Ticketmaster confirms massive breach after stolen data for sale online
by nlqip

Live Nation has confirmed that Ticketmaster suffered a data breach after its data was stolen from a third-party cloud database provider, which is believed to be Snowflake.
“On May 20, 2024, Live Nation Entertainment, Inc. (the “Company” or “we”) identified unauthorized activity within a third-party cloud database environment containing Company data (primarily from its Ticketmaster LLC subsidiary) and launched an investigation with industry-leading forensic investigators to understand what happened,” Live Nation shared in a Friday night SEC filing.
“On May 27, 2024, a criminal threat actor offered what it alleged to be Company user data for sale via the dark web.”
“We are working to mitigate risk to our users and the Company, and have notified and are cooperating with law enforcement. As appropriate, we are also notifying regulatory authorities and users with respect to unauthorized access to personal information.”
While the breach has allegedly exposed the data of over 560 million Ticketmaster users, the company states that they do not believe that the breach will have a material impact on the overall business operations or its financial condition.
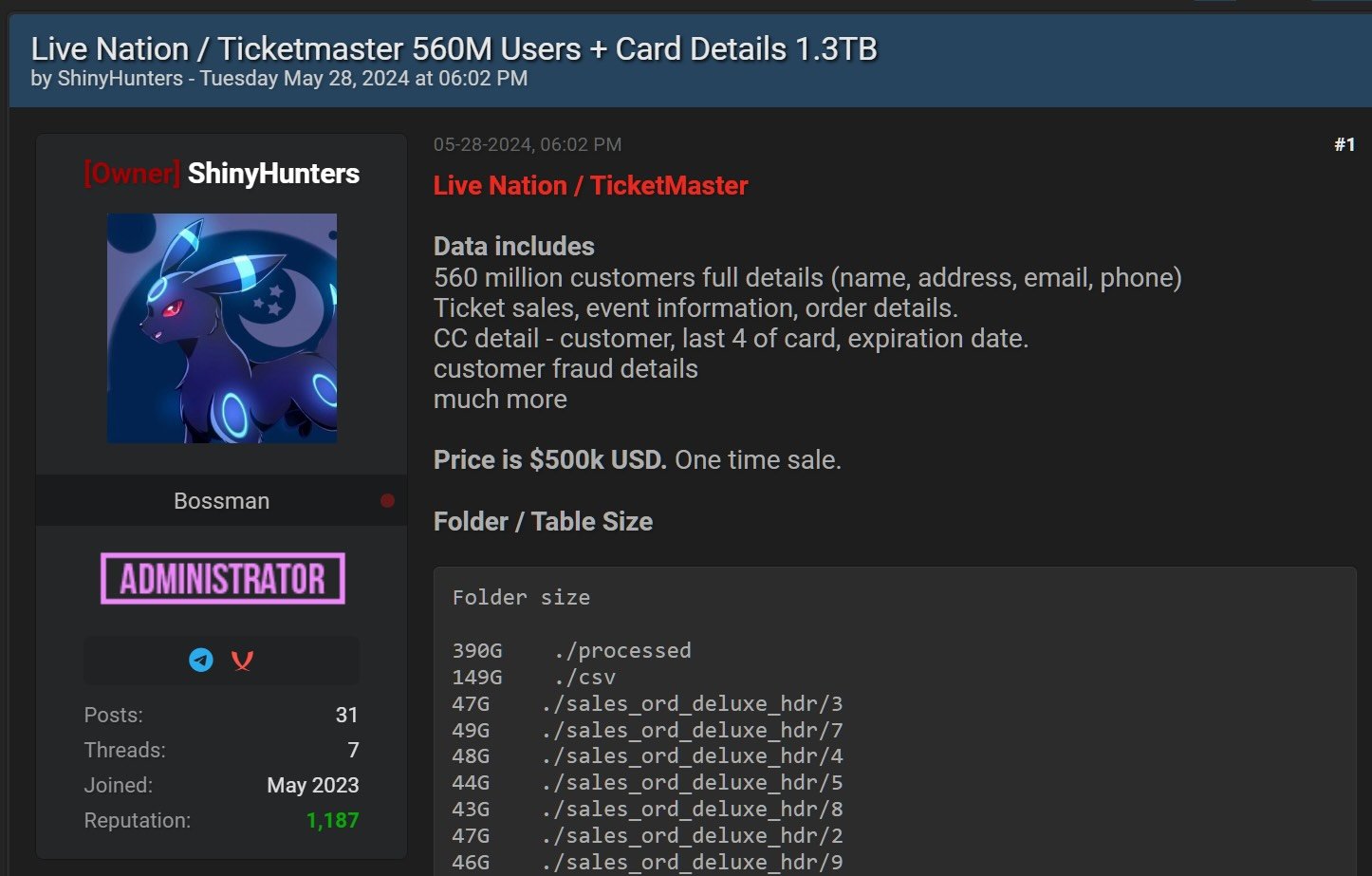
This admission comes after a threat actor known as Shiny Hunters has been attempting to sell the Ticketmaster data on a hacking forum for $500,000.
The allegedly stolen databases supposedly contain 1.3TB of data, including customers’ full details (i.e., names, home and email addresses, and phone numbers), as well as ticket sales, order, and event information for 560 million customers.
Source: BleepingComputer
In a conversation with the threat actor, ShinyHunters told BleepingComputer that there were interested buyers in the data. They believed that one of the buyers that approached them was Ticketmaster themselves.
When asked how they stole the data, the threat actor said they “can’t say anything about this.”
However, today, more information was revealed on how the threat actors gained access to the Ticketmaster database and possibly the data of many other customers.
Alon Gal of Hudson Rock spoke to one of the threat actors behind the attack, who claimed they were responsible for recent Santander and Ticketmaster data breaches and said they stole the data from cloud storage company Snowflake.
According to the threat actor, they used credentials stolen using information-stealing malware to breach a Snowflake employee’s ServiceNow account, which they used to exfiltrate information from the company. This information included unexpired auth tokens that could be used to create session tokens and access customer accounts to download data.
The threat actor claims that they used this method to steal data from other companies, including Anheuser-Busch, State Farm, Mitsubishi, Progressive, Neiman Marcus, Allstate, and Advance Auto Parts.
Progressive and Mistubishi disputed the threat actor’s claims, telling BleepingComputer that there is no indication of any breach of their systems or data.
Snowflake says the recent breaches were caused by poorly secured customer accounts whose credentials were stolen and did not have multi-factor authentication enabled.
The company added that the attacks began in mid-April, with customers’ data first being stolen on May 23. Snowflake has shared IOCs from the attacks so that customers can query logs to determine if they were breached.
Mandiant Consulting CTO Charles Carmakal told BleepingComputer that Mandiant has been investigating compromised Snowflake clients over the past few weeks and believes their Snowflake tenants were breached using stolen credentials.
When we contacted Snowflake to confirm the threat actor’s claims that they hacked an employee’s account, instead of disputing them, they said they had nothing further to share.
This is a developing story.
Source link
lol
Live Nation has confirmed that Ticketmaster suffered a data breach after its data was stolen from a third-party cloud database provider, which is believed to be Snowflake. “On May 20, 2024, Live Nation Entertainment, Inc. (the “Company” or “we”) identified unauthorized activity within a third-party cloud database environment containing Company data (primarily from its Ticketmaster…
Recent Posts
- A Vulnerability in Apache Struts2 Could Allow for Remote Code Execution
- CISA Adds One Known Exploited Vulnerability to Catalog | CISA
- Xerox To Buy Lexmark For $1.5B In Blockbuster Print Deal
- Vulnerability Summary for the Week of December 16, 2024 | CISA
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
