Month: May 2024
May 14, 2024NewsroomNetwork Monitoring / Vulnerability The maintainers of the Cacti open-source network monitoring and fault management framework have addressed a dozen security flaws, including two critical issues that could lead to the execution of arbitrary code. The most severe of the vulnerabilities are listed below – CVE-2024-25641 (CVSS score: 9.1) – An arbitrary file…
Read MoreCybersecurity researchers have uncovered an ongoing social engineering campaign that bombards enterprises with spam emails with the goal of obtaining initial access to their environments for follow-on exploitation. “The incident involves a threat actor overwhelming a user’s email with junk and calling the user, offering assistance,” Rapid7 researchers Tyler McGraw, Thomas Elkins, and Evan McCann…
Read MoreMay 14, 2024The Hacker NewsCyber Threat / Machine Learning Deploying advanced authentication measures is key to helping organizations address their weakest cybersecurity link: their human users. Having some form of 2-factor authentication in place is a great start, but many organizations may not yet be in that spot or have the needed level of authentication…
Read MoreAnother Chrome Vulnerability Google has patched another Chrome zero-day: On Thursday, Google said an anonymous source notified it of the vulnerability. The vulnerability carries a severity rating of 8.8 out of 10. In response, Google said, it would be releasing versions 124.0.6367.201/.202 for macOS and Windows and 124.0.6367.201 for Linux in subsequent days. “Google is…
Read MoreCISA and Partners Release Guidance for Civil Society Organizations on Mitigating Cyber Threats with Limited Resources | CISA
by nlqip
CISA, in partnership with the Department of Homeland Security (DHS), the Federal Bureau of Investigation (FBI) and international partners, released Mitigating Cyber Threats with Limited Resources: Guidance for Civil Society. The joint guidance provides civil society organizations and individuals with recommended actions and mitigations to reduce the risk of cyber intrusions. Additionally, the guide encourages…
Read MoreBlack Basta ransomware group's techniques evolve, as FBI issues new warning in wake of hospital attack
by nlqip
Security agencies in the United States have issued a new warning about the Black Basta ransomware group, in the wake of a high-profile attack against the healthcare giant Ascension. The cyber attack last week forced the Ascension computer systems offline, and caused some hospital emergency departments to turn away ambulances “in order to ensure emergency…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. Today’s threat landscape is as dangerous as it has ever been. Global unrest, emerging technologies, and economic downturn all contribute to persistently high…
Read MoreMicrosoft’s cloud licensing practices are under fire once again, with critics alleging anti-competitive behavior and concerns about vendor lock-in. The controversy centers around the complexity and lack of transparency in Microsoft’s licensing terms, which are accused of favoring its own Azure cloud platform over competitors like Amazon Web Services (AWS) and Google Cloud Platform (GCP).…
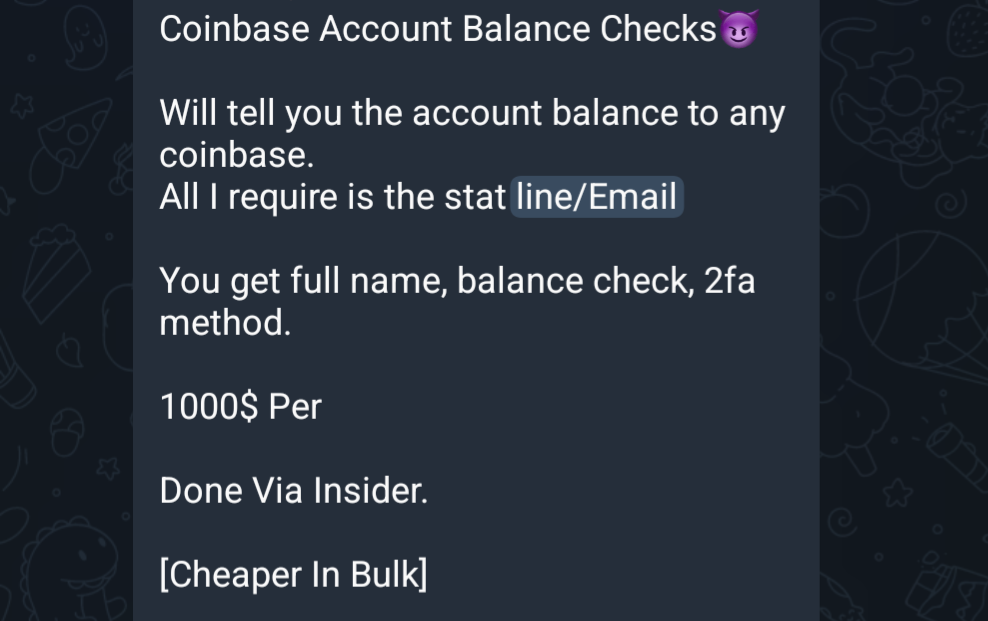
Read MoreA threat actor claimed that they have an access to Coinbase with ability to check the balance of any account. The advertisement shared in Telegram group. Coinbase is a leading cryptocurrency exchange platform founded in 2012, headquartered in the United States. It allows users to buy, sell, and store various cryptocurrencies like Bitcoin, Ethereum, and…
Read MoreGoogle has released emergency security updates for the Chrome browser to address a high-severity zero-day vulnerability tagged as exploited in attacks. This fix comes only three days after Google addressed another zero-day vulnerability in Chrome, CVE-2024-4671, caused by a use-after-free weakness in the Visuals component. The latest bug is tracked as CVE-2024-4761. It is an…
Read MoreRecent Posts
- Ivanti Releases Security Updates for Connect Secure, Policy Secure, and ZTA Gateways | CISA
- CISA Adds One Vulnerability to the KEV Catalog | CISA
- CVE-2025-0282: Ivanti Connect Secure Zero-Day Vulnerability Exploited In The Wild
- Google Cloud Hires Tech Superstar Francis DeSouza As New COO
- AWS Invests $11B In Georgia To ‘Support The Future Of AI’ Via Data Centers