Month: May 2024
‘I can’t get at it with our sellers alone. We need the channel as an extension of our sales force and they realize we are committed to them. It’s one plus one equals something much greater,’ Bill Scannell, Dell Technologies president of global sales and customer operations, tells CRN. Bill Scannell, Dell Technologies president of…
Read MoreMay 30, 2024NewsroomCyber Attack / Malware Cloudflare on Thursday said it took steps to disrupt a month-long phishing campaign orchestrated by a Russia-aligned threat actor called FlyingYeti targeting Ukraine. “The FlyingYeti campaign capitalized on anxiety over the potential loss of access to housing and utilities by enticing targets to open malicious files via debt-themed lures,”…
Read MoreFrom integrating Cisco Nexus to Lenovo’s infrastructure portfolio to engineering AI solutions together, here’s what you need to know about Lenovo and Cisco’s new agreement unveiled today. IT hardware giants Cisco and Lenovo are teaming up to jointly design and engineer integrated products around networking, purpose-built AI infrastructure and generative AI solutions. The two tech…
Read MoreThe company says the acquisition of BastionZero will enable Cloudflare to introduce ‘zero trust’ infrastructure access to its secure access service edge platform. Cloudflare announced Thursday that its acquisition of passwordless authentication startup BastionZero will enable it to introduce “zero trust” infrastructure access to its secure access service edge (SASE) platform. Boston-based BastionZero was founded…
Read MoreEverbridge, an American software company focused on crisis management and public warning solutions, notified customers that unknown attackers had accessed files containing business and user data in a recent corporate systems breach. The company provides public warning, crisis management, and risk intelligence services to over 6,500 customers worldwide, including the U.S. Army, the Hartsfield-Jackson Atlanta…
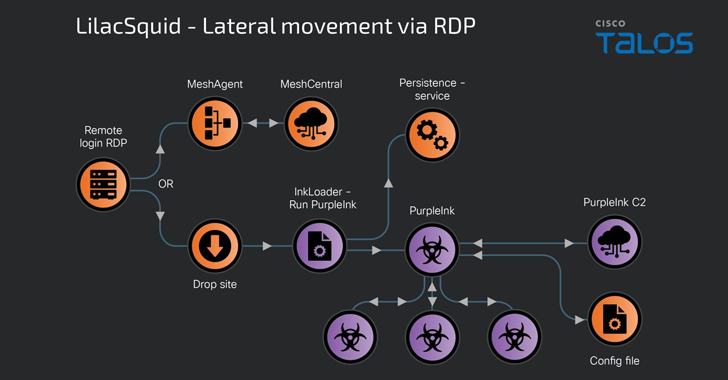
Read MoreMay 30, 2024NewsroomCyber Espionage / Threat Intelligence A previously undocumented cyber espionage-focused threat actor named LilacSquid has been linked to targeted attacks spanning various sectors in the United States (U.S.), Europe, and Asia as part of a data theft campaign since at least 2021. “The campaign is geared toward establishing long-term access to compromised victim…
Read MoreSmashing Security podcast #374: Microsoft’s Recall controversy, and the North Korean insider threat
by nlqip
Microsoft gets itself into a pickle with a privacy-popping new feature on its CoPilot+ PCs, the FTC warns of impersonated companies, and is your company hiring North Korean IT workers? All this and much much more is discussed in the latest edition of the “Smashing Security” podcast by cybersecurity veterans Graham Cluley and Carole Theriault,…
Read MoreWelcome to this week’s edition of the “Bi-Weekly Cyber Roundup” by Canary Trap. At Canary Trap, it is our mission to keep you up-to-date with the most crucial news in the world of cybersecurity and this bi-weekly publication is your gateway to the latest news. In this week’s roundup, we’ll begin with how Interpol is…
Read More‘As a group of powerful and amazing and capable women, it’s important for us to be lifting up and supporting other women,’ says Cass Cooper, columnist, inclusive leadership, for CRN. Leadership, mentorship or taking on a different role can have its challenges. Anything in the professional realm can be met with pushback, setbacks, failures and…
Read More“Customer data and metadata are the new gold for these enterprises,” Salesforce CEO Marc Benioff said Wednesday. Salesforce executives played up growth in the vendor’s artificial intelligence offerings while acknowledging continued “measured” customer buying patterns including longer sales cycles and smaller during the fiscal 2025 first quarter. Marc Benioff, CEO and co-founder of the San…
Read MoreRecent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA