Month: May 2024
A summary of the NCSC’s security analysis for the UK telecoms sector Source link lol
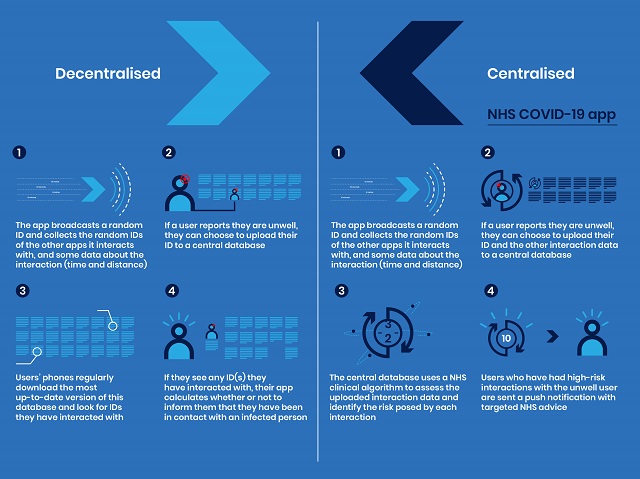
Read MoreNCSC technical paper about the privacy and security design of the NHS contact tracing app developed to help slow the spread of coronavirus. Source link lol
Read MoreThe Government of British Columbia is investigating multiple “cybersecurity incidents” that have impacted the Canadian province’s government networks. Premier David Eby said in a Wednesday statement that there is no evidence that the attackers had accessed or stolen sensitive information from the compromised networks. However, an ongoing investigation is assessing the incidents’ impact and looking…
Read MoreCVE-2024-21793, CVE-2024-26026: Proof of Concept Available for F5 BIG-IP Next Central Manager Vulnerabilities
by nlqip
Researchers disclose multiple vulnerabilities in F5 BIG-IP Next Central Manager and provide proof-of-concept exploit code, which could lead to exposure of hashed passwords. Background On May 8, F5 published advisories for two vulnerabilities in the BIG-IP Next Central Manager, a centralized management console for BIG-IP Next instances. CVE Description CVSSv3 CVE-2024-21793 BIG-IP Next Central Manager…
Read MoreA summary of the NCSC’s analysis of the May 2020 US sanction which caused the NCSC to modify the scope of its security mitigation strategy for Huawei. Source link lol
Read MoreFrom Amazon Q and SageMaker to customer buying trends in 2024, Amazon CEO Andy Jassy explains why AI has already generated “a multibillion-dollar revenue run rate” for his company. Amazon CEO Andy Jassy is bullish that Amazon Web Services’ artificial intelligence push will take the company to new heights in 2024 thanks to several key…
Read MoreThe NCSC report highlights the cyber threats faced by the sports sector and suggests how to stop or lessen their impact on organisations. Source link lol
Read More‘Upon identifying the incident, we promptly implemented our incident response procedures, began investigating, took steps to contain the incident and notified law enforcement,’ said Dell in an email to customers. ‘We have also engaged a third-party forensics firm to investigate this incident.’ Dell Technologies is investigating a security “incident” involving a portal that contains a…
Read MoreHow Criminals Are Using Generative AI There’s a new report on how criminals are using generative AI tools: Key Takeaways: Adoption rates of AI technologies among criminals lag behind the rates of their industry counterparts because of the evolving nature of cybercrime. Compared to last year, criminals seem to have abandoned any attempt at training…
Read MoreThe second report examining how the NCSC’s ACD programme is improving the security of the UK public sector and the wider UK cyber ecosystem. Source link lol
Read MoreRecent Posts
- CISA Releases the Cybersecurity Performance Goals Adoption Report | CISA
- Multiple vulnerabilities in SonicWall SonicOS could allow a remote attacker to bypass authentication.
- Dell Sales Leader, Former Channel Chief John Byrne Steps Down
- The Dangers of DNS Hijacking
- CES 2025: 15 PC Chips Announced By Intel, Nvidia, AMD And Qualcomm