Month: May 2024
Capgemini, Miracle Software Systems and Presidio were among the standout solution providers at Red Hat Summit 2024. One of the central messages throughout Red Hat’s Summit 2024 event was that the open source enterprise tools vendor sees solution providers as integral in meeting customer demand in multiple technology opportunities, including artificial intelligence and virtualization. During…
Read MoreMalicious Android apps masquerading as Google, Instagram, Snapchat, WhatsApp, and X (formerly Twitter) have been observed to steal users’ credentials from compromised devices. “This malware uses famous Android app icons to mislead users and trick victims into installing the malicious app on their devices,” the SonicWall Capture Labs threat research team said in a recent…
Read MoreThe type of information stolen is believed to include name, physical address, and purchase order details. No sensitive information breached On April 28, Menelik listed stolen data from Dell on BreachForum that included customer information with non-financial fields such as City, Full Name, Address, Province, Postal Code, Warranty plan, Company name, Dell Order Number, Dell…
Read MoreA guide to finding the right endpoint detection and response (EDR) solution for your business’ unique needs. Cybersecurity has become an ongoing battle between hackers and small- and mid-sized businesses. Though perimeter security measures like antivirus and firewalls have traditionally served as the frontlines of defense, the battleground has shifted to endpoints. This is why…
Read MoreMay 10, 2024NewsroomBrowser Security / Vulnerability Google on Thursday released security updates to address a zero-day flaw in Chrome that it said has been actively exploited in the wild. Tracked as CVE-2024-4671, the high-severity vulnerability has been described as a case of use-after-free in the Visuals component. It was reported by an anonymous researcher on…
Read MoreEven if you’ve got all the bells and whistles when it comes to securing your data center, your cloud deployments, your building’s physical security, and you’ve invested in defensive technologies, have the right security policies and processes in place and measure their effectiveness and continuously improve, still a crafty social engineer can weasel his way…
Read MoreThe content of this post is solely the responsibility of the author. LevelBlue does not adopt or endorse any of the views, positions, or information provided by the author in this article. As a high school student interested in exploring the connection between technology and nature, I was curious to find out how the natural…
Read MoreSecurity flaws in Telit Cinterion cellular modems, widely used in sectors including industrial, healthcare, and telecommunications, could allow remote attackers to execute arbitrary code via SMS. A set of eight separate issues, seven of them with identifiers CVE-2023-47610 through CVE-2023-47616 and another that has yet to be registered, were disclosed last November by security researchers…
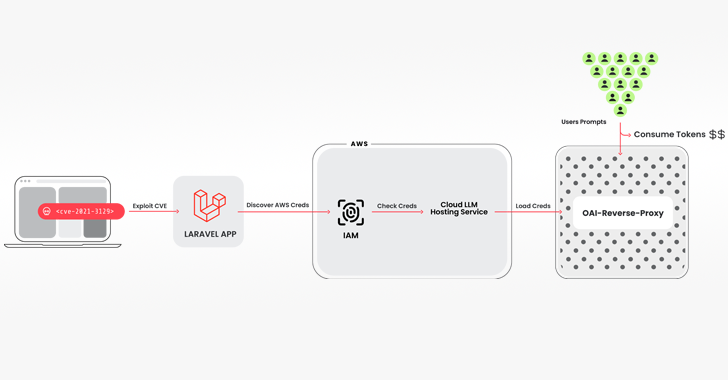
Read MoreMay 10, 2024NewsroomVulnerability / Cloud Security Cybersecurity researchers have discovered a novel attack that employs stolen cloud credentials to target cloud-hosted large language model (LLM) services with the goal of selling access to other threat actors. The attack technique has been codenamed LLMjacking by the Sysdig Threat Research Team. “Once initial access was obtained, they…
Read MoreGoogle has released a security update for the Chrome browser to fix the fifth zero-day vulnerability exploited in the wild since the start of the year. The high-severity issue tracked as CVE-2024-4671 is a “user after free” vulnerability in the Visuals component that handles the rendering and display of content on the browser. CVE-2024-4671 was…
Read More