Chinese hacking groups team up in cyber espionage campaign
by nlqip

Chinese state-sponsored actors have been targeting a government agency since at least March 2023 in a cyberespionage campaign that researchers track as Crimson Palace.
According to a report from cybersecurity company Sophos, the campaign relied on new malware variants and three different activity clusters that indicate a coordinated attack.
While initial access could not be determined, the researchers observed related activity dating to early 2022 that used the custom Nupakage malware previously associated with the Chinese threat group Mustang Panda.
Three activity clusters
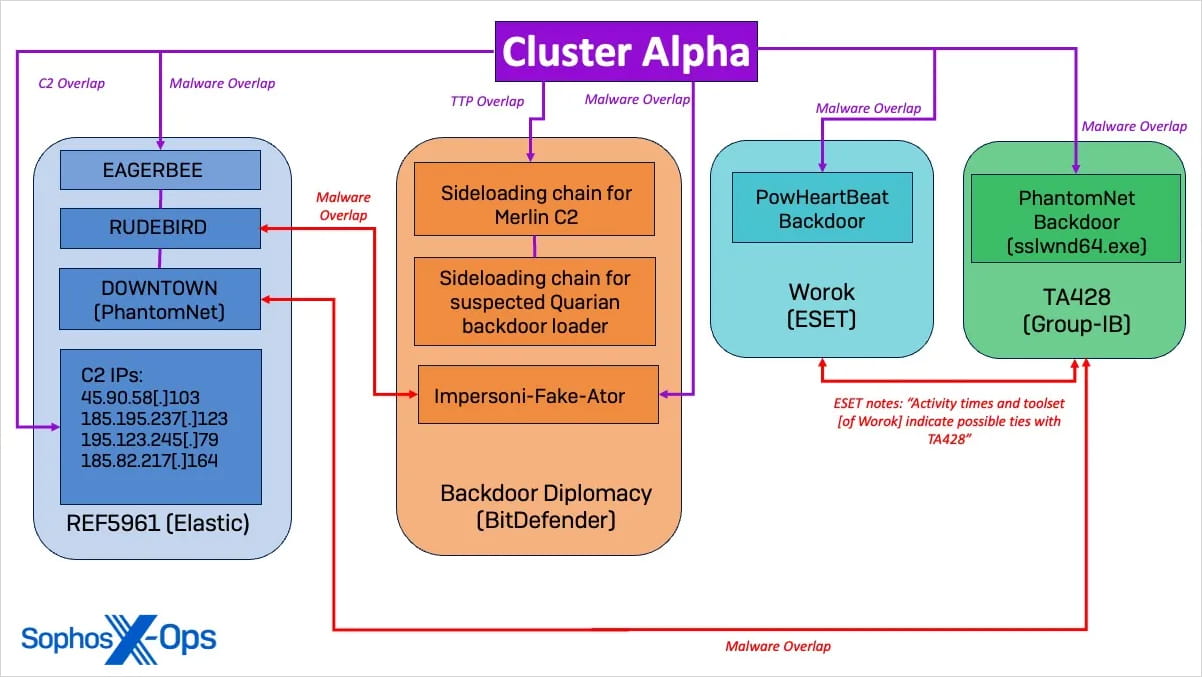
Sophos identified three activity clusters connected to known Chinese threat groups like “BackdoorDiplomacy,” “REF5961,” “Worok,” “TA428,” and the APT41 subgroup Earth Longzhi.
The analysts assessed with high confidence that the operation of those clusters is centrally coordinated under a single organization.
Source: Sophos
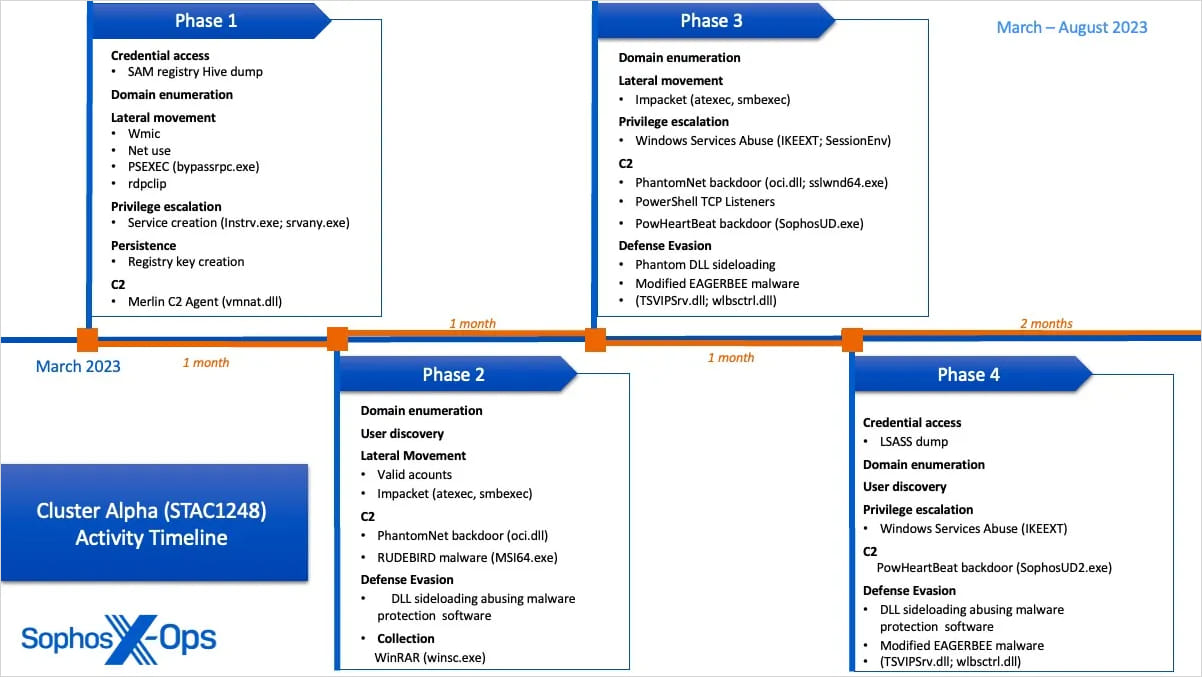
Cluster Alpha (STAC1248): active from early March to August 2023, it focused on deploying updated ‘EAGERBEE’ malware variants capable of disrupting security agency network communications.
The main goal was to map server subnets and enumerate administrator accounts by conducting reconnaissance on Active Directory infrastructure.
The activity relied on multiple persistent command and control (C2) channels, including Merlin Agent, PhantomNet backdoor, RUDEBIRD malware, and PowHeartBeat backdoor.
To evade detection, the threat actor employed living-off-the-land binaries (LOLBins) for service persistence with elevated SYSTEM privileges, and conducted DLL side-loading with eight unique DLLs, exploiting Windows Services and legitimate Microsoft binaries.
Source: Sophos
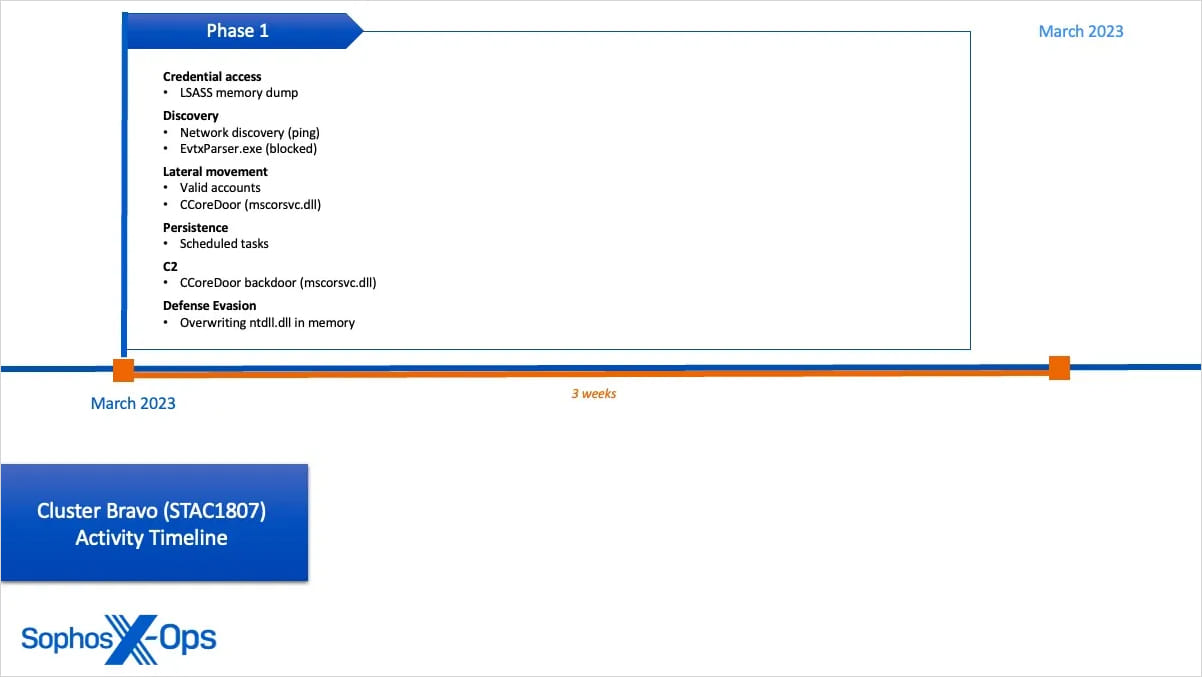
Cluster Bravo (STAC1807): active for only three weeks in March 2023, it focused on lateral movement and persistence, dropping a previously unknown backdoor named ‘CCoreDoor’ onto the target systems. The backdoor established external C2 communications, performed discovery, and dumped credentials.
The actor used renamed versions of signed side-loadable binaries to obfuscate the backdoor deployment and facilitate lateral movement while also overwriting ntdll.dll in memory to unhook the Sophos endpoint protection agent process from the kernel.
Source: Sophos
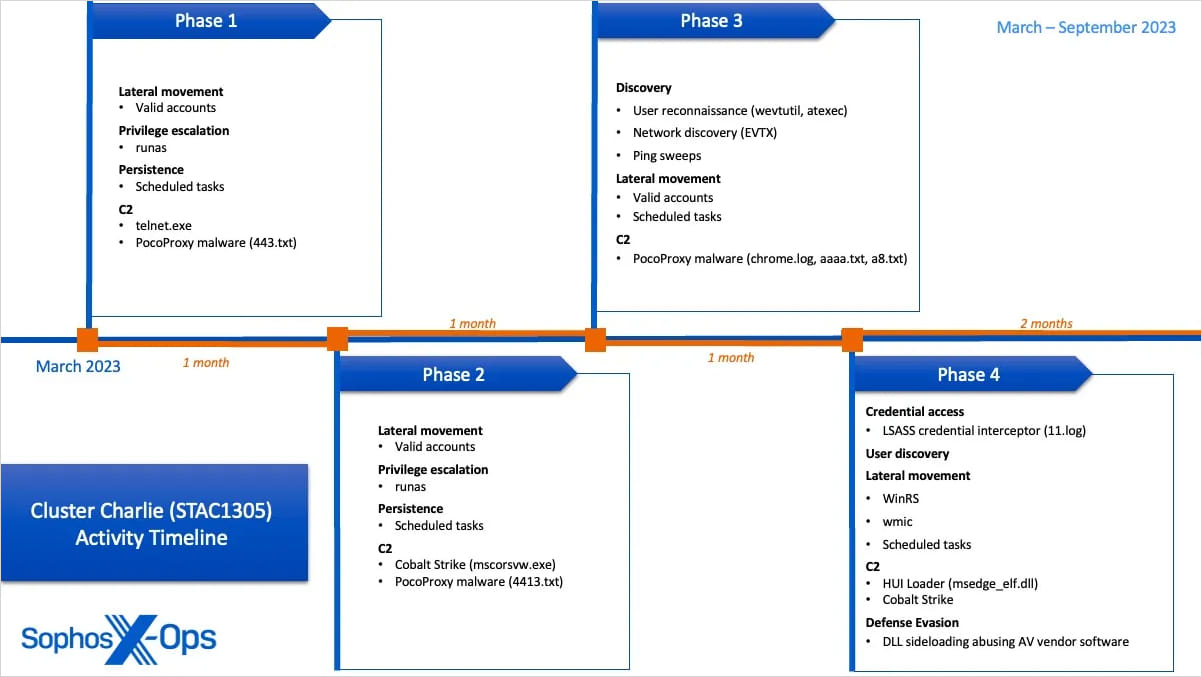
Cluster Charlie (SCAT1305): active from March 2023 to at least April 2024, it engaged in persistent access management and extensive reconnaissance over an extended period.
The actor deployed multiple samples of a previously unidentified malware called ‘PocoProxy,’ used for persistent C2 communications. They also used the HUI loader to inject a Cobalt Strike Beacon into mstsc.exe, though these attempts were blocked.
Additionally, the threat actor injected an LSASS login credential interceptor to capture credentials on domain controllers and conducted a mass analysis of Event Logs and automated ping sweeps to map users and endpoints across the network.
Source: Sophos
The Crimson Palace campaign targeted an agency of a Southeast Asian government for cyberespionage purposes.
“We assess with moderate confidence that multiple distinct Chinese state-sponsored actors have been active in this high-profile Southeast Asian government organization since at least March 2022,” explains Sophos.
“Though we are currently unable to perform high-confidence attribution or confirm the nature of the relationship between these clusters, our current investigation suggests that the clusters reflect the work of separate actors tasked by a central authority with parallel objectives in pursuit of Chinese state interests” – Sophos
Overall, the three clusters operated during standard Chinese work hours (08:00 AM to 05:00 PM CST), breaking the period into three chunks that don’t overlap, which indicates a high level of coordination.
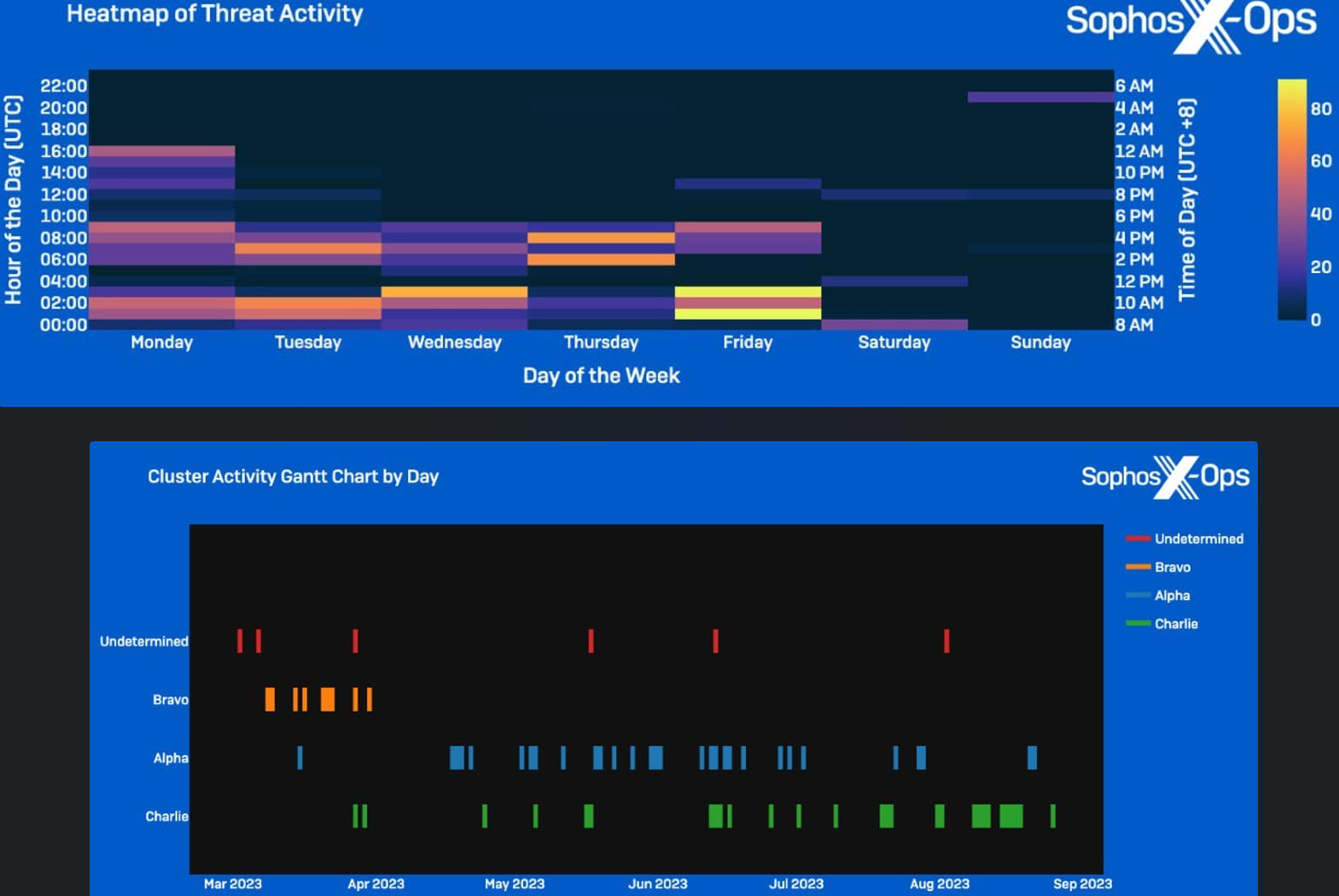
Source: Sophos
Sophos found that malicious activity spiked in some cases, like on June 12, 2023, which was a holiday in the target country. This was likely to catch defenders understaffed and carry out activity at a time when systems were not as closely monitored.
Due to lack of visibility, Sophos could not determine the initial access but assesses that the threat actor had access to the network since at least March 2022, based on a detection of the Nupakage malware that is typically used to exfiltrate data.
High-confidence attribution or confirming the relation between the three clusters is difficult, Sophos researchers believe that the detected activity represents “the work of separate actors tasked by a central authority with parallel objectives in pursuit of Chinese state interests.”
Although Sophos has blocked the threat actor’s C2 implants in August 2023 and Cluster Alpha activity has not been seen since, the researchers say that Cluster Charlie activity was observed after a few weeks of silence and the adversary tried to breach the network and resume operations “at a higher tempo and in a more evasive manner.”
Sophos continues to monitor the intrusion activity in the target network.
Source link
lol
Chinese state-sponsored actors have been targeting a government agency since at least March 2023 in a cyberespionage campaign that researchers track as Crimson Palace. According to a report from cybersecurity company Sophos, the campaign relied on new malware variants and three different activity clusters that indicate a coordinated attack. While initial access could not be determined,…
Recent Posts
- Arm To Seek Retrial In Qualcomm Case After Mixed Verdict
- Jury Sides With Qualcomm Over Arm In Case Related To Snapdragon X PC Chips
- Equinix Makes Dell AI Factory With Nvidia Available Through Partners
- AMD’s EPYC CPU Boss Seeks To Push Into SMB, Midmarket With Partners
- Fortinet Releases Security Updates for FortiManager | CISA
