Month: May 2024
Donna, can you build on that and talk about how you provide clarity for 11,000 teammates, especially in the area of cybersecurity? Hart: Human error and phishing are still the major cyber risks to a corporation. Ransomware is our No. 1 threat, and it really is stemming from a team member clicking on the wrong…
Read MoreThe 2nd joint report between the NCSC and KPMG UK benchmarks against the 2020 findings to gauge what progress has been made. Source link lol
Read MoreJoint report between the NCSC and KPMG UK is the first in a series to benchmark and track levels of diversity and inclusion in the cyber security industry. Source link lol
Read MoreMay 09, 2024NewsroomNetwork Security / Botnet Two recently disclosed security flaws in Ivanti Connect Secure (ICS) devices are being exploited to deploy the infamous Mirai botnet. That’s according to findings from Juniper Threat Labs, which said the vulnerabilities CVE-2023-46805 and CVE-2024-21887 have been leveraged to deliver the botnet payload. While CVE-2023-46805 is an authentication bypass…
Read MoreMay 09, 2024The Hacker NewsvCISO / Regulatory Compliance Cybersecurity and compliance guidance are in high demand among SMEs. However, many of them cannot afford to hire a full-time CISO. A vCISO can answer this need by offering on-demand access to top-tier cybersecurity expertise. This is also an opportunity for MSPs and MSSPs to grow their…
Read More“We regularly see attempted attacks and rumors circulating, but it is crucial to rely only on official communications from Zscaler itself to get factual updates and information,” the employee had said. The rumors started after the notorious Serbian threat actor named IntelBroker offered to sell access to a cybersecurity company with a revenue of $1.8…
Read MoreCancer patients’ sensitive information accessed by “unidentified parties” after being left exposed by screening lab for years
by nlqip
A medical lab that specialises in cancer screenings has admitted to an alarming data breach that left sensitive patient information exposed for years – and accessible by unauthorised parties. California-based Guardant Health is notifying affected individuals that information related to samples collected in late 2019 and 2020 was “inadvertently” left exposed online to the general…
Read MoreCybersecurity analysts point out that we are seeing a departure from traditional approaches. Traditional cybersecurity solutions have been limited to either time-driven or point-driven security, noted Faisal Kawooza, chief analyst at Techarc. This means they could only defend against cyberthreats that their systems had already recognized, understood, and formulated defenses against. “As we see the…
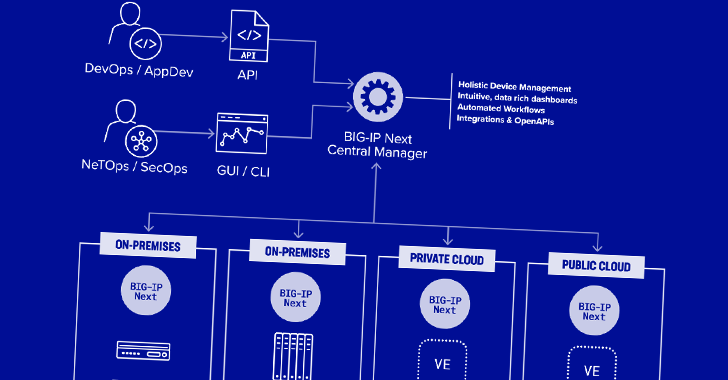
Read MoreMay 09, 2024NewsroomFirewall / Network Security Two security vulnerabilities have been discovered in F5 Next Central Manager that could be exploited by a threat actor to seize control of the devices and create hidden rogue administrator accounts for persistence. The remotely exploitable flaws “can give attackers full administrative control of the device, and subsequently allow…
Read MoreUpdate 5/8/24: Out original article was updated to include new information about a breached “test” environment. Zscaler says that they discovered an exposed “test environment” that was taken offline for analysis after rumors circulated that a threat actor was selling access to the company’s systems. In a Wednesday afternoon post, Zscaler initially stated that its ongoing…
Read MoreRecent Posts
- Fake AI video generators infect Windows, macOS with infostealers
- T-Mobile confirms it was hacked in recent wave of telecom breaches
- GitHub projects targeted with malicious commits to frame researcher
- NSO Group used another WhatsApp zero-day after being sued, court docs say
- Ingram Micro’s Sahoo: ‘Don’t React To AI.’ Act On AI’