for MSPs, Lookout CEO Jim Dolce tells CRN. Lookout disclosed Thursday that it has become the first provider of mobile endpoint detection and response (EDR) to join the Pax8 cloud marketplace, in a bid to…
Read MoreBackground Cloud cryptomining has become an emerging trend in recent years, powered by the scalability and flexibility of cloud platforms. Unlike traditional on-premises infrastructure, cloud infrastructure allows attackers to quickly deploy resources for cryptomining, making it easier to exploit. One of the most common cryptomining threats for cloud environments is the Kinsing malware. Kinsing is…
Read MoreToday, Google announced new security features coming to Android 15 and Google Play Protect that will help block scams, fraud, and malware apps on users’ devices. Announced at Google I/O 2024, the new features are designed not only to help end users but also to warn developers when their apps have been tampered with. “Today, we’re announcing more new fraud and scam protection…
Read MoreZero-Trust DNS Microsoft is working on a promising-looking protocol to lock down DNS. ZTDNS aims to solve this decades-old problem by integrating the Windows DNS engine with the Windows Filtering Platform—the core component of the Windows Firewall—directly into client devices. Jake Williams, VP of research and development at consultancy Hunter Strategy, said the union of…
Read MoreGoogle has released a new emergency Chrome security update to address the third zero-day vulnerability exploited in attacks within a week. “Google is aware that an exploit for CVE-2024-4947 exists in the wild,” the search giant said in a security advisory published on Wednesday. The high-severity zero-day vulnerability (CVE-2024-4947) is caused by a type confusion…
Read More